Flags: 4
Difficulty: Easy
Category: Web
Flag 1/4
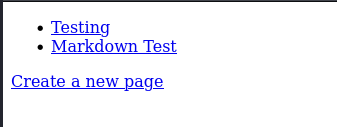
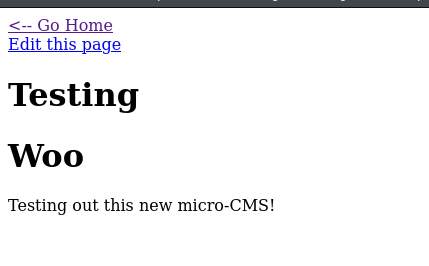
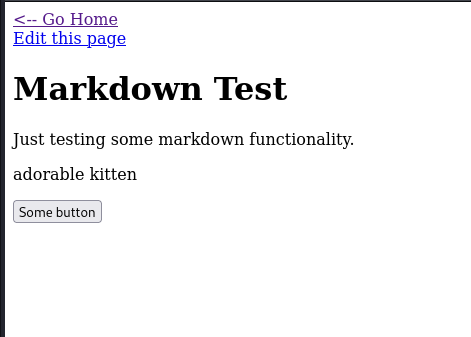
By taking a short tour through the application, we can view and edit a number of ready-made testing pages, and we can also create a page.
On the first page we see that markdown is allowed, but script… no? Let’s try it.
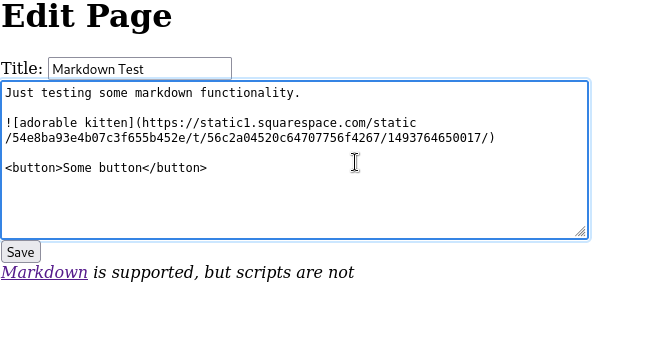
<img decoding="async" src="asd" onerror="alert('xss');">
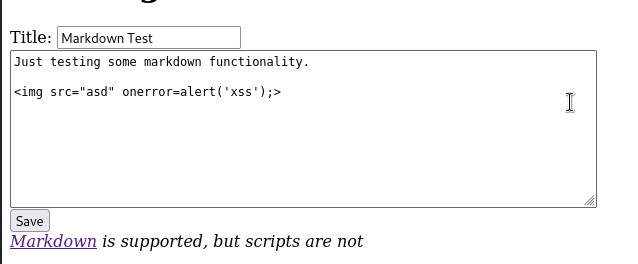
Press the save button and..
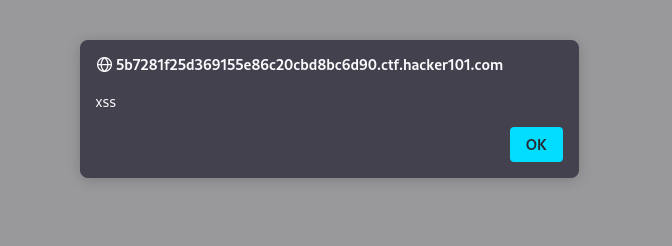
And, if we inspect element, we get the first flag.

Flag 2/4
Now we’ll try to execute a XSS (same script) in the title:
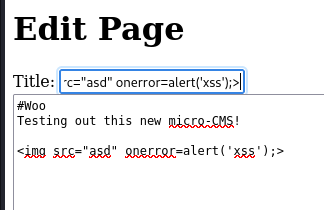
Press the save button and go to “home”. Then, we get the second flag:
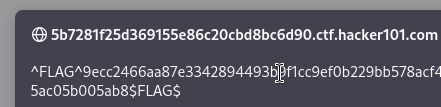
Flag 3/4
Let’s create a test page.
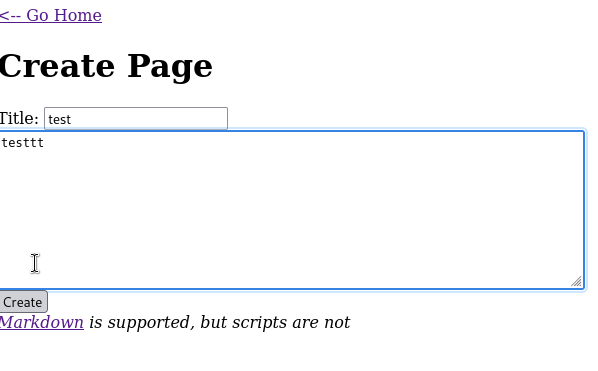
I have seen that a new page has been created with ID 9. If we look carefully, the two previously found are 1 and 2.
Is there another one that is between 2 and 9? Let’s see.
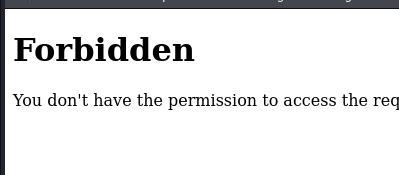
All the ones we saw, give a 404 Not Found error. But, page number 4 gives us a 403 Forbidden. This means that we “cannot” access it, but it does exist.
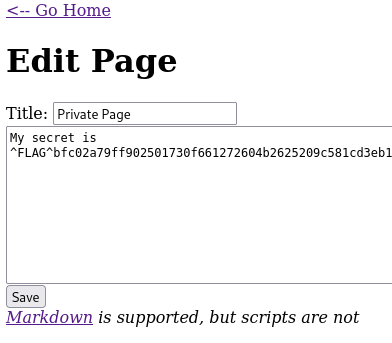
Note that when editing a page, the url is /page/edit/ID. So, what happens if we go to /page/edit/4? Maybe we “can’t” see it, but we can edit it -therefore, we can see the content-. Going to /page/edit/4 we find the third flag!
Flag 4/4
What if after the page ID we were to add a “ ‘ “? Simply to test if it is vulnerable to SQLi. For example: /page/edit/4’
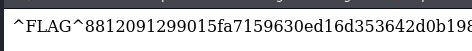
We get the last flag.
I hope you found it useful (:
Leave a Reply