Writeups
CTF Writeups
-
 Read more: Mobile Hacking Lab – TokenBleed
Read more: Mobile Hacking Lab – TokenBleedDescription: This challenge is centered around a fictitious Crypto exchange app, highlighting a critical security flaw related to an insecure web view implementation which can lead to exfiltration of sensitive data and 1-click account takeover. Link: https://www.mobilehackinglab.com/course/lab-tokenbleed Install the .apk file using ADB adb install -r mhl-lab-tokenbleed.apk We can see a typical Exchange application (very well designed graphically).However, I noticed that…
-
 Read more: CyberSecurityRumble CTF – Exterminate
Read more: CyberSecurityRumble CTF – ExterminateDescription: Daleks have invaded the earth and the Doctor is nowhere to be seen. Now it’s up to you to find out how they are built and which code can stop the extermination of all humankind. Download: https://lautarovculic.com/my_files/exterminate.apk Install the .apk file using ADB adb install -r exterminate.apk We can see that when the app is launched, there are…
-
 Read more: WonderSMS – Hack The Box – @lautarovculic
Read more: WonderSMS – Hack The Box – @lautarovculicDifficult: HardCategory: MobileOS: Android Description: My grandmother just got stolen! Someone drained her bank account! I didn’t even know this was possible, with so many security layers and tokens and stuff nowadays! Anyway, I need your help! You’re the only hacker I know! I took a look at her phone and the only thing that struck…
-
 Read more: Jigsaw – Hack The Box – @lautarovculic
Read more: Jigsaw – Hack The Box – @lautarovculicDifficult: EasyCategory: MobileOS: Android Description: A secret lies hidden, protected by layers of logic and scattered clues. Your task is to uncover these fragments, piece them together, and solve the mystery. It’s a challenge of patience, creativity, and determination. Can you reveal the secret? Install the APK file using ADB adb install -r Jigsaw.apk We can see a login activity.Let’s decompile…
-
 Read more: BYUCTF 2025 – Baby Android 1 & 2
Read more: BYUCTF 2025 – Baby Android 1 & 2Baby Android 1 Description: If you’ve never reverse engineered an Android application, now is the time!! Get to it, already!! Learn how they work!!Download: https://lautarovculic.com/my_files/baby-android-1.apk Install the APK file using ADB adb install -r baby-android-1.apk We can see a message when the app is launched: Too slow!! So, let’s analyze the source code with jadx.We can see the MainActivity class: package byuctf.downwiththefrench; import android.os.Bundle; import…
-
 Read more: Pedometer – Hack The Box – @lautarovculic
Read more: Pedometer – Hack The Box – @lautarovculicDifficult: HardCategory: MobileOS: Android Description: I’ve been using this pedometer app for weeks, and I am convinced it’s using me as a power supply for some hidden machine. I bet it holds the key or a map to some sort of treasure. If only I could figure out what it’s doing… Download the .zip file and extract this…
-
 Read more: DroidPhish (Sherlock) – Hack The Box
Read more: DroidPhish (Sherlock) – Hack The BoxDescription: Last night, most employees’ mobile devices were compromised, putting them at significant risk of leaking personal and private information. We require your expertise in digital forensics to help investigate this breach.Difficulty: EasyCategory: Mobile / Forensics Download the .zip file and extract with the password: hacktheblue file DroidPhish.dd Output: DroidPhish.dd: Linux rev 1.0 ext4 filesystem data, UUID=e98cc545-b7fe-4ba9-8b33-2fb9bba476d6, volume…
-
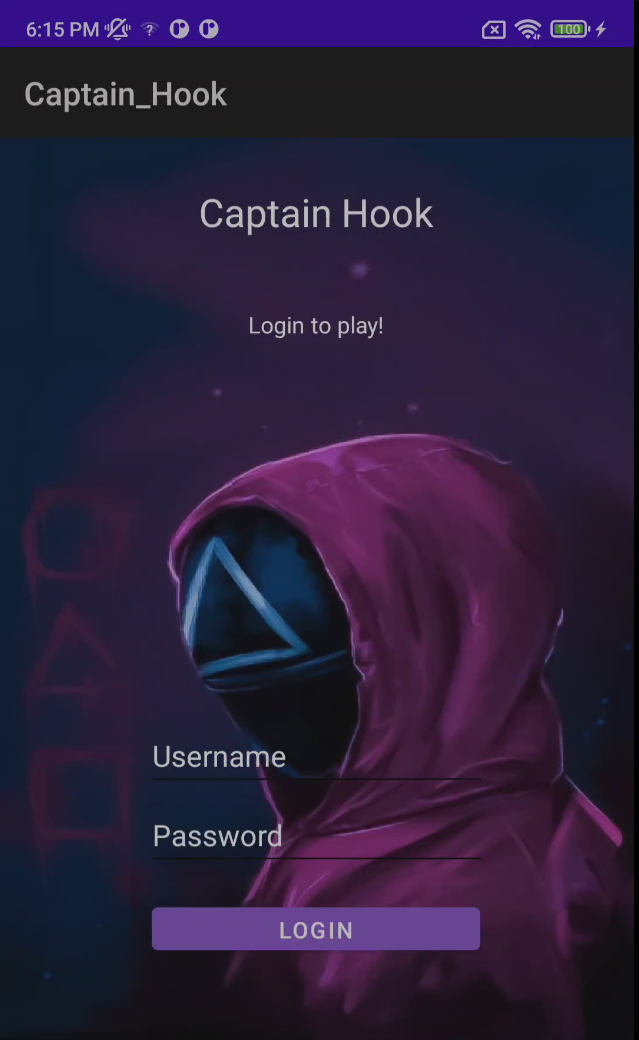 Read more: UniWA 2022 – CaptainHook
Read more: UniWA 2022 – CaptainHookDescription: Captain Hook has applied for a position in Squid Game 2022, but in order to take part into the game, he got asked to bypass the login screen of this app. Help him bypass it and he wont have the crocodile eat your hand. Download: https://lautarovculic.com/my_files/Captain_Hook.apk Install the APK file with ADB adb install -r Captain_Hook.apk We can…
-
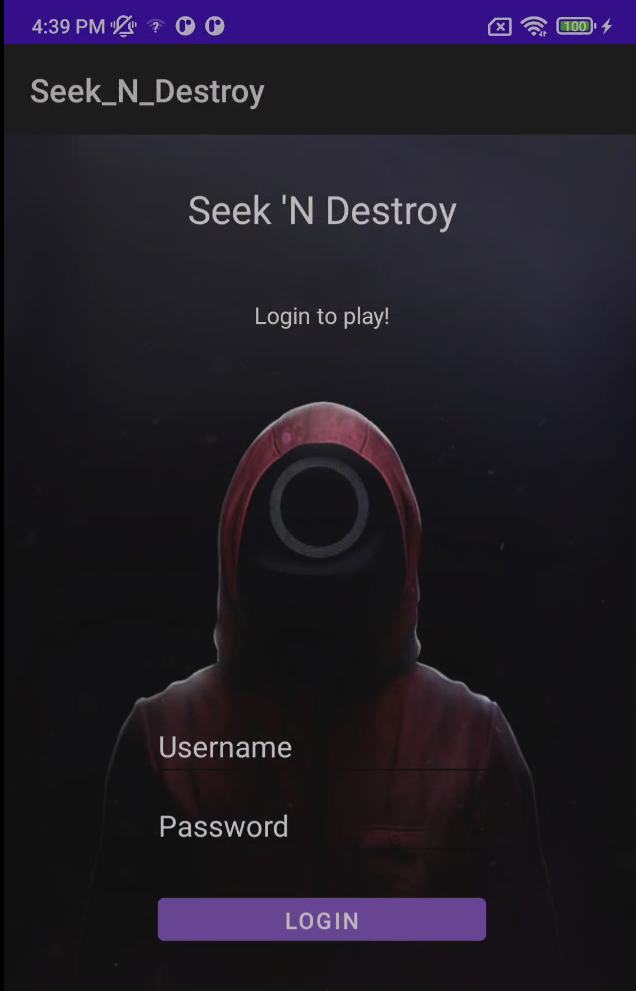 Read more: UniWA 2022 – SeekNDestroy
Read more: UniWA 2022 – SeekNDestroyDescription: James Hetfield has applied a position in Squid Game 2022, but in order to take part into the game, he was asked to bypass the login screen of this app. Help him do this and he might find you a free ticket for the concert. Download: https://lautarovculic.com/my_files/Seek_N_Destroy.apk Install the APK with ADB adb install -r Seek_N_Destroy.apk We can…
-
 Read more: UniWA 2022 – SlapApp
Read more: UniWA 2022 – SlapAppDescription: A heard there is an easy way to make money. All you have to do, is slap 1.000.000.000 times. Download: https://lautarovculic.com/my_files/SlapApp-signed.apk Install the APK with ADB adb install -r SlapApp-signed.apk We can see a button that Slap.We need reach the 1.000.000.000 Let’s analyze the source code with jadx.We have two activities if we look into AndroidManifest.xml file: ShowFlag MainActivity We just need work with MainActivity class.This is the java code public class MainActivity extends…