cracking
-
 Read more: Protected: Alert – Hack The Box – @lautarovculic
Read more: Protected: Alert – Hack The Box – @lautarovculicThere is no excerpt because this is a protected post.
-
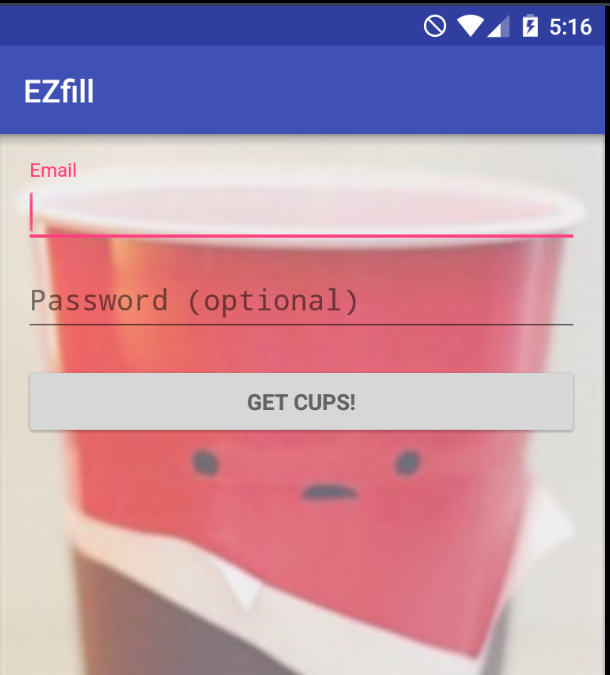 Read more: LabyREnth CTF 2016 – 2 – Cups
Read more: LabyREnth CTF 2016 – 2 – CupsNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/3778e43f21797bb383108182fe200a928be8605ff5b078aaf4feac02850b91f4Password: infected After extract the file, we get the .apkInstall it with adb adb install -r ezFill.apk We can see a login activitySo, for understand what the app do, we need decompile it. apktool d ezFill.apk And open the apk file with jadx (GUI version) We have just one activity…
-
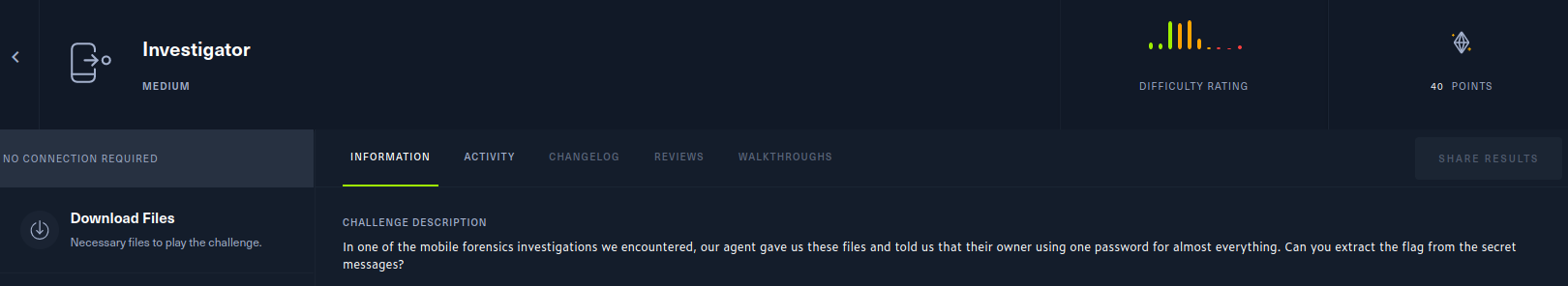 Read more: Investigator – Hack The Box – @lautarovculic
Read more: Investigator – Hack The Box – @lautarovculicDifficult: Medium Category: Mobile OS: Android Description: In one of the mobile forensics investigations we encountered, our agent gave us these files and told us that their owner using one password for almost everything. Can you extract the flag from the secret messages? Download the .zip file and extract the content with the hackthebox password.…
-
 Read more: SolarLab – Hack The Box – @lautarovculic
Read more: SolarLab – Hack The Box – @lautarovculicUser.txt First we need know what’s ports are up. sudo nmap -sS -sV -n -Pn -vv 10.10.11.16 Output PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack ttl 127 nginx 1.24.0 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? syn-ack ttl 127…
-
 Read more: Mailing – Hack The Box – @lautarovculic
Read more: Mailing – Hack The Box – @lautarovculicUser.txt Let’s discover the open ports with nmap sudo nmap -sS -sV –min-rate 5000 -n -Pn -T4 -vv 10.10.11.14 Output PORT STATE SERVICE REASON VERSION 25/tcp open smtp syn-ack ttl 127 hMailServer smtpd 80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) 110/tcp open pop3 syn-ack ttl 127 hMailServer pop3d 135/tcp open msrpc…
-
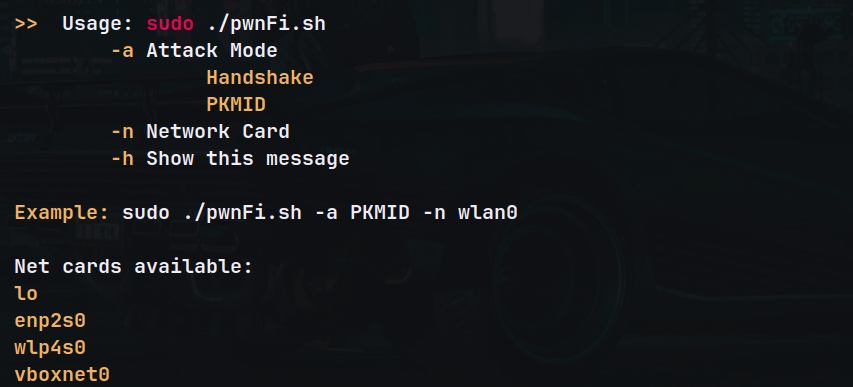 Read more: pwnFi
Read more: pwnFiSimple Wi-Fi cracking automation. GitHub Description This Bash script is designed for performing Wi-Fi penetration testing attacks, specifically targeting WPA/WPA2 networks using PSK (Pre-Shared Key). It supports two attack modes: Handshake and PKMID attack. The script automates various steps including setting up monitor mode, capturing handshakes or PKMID messages, deauthentication, and cracking passwords using Aircrack-ng…
-
 Read more: Runner – Hack The Box – @lautarovculic
Read more: Runner – Hack The Box – @lautarovculicUser.txt First we will discover the open ports with nmap sudo nmap -sS -sU –min-rate 5000 -n -Pn -T4 -vv 10.10.11.13 Output: PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu) 8000/tcp open nagios-nsca syn-ack ttl…
-
 Read more: Usage – Hack The Box – @lautarovculic
Read more: Usage – Hack The Box – @lautarovculicUser.txt Will discover open ports with nmap sudo nmap -sS -sV –min-rate 5000 -n -Pn -T4 -vv 10.10.11.18 Output PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu) Inspectin the webserver in the port 80, we…
-
 Read more: IClean – Hack The Box – @lautarovculic
Read more: IClean – Hack The Box – @lautarovculicUser.txt First, we will discover which ports are open. sudo nmap -sS –min-rate 5000 -n -Pn -T4 -vv -sV 10.10.11.12 Output: PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 ((Ubuntu)) If we go to clean.htb…
-
 Read more: Codify – Hack The Box – @lautarovculic
Read more: Codify – Hack The Box – @lautarovculicUser.txt Add the machine IP to /etc/hosts file Now it’s nmap time sudo nmap -sS –min-rate 5000 -n -Pn -T4 -vv 10.10.11.239 PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 3000/tcp open http syn-ack ttl…