intent
-
 Read more: Mobile Hacking Lab – Post Board
Read more: Mobile Hacking Lab – Post BoardDescription: Welcome to the Android Insecure WebView Challenge! This challenge is designed to delve into the complexities of Android’s WebView component, exploiting a Cross-Site Scripting (XSS) vulnerability to achieve Remote Code Execution (RCE). It’s an immersive opportunity for participants to engage with Android application security, particularly focusing on WebView security issues. Download: https://lautarovculic.com/my_files/postBoard.apkLink:https://www.mobilehackinglab.com/path-player?courseid=lab-webview Install the app with ADB…
-
 Read more: Mobile Hacking Lab – IOT Connect
Read more: Mobile Hacking Lab – IOT ConnectDescription: Welcome to the “IOT Connect” Broadcast Receiver Exploitation Challenge! Immerse yourself in the world of cybersecurity with this hands-on lab. This challenge focuses on exploiting a security flaw related to the broadcast receiver in the “IOT Connect” application, allowing unauthorized users to activate the master switch, which can turn on all connected devices. The goal is…
-
 Read more: Mobile Hacking Lab – Config Editor
Read more: Mobile Hacking Lab – Config EditorDescription: Welcome to the Config Editor Challenge! In this lab, you’ll dive into a realistic situation involving vulnerabilities in a widely-used third-party library. Your objective is to exploit a library-induced vulnerability to achieve RCE on an Android application. Download: https://lautarovculic.com/my_files/configEditor.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-config-editor-rce Install the APP with ADB adb install -r configEditor.apk We can see that there ask for storage permissions.Also, notice that we have two…
-
 Read more: Mobile Hacking Lab – Document Viewer
Read more: Mobile Hacking Lab – Document ViewerDescription: Welcome to the Remote Code Execution (RCE) Challenge! This lab provides a real-world scenario where you’ll explore vulnerabilities in popular software. Your mission is to exploit a path traversal vulnerability combined with dynamic code loading to achieve remote code execution. Download: https://lautarovculic.com/my_files/documentViewer.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-document-viewer-rce Install the APK with ADB adb install -r documentViewer.apk The app appear ask for storage permissions.Let’s inspect the source code with jadx (GUI…
-
 Read more: Mobile Hacking Lab – Guess Me
Read more: Mobile Hacking Lab – Guess MeDescription: Welcome to the “Guess Me” Deep Link Exploitation Challenge! Immerse yourself in the world of cybersecurity with this hands-on lab. This challenge revolves around a fictitious “Guess Me” app, shedding light on a critical security flaw related to deep links that can lead to remote code execution within the app’s framework. Download: https://lautarovculic.com/my_files/guessMe.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-guess-me Install the…
-
 Read more: BSides San Francisco CTF 2017 – flag-receiver
Read more: BSides San Francisco CTF 2017 – flag-receiverDescription: Here is a simple mobile application that will hand you the flag.. if you ask for it the right way.P.S, it is meant to have a blank landing activity 🙂 Use string starting with Flag:Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/flagstore.apk…
-
 Read more: Google CTF 2016 – Ill Intentions
Read more: Google CTF 2016 – Ill IntentionsNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/illintentions.apk Install the apk with adb adb install -r illintentions.apk adb install -r illintentions.apk apktool d illintentions.apk And let’s check the source code with jadx (GUI version)We can see that the package name is com.example.hellojni So, after read the code some minutes, we have the MainActivity public…
-
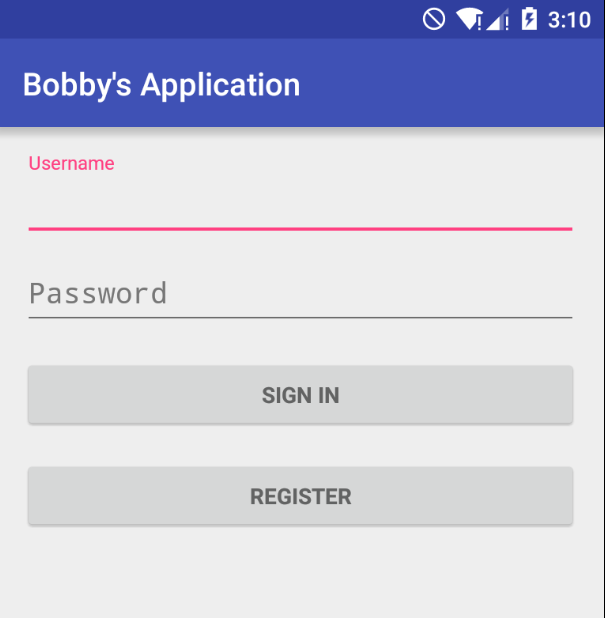 Read more: Google CTF 2016 – Little Bobby application
Read more: Google CTF 2016 – Little Bobby applicationNote: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/BobbyApplication_CTF.apk Install the apk with adb adb install -r BobbyApplication_CTF.apk We can see a login form. Let’s decompile the content with apktool. apktool d BobbyApplication_CTF.apk And let’s check the source code with jadx (GUI version)We can conclude that the package name is bobbytables.ctf.myapplication After create an user “asd” for…