writeup
-
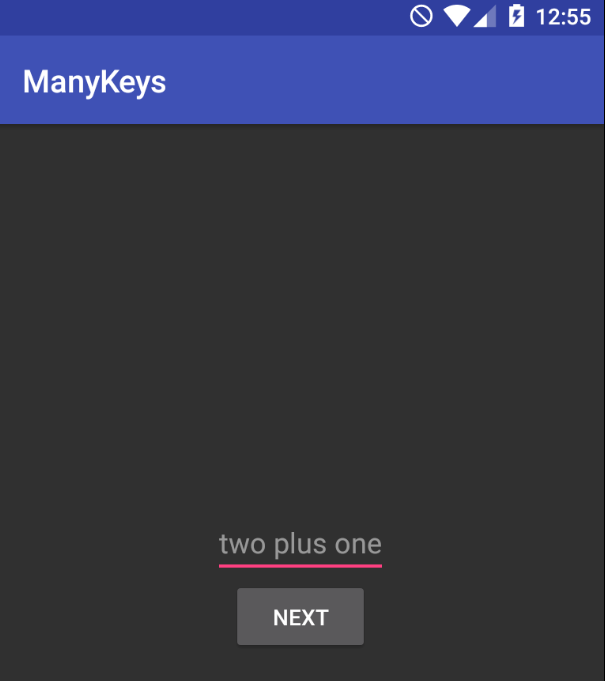 Read more: LabyREnth CTF 2017 – 1 – EzDroid
Read more: LabyREnth CTF 2017 – 1 – EzDroidNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/EzDroid.apk Install the apk with adb adb install -r EzDroid.apk The app doesn’t launch, even if we start the activity with adb adb shell am start -n com.labyrenth.manykeys.manykeys/.EZMain So, let’s decompile it with apktool apktool d EzDroid.apk And let’s inspect the source…
-
 Read more: BSides San Francisco CTF 2017 – flag-receiver
Read more: BSides San Francisco CTF 2017 – flag-receiverDescription: Here is a simple mobile application that will hand you the flag.. if you ask for it the right way.P.S, it is meant to have a blank landing activity 🙂 Use string starting with Flag:Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/flagstore.apk…
-
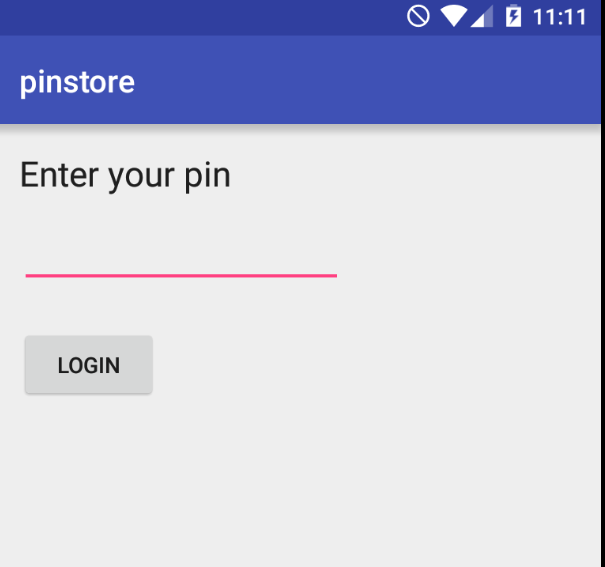 Read more: BSides San Francisco CTF 2017 – pinlock
Read more: BSides San Francisco CTF 2017 – pinlockDescription: It’s the developer’s first mobile application. They are trying their hand at storing secrets securely. Could one of them be the flag?Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/pinstore.apk Install the apk with adb adb install -r pinstore.apk Then, decompile with apktool apktool d pinstore.apk Notice…
-
 Read more: LabyREnth CTF 2016 – 4 – Swip3r
Read more: LabyREnth CTF 2016 – 4 – Swip3rNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/c6acf741819c9632cffd12aec0b61aa0dcee0b9f262ccc24262fd8458512c85cPassword: infected Install the apk with adb adb install -r Swip3r.apk Then, decompile this with apktool apktool d Swip3r.apk The app crashes when we press the button give me the child.Let’s inspect the source code with jadx. There are two java classes.Pay attention, the MainActivity (Home) is Swip3r, no MainActivity.You…
-
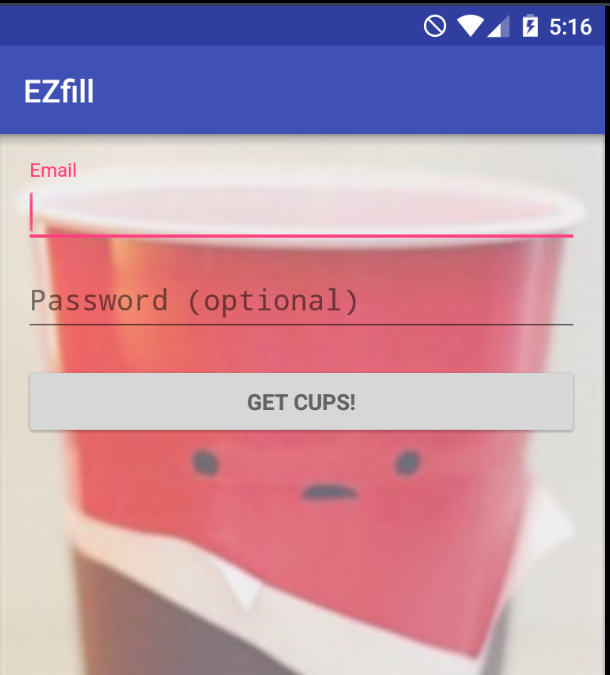 Read more: LabyREnth CTF 2016 – 2 – Cups
Read more: LabyREnth CTF 2016 – 2 – CupsNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/3778e43f21797bb383108182fe200a928be8605ff5b078aaf4feac02850b91f4Password: infected After extract the file, we get the .apkInstall it with adb adb install -r ezFill.apk We can see a login activitySo, for understand what the app do, we need decompile it. apktool d ezFill.apk And open the apk file with jadx (GUI version) We have just one activity…
-
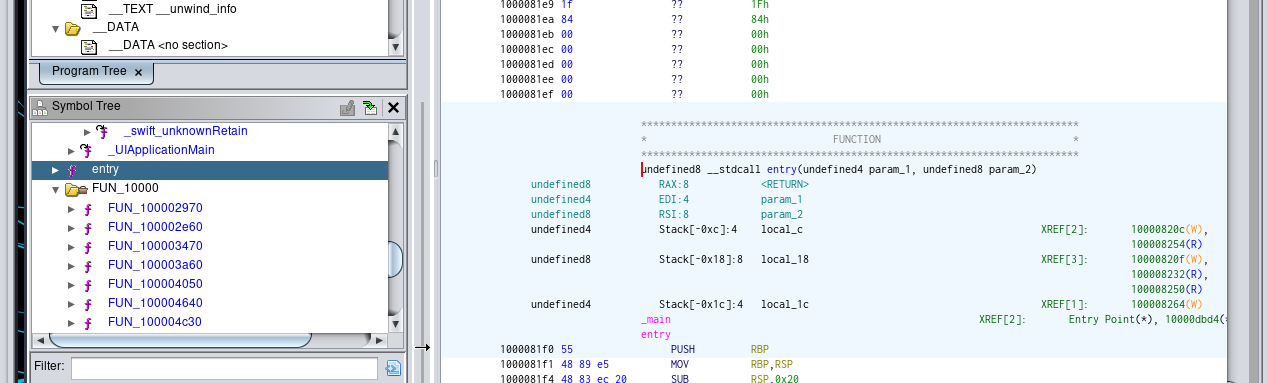 Read more: LabyREnth CTF 2016 – 1 – LastChance
Read more: LabyREnth CTF 2016 – 1 – LastChanceDownload IPA: https://lautarovculic.com/my_files/fbfe8ecef4b5f97c40687fd02f74ae009277538490fba314e61830d75b3b4ac5Password: infected When you extract the file, we’ll have the .ipa file, and the LastChance_Simulator.app folder.Inside of this folder we have the LastChance executable. file LastChance LastChance: Mach-O 64-bit x86_64 executable, flags We can use ghidra for inspect this binary.After load, we have the entry point. But, we can search for some functions or hardcoded strings.I found some interesting strings. Let’s found where is used.Taking…
-
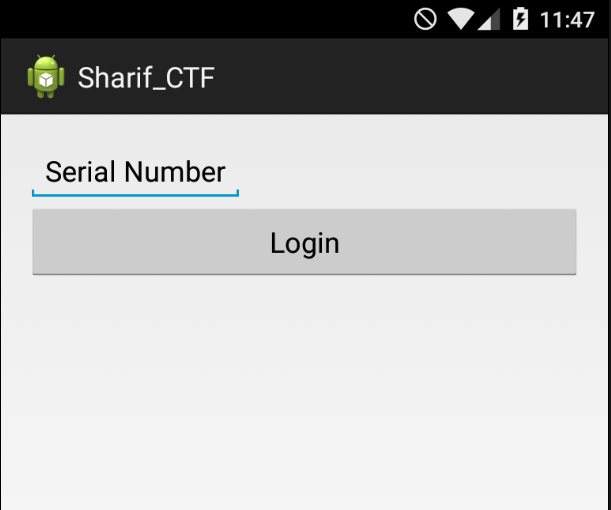 Read more: Sharif University CTF 2016 – Android App
Read more: Sharif University CTF 2016 – Android AppDescription: Find the Flag!!Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/Sharif_CTF.apk Install the apk with adb adb install -r Sharif_CTF.apk Then, decompile with apktool apktool d Sharif_CTF.apk We can see an input that need a serial number for login.Let’s inspect the source code with jadx (GUI Version)The package name is com.example.ctf2 Here’s the MainActivity java code public class MainActivity extends…
-
 Read more: Google CTF 2016 – Ill Intentions
Read more: Google CTF 2016 – Ill IntentionsNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/illintentions.apk Install the apk with adb adb install -r illintentions.apk adb install -r illintentions.apk apktool d illintentions.apk And let’s check the source code with jadx (GUI version)We can see that the package name is com.example.hellojni So, after read the code some minutes, we have the MainActivity public…
-
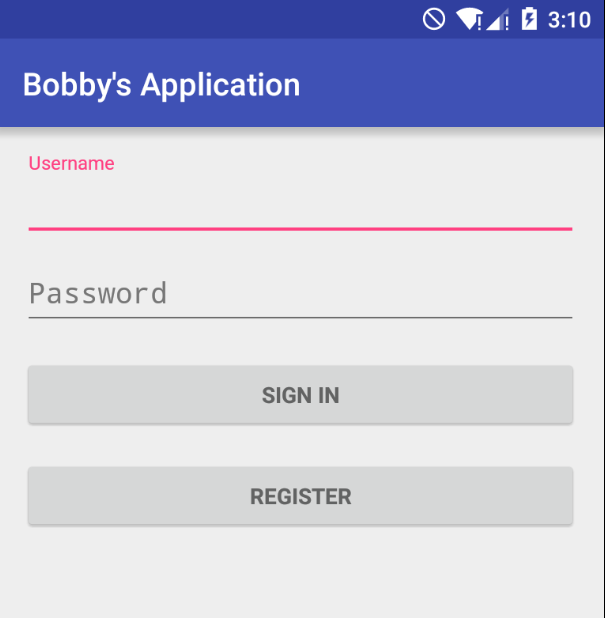 Read more: Google CTF 2016 – Little Bobby application
Read more: Google CTF 2016 – Little Bobby applicationNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/BobbyApplication_CTF.apk Install the apk with adb adb install -r BobbyApplication_CTF.apk We can see a login form. Let’s decompile the content with apktool. apktool d BobbyApplication_CTF.apk And let’s check the source code with jadx (GUI version)We can conclude that the package name is bobbytables.ctf.myapplication After create an user “asd” for…
-
 Read more: IceCTF 2015 – Husavik
Read more: IceCTF 2015 – HusavikDescription: This handy Android App is supposed to display the flag, but it’s not working!Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/husavik.apk Install the apk with adb adb install -r husavik.apk Then, decompile it with apktool apktool d husavik.apk We can see inspecting the source code with jadx (GUI version)That in…