Writeups
CTF Writeups
-
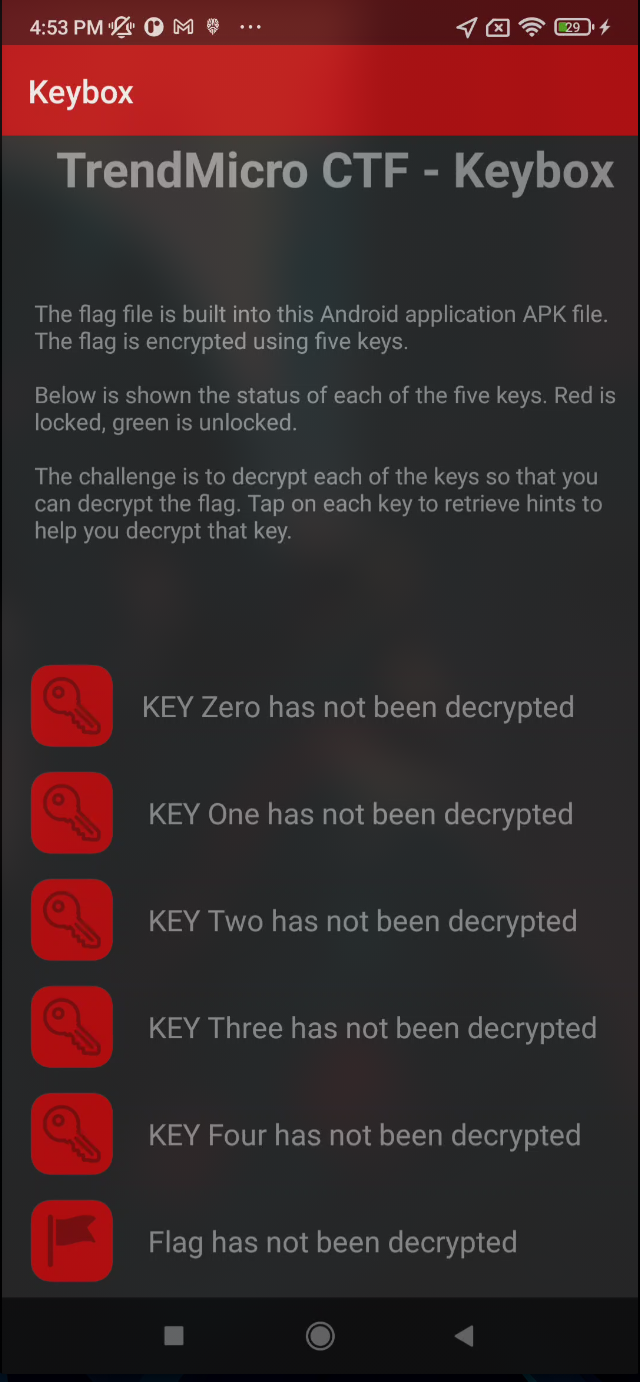 Read more: Trend Micro CTF 2020 – Keybox
Read more: Trend Micro CTF 2020 – KeyboxDescription: The flag file is built into this Android application APK file.The flag is encrypted using five keys.Below is shown the status of each of the five keys. Red is locked, green is unlocked.The challenge is to decrypt each of these keys so that you can decrypt the flag. Tap on each key to retrieve…
-
 Read more: Mobile Hacking Lab – Captain Nohook
Read more: Mobile Hacking Lab – Captain NohookDescription: Welcome to the iOS Application Security Lab: Captain No Hook Anti-Debugging Challenge. This challenge focuses on a fictitious app called Captain No Hook, which implements advanced anti-debugging / jailbreak detection techniques. Your objective is to bypass these protections and retrieve the hidden flag within the app. Download: https://lautarovculic.com/my_files/noHook.ipaLink: https://www.mobilehackinglab.com/path-player?courseid=lab-captain-nohook Final Steps Install an IPA file can be difficult.So, for…
-
 Read more: Mobile Hacking Lab – Run Time
Read more: Mobile Hacking Lab – Run TimeDescription: Welcome to the iOS Application Security Lab: Dynamic Library Injection Challenge. This challenge focuses on a fictitious app called Run Time , which tracks the steps while running. Your objective is to bypass the app’s protections, deliver the exploit and gain code execution utilizing the dynamic library injection. Download: https://lautarovculic.com/my_files/runtime.ipaLink: https://www.mobilehackinglab.com/path-player?courseid=lab-runtime Install an IPA file can be difficult.So, for…
-
 Read more: Mobile Hacking Lab – No Escape
Read more: Mobile Hacking Lab – No EscapeDescription: Welcome to the iOS Application Security Lab: Jailbreak Detection Evasion Challenge. The challenge centers around a fictitious app called No Escape, designed with robust jailbreak detection mechanisms. Your mission is to bypass these mechanisms and gain full access to the app’s functionalities using Frida. Download: https://lautarovculic.com/my_files/noEscape.ipaLink: https://www.mobilehackinglab.com/path-player?courseid=lab-no-escape Install an IPA file can be difficult.So, for make it more easy,…
-
 Read more: Mobile Hacking Lab – Serial Notes
Read more: Mobile Hacking Lab – Serial NotesDescription: Welcome to the iOS Application Security Lab: Deserialization Vulnerability Challenge. The challenge revolves around a fictitious note-taking app called Serial Notes. Serial Notes is designed to support markdown editing and has its own file format to share the notes. However, it harbors a critical vulnerability related to deserialization, which can be escalated to command injection.…
-
 Read more: Mobile Hacking Lab – Freshcart
Read more: Mobile Hacking Lab – FreshcartDescription: Welcome to the iOS Application Security Lab: JavaScript-to-Native Bridge Exploitation Challenge. This challenge is centered around a fictitious grocery app called Freshcart. Freshcart contains a critical vulnerability that allows token stealing by exploiting the JavaScript to native bridge. Your objective is to exploit this vulnerability to steal the token used within the app. Download: https://lautarovculic.com/my_files/freshcart.ipaLink: https://www.mobilehackinglab.com/path-player?courseid=lab-freshcart Install…
-
 Read more: Mobile Hacking Lab – Time Trap
Read more: Mobile Hacking Lab – Time TrapDescription: Welcome to the Time Trap Challenge. In this challenge, you will explore the vulnerabilities in an internally used application named Time Trap, focusing on Command Injection. Time Trap is a fictional application that showcases insecure practices commonly found in internal applications. Your objective is to exploit the Command Injection vulnerability to gain unauthorized access and…
-
 Read more: Mobile Hacking Lab – Gotham Times
Read more: Mobile Hacking Lab – Gotham TimesDescription: Welcome to the iOS Application Security Lab: Deeplink Exploitation Challenge. The challenge is built around the fictional newspaper Gotham Times, an iOS application providing users with the latest news and updates about events happening in Gotham City. This challenge focuses on the potential vulnerabilities in the deep link feature, emphasizing how attackers can exploit it…
-
 Read more: Mobile Hacking Lab – Flipcoin Wallet
Read more: Mobile Hacking Lab – Flipcoin WalletDescription: Welcome to the iOS Application Security Lab: SQL Injection Challenge. The challenge is centered around a fictious crypto currency flipcoin and its wallet Flipcoin Wallet. The Flipcoin wallet is an offline wallet giving users full ownership of their digital assets. The challenge highlights the potential entrypoints that can lead to further serious vulnerabilities including…
-
 Read more: Mobile Hacking Lab – NoteKeeper
Read more: Mobile Hacking Lab – NoteKeeperDescription: Welcome to the NoteKeeper Application, where users can create and encode short notes. However, lurking within the app is a critical buffer overflow vulnerability. Your mission is to uncover this vulnerability and exploit it to achieve remote code execution. Download: https://lautarovculic.com/my_files/notekeeper.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-notekeeper Install the app with ADB adb install -r notekeeper.apk We can see how this notes app allows…