crypto
-
 Read more: Mobile Hacking Lab – IOT Connect
Read more: Mobile Hacking Lab – IOT ConnectDescription: Welcome to the “IOT Connect” Broadcast Receiver Exploitation Challenge! Immerse yourself in the world of cybersecurity with this hands-on lab. This challenge focuses on exploiting a security flaw related to the broadcast receiver in the “IOT Connect” application, allowing unauthorized users to activate the master switch, which can turn on all connected devices. The goal is…
-
 Read more: Mobile Hacking Lab – Strings
Read more: Mobile Hacking Lab – StringsDescription: Welcome to the Strings Challenge! In this lab,your goal is to find the flag. The flag’s format should be “MHL{…}“. The challenge will give you a clear idea of how intents and intent filters work on android also you will get a hands-on experience using Frida APIs. Download: https://lautarovculic.com/my_files/strings-MHL.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-strings Install the app with ADB adb install -r strings-MHL.apk…
-
 Read more: PwnSec CTF 2024 – FireInTheHole
Read more: PwnSec CTF 2024 – FireInTheHoleDescription: Great job, Mark! You encrypted the files, inserted them into the mobile application, and then forgot how to decrypt them. Seriously? Now, we have to figure out your mess. Well done! And by the way… YOU’RE FIRED!Download content: https://lautarovculic.com/my_files/fire-in-the-hole.zip Install the apk with ADB adb install -r FireInTheHole.apk We can see some wallpaper screen.Let’s check the source code with jadx (GUI version)But…
-
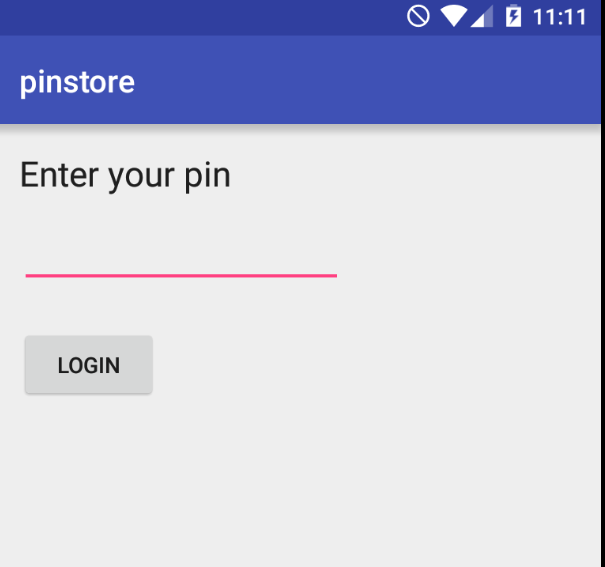 Read more: BSides San Francisco CTF 2017 – pinlock
Read more: BSides San Francisco CTF 2017 – pinlockDescription: It’s the developer’s first mobile application. They are trying their hand at storing secrets securely. Could one of them be the flag?Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/pinstore.apk Install the apk with adb adb install -r pinstore.apk Then, decompile with apktool apktool d pinstore.apk Notice…
-
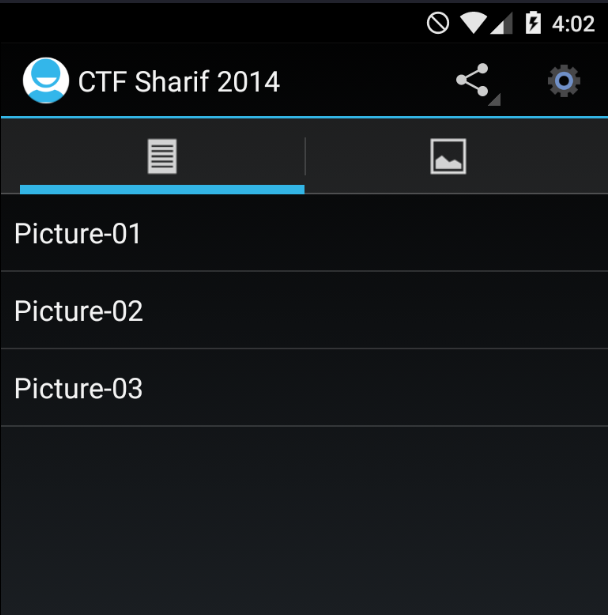 Read more: Sharif University Quals CTF 2014 – Commercial Application
Read more: Sharif University Quals CTF 2014 – Commercial ApplicationCategory: CryptoDescription: Flag is a serial number. Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/suCTF.apk Install the apk with adb adb install -r suCTF.apk Decompile this with apktool apktool d suCTF.apk And now we can inspect the source code with jadxBut, first at all, let’s take a look to the…
-
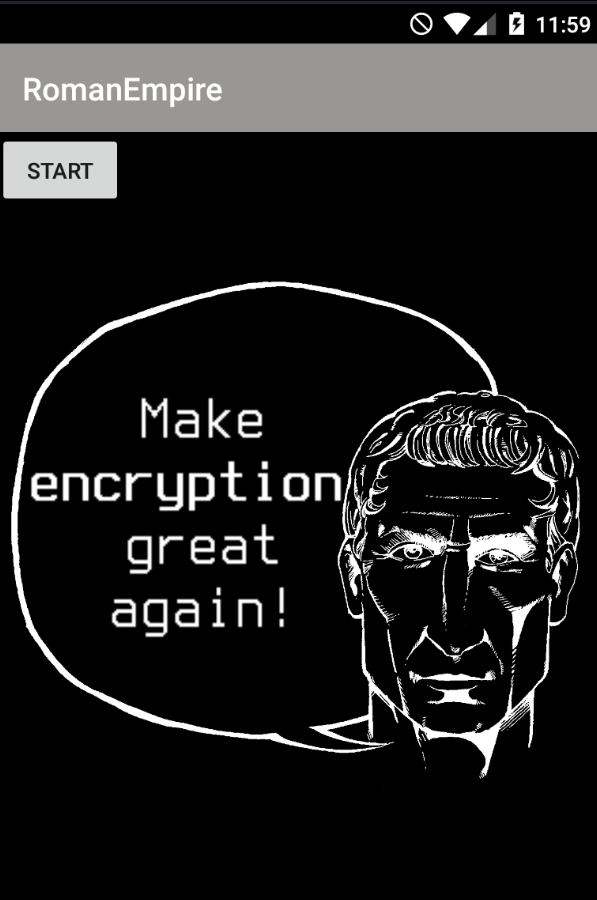 Read more: AHE17: Android Hacking Events 2017 (You Can Hide – But You Cannot Run)
Read more: AHE17: Android Hacking Events 2017 (You Can Hide – But You Cannot Run)For this challenge, probably we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APKhttps://team-sik.org/wp-content/uploads/2017/06/YouCanHideButYouCannotRun.apk_.zip Use apktool for decompile the .apk file apktool d YouCanHideButYouCannotRun.apk And install the .apk with adb adb install -r YouCanHideButYouCannotRun.apk Launching the app we can see that we have a text that talk about encryption and a button. That say Start to Running if we press it. Let’s load the .apk to jadx for…
-
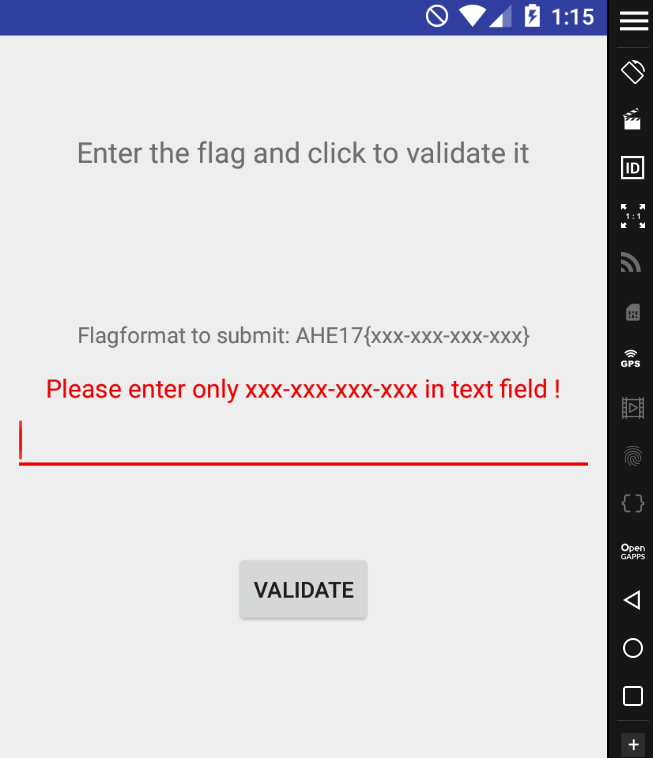 Read more: AHE17: Android Hacking Events 2017 (Flag-Validator)
Read more: AHE17: Android Hacking Events 2017 (Flag-Validator)Methods For this challenge, probably we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APKhttps://team-sik.org/wp-content/uploads/2017/06/FlagValidator.apk_.zip With apktool will extract the content of the apk file apktool d FlagValidator.apk Let’s see the content of MainActivity.java that say so clear the structure of the flag.In the onValidateClick method public void onValidateClick(View view) { new StringBuilder(“Validate Token…
-
 Read more: AHE17: Android Hacking Events 2017 (AES-Decrypt)
Read more: AHE17: Android Hacking Events 2017 (AES-Decrypt)For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APK https://team-sik.org/wp-content/uploads/2017/06/AES-Decrypt.apk_.zip Now, installing the APK, we can see a button and two text box for decrypt something. Then, let’s take around the code with jadx. Just we need this piece of Java…
-
 Read more: Hack The Box – Cryptohorrific – @lautarovculic
Read more: Hack The Box – Cryptohorrific – @lautarovculicDifficult: Medium Category: Mobile OS: iOS Description: Secure coding is the keystone of the application security! After downloading the compressed file and decompressing it, we will have a folder where inside we find the files we need: The hackthebox file, is the main file of the program that contains the binary files. The .plist file…
-
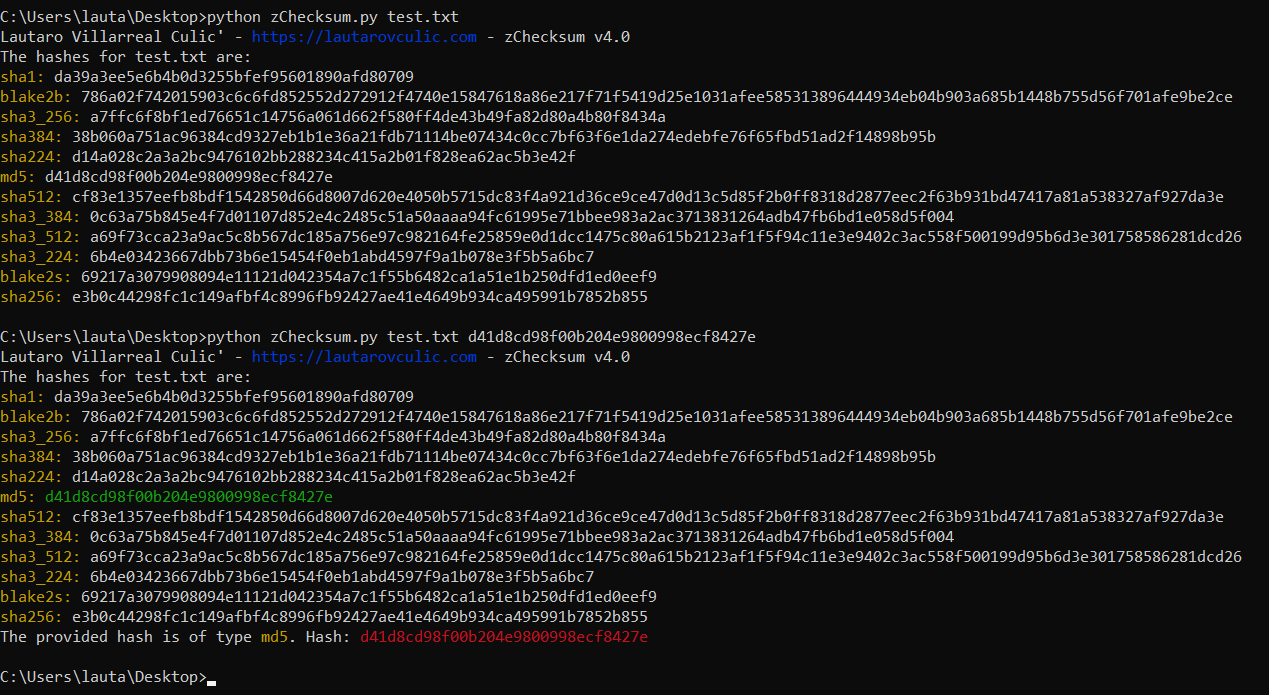 Read more: zChecksum
Read more: zChecksumTool to obtain and compare hashes. Python >= 3.9 pip install hashlib pip install colorama Usage python zChecksum.py <file_name> python zChecksum.py <file_name> [hash] The [hash] arg is optional. This hash will compare the hashes that were obtained from the <file_name>. Code # Lautaro Daniel Villarreal Culic’ # https://lautarovculic.com # ver 4.0 # REQUIRE…