Writeups
CTF Writeups
-
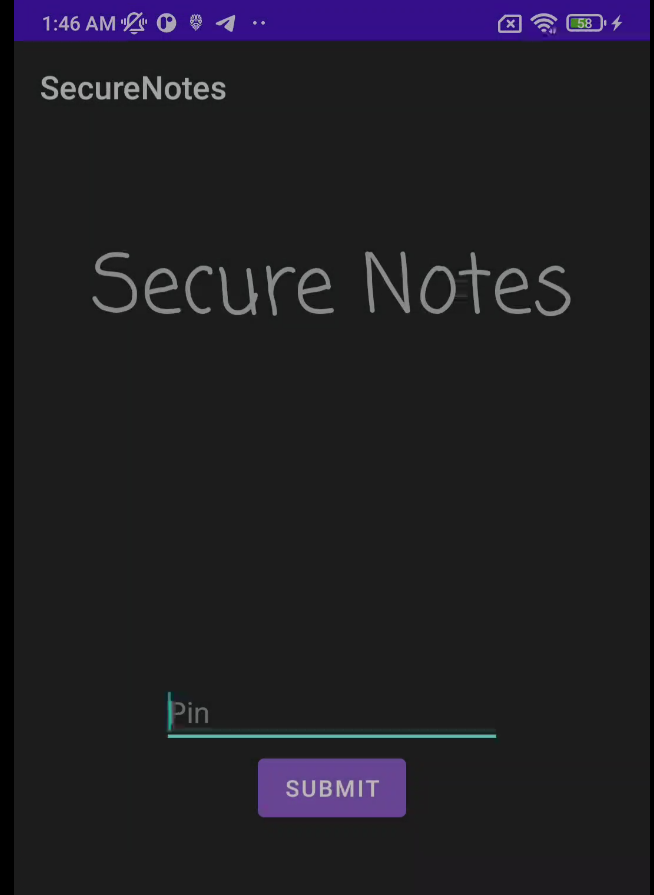 Read more: NahamCon CTF 2022 – Secure Notes
Read more: NahamCon CTF 2022 – Secure NotesDescription: None of the free note taking app offer encryption… So I made my own! Download: https://lautarovculic.com/my_files/secure_notes.apk Install the APK file with ADB adb install -r secure_notes.apk We can see that we need insert a 4-Digit PIN.If we insert any number, we get the Wrong password message. Let’s inspect the source code using jadx.The package name is com.congon4tor.securenotes. We have two activities in AndroidManifest.xml file: LoginActivity -> MainActivity also?¿?¿ -> PIN Screen MainActivity ->…
-
 Read more: NahamCon CTF 2022 – Mobilize
Read more: NahamCon CTF 2022 – MobilizeDescription: Autobots. ROLLL OUTT!!!!!! Download: https://lautarovculic.com/my_files/mobilize.apk Install the APK file with ADB adb install -r mobilize.apk This app doesn’t nothing haha. Just, extract the app with jadx or just unzip.Inside of res/values/strings.xml you can find the flag. Or just unzip mobilize.apk && strings resources.arsc | grep flag Flag: flag{e2e7fd4a43e93ea679d38561fa982682} I hope you found it useful (:
-
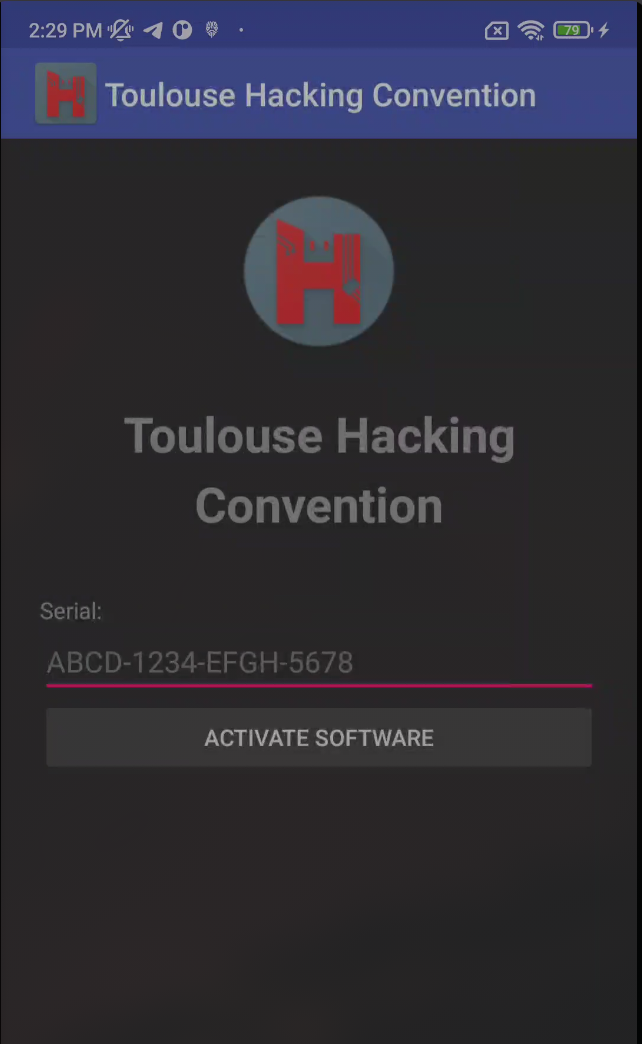 Read more: THC CTF 2018 – Android serial
Read more: THC CTF 2018 – Android serialDescription: A paid android app for THC began to be developed, unfortunately its development stalled. In the end, it was never possible to buy this app, but be the first to unlock the app’s premium features by finding a valid key. Download: https://lautarovculic.com/my_files/THC.apk Install the APK file with ADB adb install -r THC.apk We can see that we have…
-
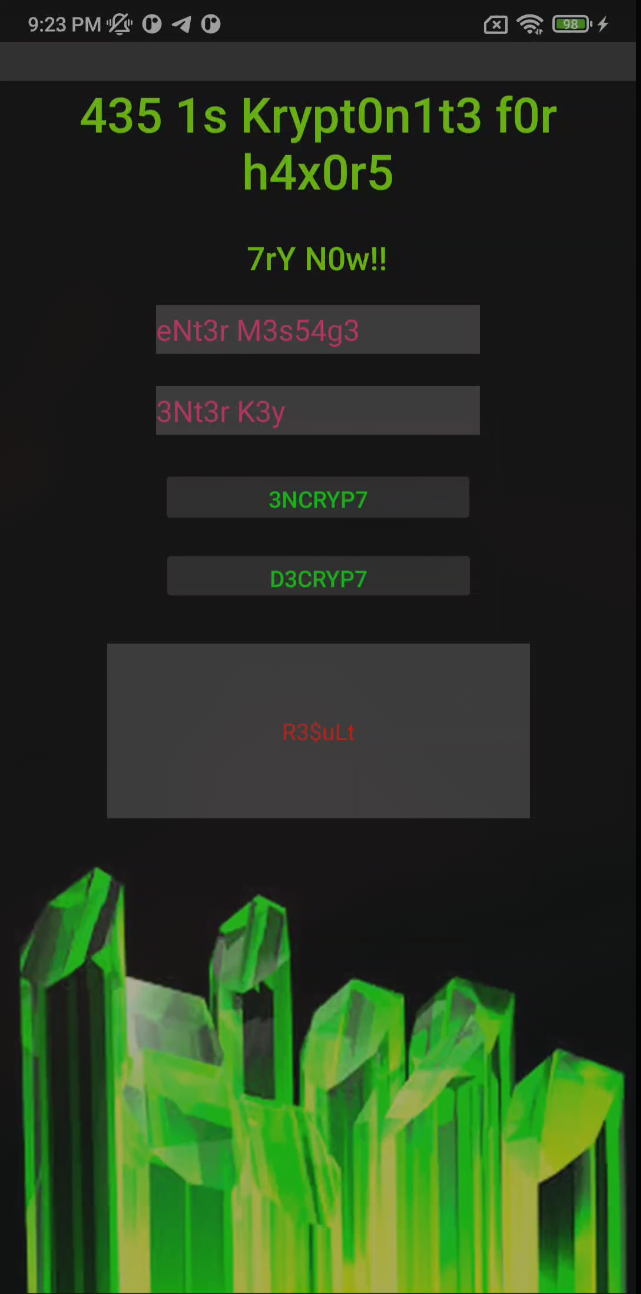 Read more: Mystiko – Kryptonite
Read more: Mystiko – KryptoniteCategory: CryptoDescription: This challenge intends to show how to enumerate android apps in search for hidden information. Download APK: https://lautarovculic.com/my_files/kryptonite.apk Install the APK file with ADB adb install -r krypto.apk We can see that we have an encrypt/decrypt message app.The text is in leet speak.And the title says: AES is kryptonite for haxors Notice that, trying the length of the key randomly, I see the correct…
-
 Read more: NahamCon CTF 2021 – Andra & Resourceful
Read more: NahamCon CTF 2021 – Andra & ResourcefulAndra Description: You know what to do. 🙂Download: https://lautarovculic.com/my_files/andra.apk Install the APK file using ADB adb install andra.apk We can see a simple login activity.Let’s inspect the source code with jadx. We can see the credentials of this login in the MainActivity class: final String str = “Nahamcom”; final String str2 = “pink_panther@786”; Username: nahamcomPassword: pink_panther@786 Then, the com.example.hack_the_app.flag activity will be showed with the flag. Flag: flag{d9f72316dbe7ceab0db10bed1a738482 Resourceful Description: I…
-
 Read more: NahamCon CTF 2020 – Candroid & Simple App
Read more: NahamCon CTF 2020 – Candroid & Simple AppCandroid Description: I think I can, I think I can!Download: https://lautarovculic.com/my_files/candroid.apk Install the APK file with ADB adb install -r candroid.apk Decompile the application with apktool apktool d candroid.apk The app name is “Nahamcon1“If we insert any text as password, a message will prompt saying:Error: Reading the password file Notice that a password.txt file is created in the external directory: File file =…
-
 Read more: Hacktivitycon 2021 – To Do & Reactor
Read more: Hacktivitycon 2021 – To Do & ReactorChallenges To Do Description: I made my own app to remind me of all the things I need to do.Download: https://lautarovculic.com/my_files/todo.apk Install the APK file with ADB adb install -r todo.apk Let’s inspect the source code with jadx.Meanwhile, we can see that we have an password text field, if we insert any char, we get the message “Wrong password“. Looking…
-
 Read more: Google CTF 2020 – Sandbox
Read more: Google CTF 2020 – SandboxDownload: https://lautarovculic.com/my_files/google2020reverse.apk Install the APK with ADB adb install -r google2020reverse.apk Let’s inspect the source code with jadx.We can see that jadx doesn’t work.So move to dex2jar tool. d2j-dex2jar google2020reverse.apk The MainActivity is called ő.The code is malformed, that why we can’t decompile the code and then, read it. The constructor and onCreate() are obfuscated with invalid try/catch (such as catch I, which is invalid because int is not a Throwable).…
-
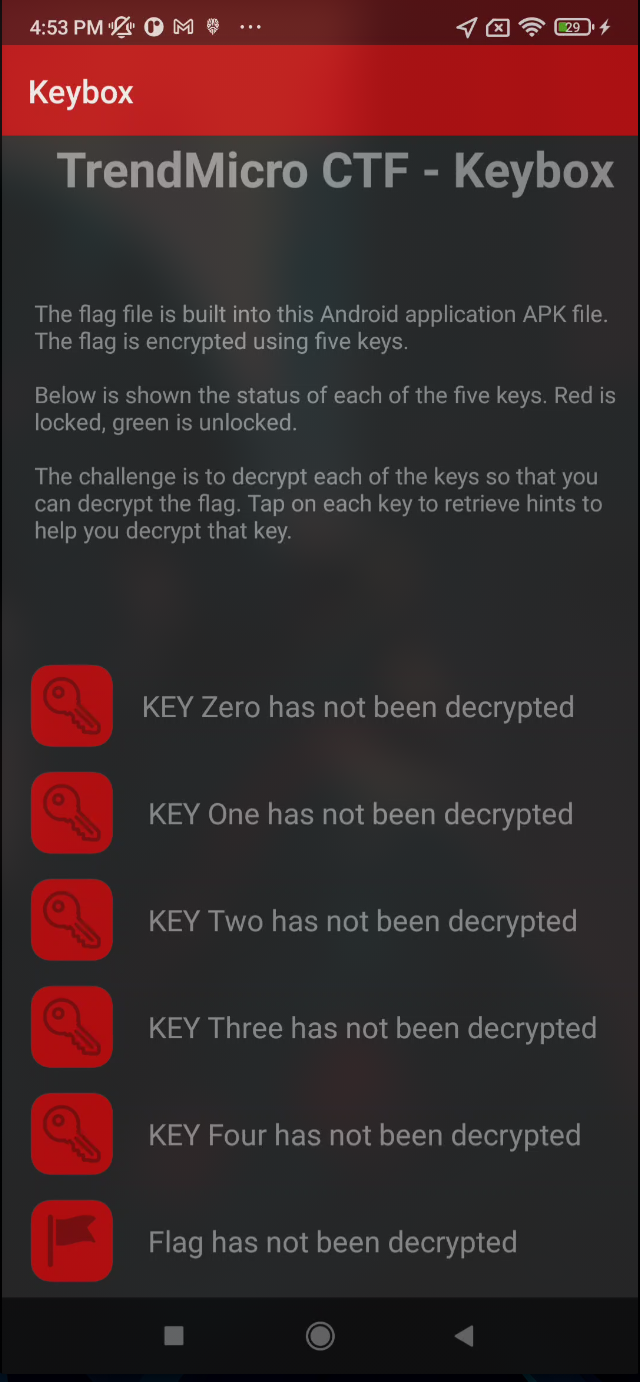 Read more: Trend Micro CTF 2020 – Keybox
Read more: Trend Micro CTF 2020 – KeyboxDescription: The flag file is built into this Android application APK file.The flag is encrypted using five keys.Below is shown the status of each of the five keys. Red is locked, green is unlocked.The challenge is to decrypt each of these keys so that you can decrypt the flag. Tap on each key to retrieve…
-
 Read more: Mobile Hacking Lab – Captain Nohook
Read more: Mobile Hacking Lab – Captain NohookDescription: Welcome to the iOS Application Security Lab: Captain No Hook Anti-Debugging Challenge. This challenge focuses on a fictitious app called Captain No Hook, which implements advanced anti-debugging / jailbreak detection techniques. Your objective is to bypass these protections and retrieve the hidden flag within the app. Download: https://lautarovculic.com/my_files/noHook.ipaLink: https://www.mobilehackinglab.com/path-player?courseid=lab-captain-nohook Final Steps Install an IPA file can be difficult.So, for…