I recomment read this post first:
First, we need install FRIDA with
pip install frida-tools
Now, we need know the arch of our Android device:
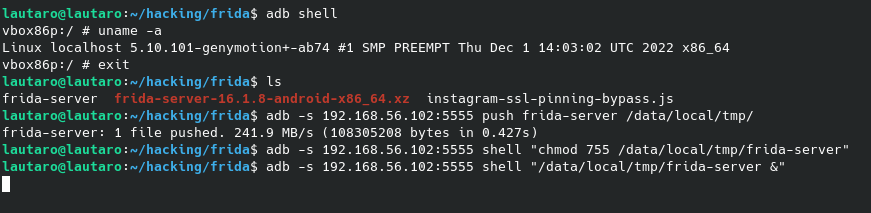
adb shell
If you have more than one device, you can run this command:
adb -s -genymotion device ip-:5555 shell
And, with
uname -a
We get the arch of our Device.
In this case, x86_64
Linux localhost 5.10.101-genymotion+-ab74 #1 SMP PREEMPT Thu Dec 1 14:03:02 UTC 2022 x86_64

We need know that because, we’ll download the necessary frida-server version for our Android device.
In this case, we will download: frida-server-16.1.8-android-x86_64.xz
To our host machine.
Then, unzip the file with
7z x frida-server-16.1.8-android-x86_64.xz
We get the file frida-server-16.1.8-android-x86_64
Rename the file
mv frida-server-16.1.8-android-x86_64 frida-server
And now we will push this file to our Android device:
adb -s 192.168.56.102:5555 push frida-server /data/local/tmp/
We need that frida-server be executable:
adb -s 192.168.56.102:5555 shell "chmod 755 /data/local/tmp/frida-server"
So, execute it:
adb -s 192.168.56.102:5555 shell "/data/local/tmp/frida-server &"
And in our attacker machine we can execute the frida-* suite.
With our Genymotion device running and proxy set, we will download Instagram from playstore.
And we will try login with fake credentials:

Notice that Instagram block the login because the proxy intercept is detected. So, here are a script for bypass these restriction.
But, first we need check if frida is working.
While frida is running in background, we will open another terminal and try execute some command like
frida-ps -U
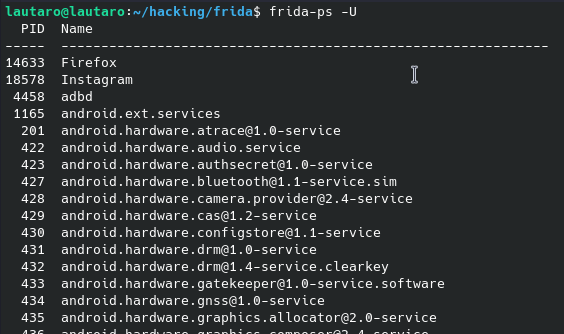
Frida is working, so, here the script:
Download the instagram-ssl-pinning-bypass.js file to our directory, but first, close the Instagram App.
wget https://raw.githubusercontent.com/Eltion/Instagram-SSL-Pinning-Bypass/main/instagram-ssl-pinning-bypass.js
Force stop Instagram App
Now we can execute the following command:
frida -U -l ./instagram-ssl-pinning-bypass.js -f com.instagram.android
And in our Genymotion Android device Instagram will be executed:
Remember keep the proxy enable, so we can intercept the traffic.

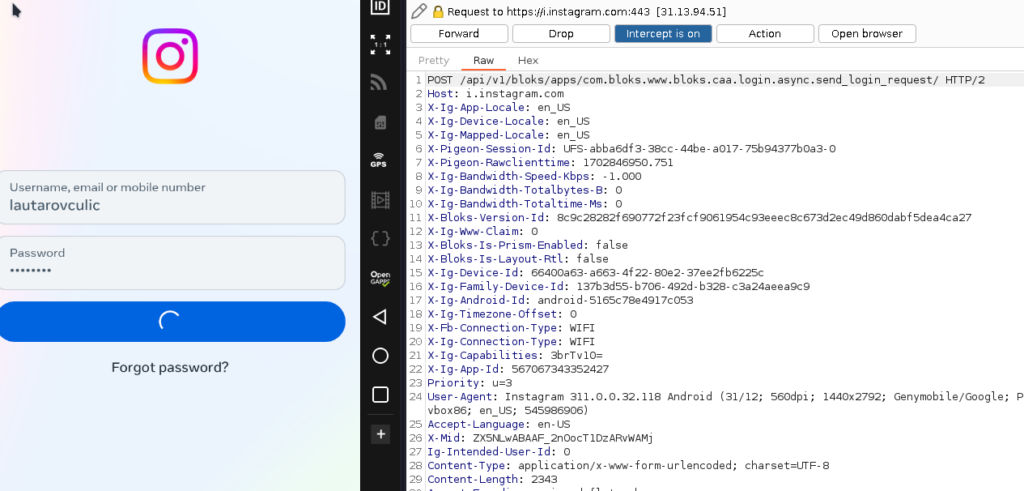

Notice that now we don’t get the same error, just wrong password. So, the bypass has success.
Now we can intercept Instagram app traffic!
I hope you found it useful (:

Leave a Reply