hooking
-
 Read more: Mobile Hacking Lab – NoteKeeper
Read more: Mobile Hacking Lab – NoteKeeperDescription: Welcome to the NoteKeeper Application, where users can create and encode short notes. However, lurking within the app is a critical buffer overflow vulnerability. Your mission is to uncover this vulnerability and exploit it to achieve remote code execution. Download: https://lautarovculic.com/my_files/notekeeper.apkLink: https://www.mobilehackinglab.com/path-player?courseid=lab-notekeeper Install the app with ADB adb install -r notekeeper.apk We can see how this notes app allows…
-
 Read more: CyberTruck Challenge 2019 – Android CTF
Read more: CyberTruck Challenge 2019 – Android CTFDescription: A new mobile remote keyless system “CyberTruck” has been implemented by one of the most well-known car security companies “NowSecure Mobile Vehicles”. The car security company has ensured that the system is entirely uncrackable and therefore attackers will not be able to recover secrets within the mobile application. If you are an experienced Android reverser, then…
-
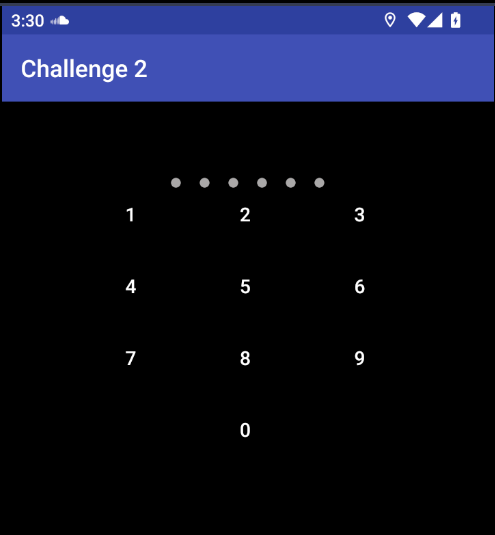 Read more: HackerOne H1-702 – Challenge 2
Read more: HackerOne H1-702 – Challenge 2Description: Looks like this app is all locked up. Think you can figure out the combination? Download APK: https://lautarovculic.com/my_files/challenge2_h1-702.apk Install the apk with adb adb install -r challenge2_h1-702.apk And then, decompile with apktool apktool d challenge2_h1-702.apk We can see a PIN app, which have six numbers combination.So, we can simply try the 1.000.000 combinations (C= 10⁶ = 1.000.000) or look the source code. Open jadx (GUI Version) for analyze the code.The package name is com.hackerone.mobile.challenge2And…
-
 Read more: BSides San Francisco CTF 2017 – flag-receiver
Read more: BSides San Francisco CTF 2017 – flag-receiverDescription: Here is a simple mobile application that will hand you the flag.. if you ask for it the right way.P.S, it is meant to have a blank landing activity 🙂 Use string starting with Flag:Note: For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation Download APK: https://lautarovculic.com/my_files/flagstore.apk…
-
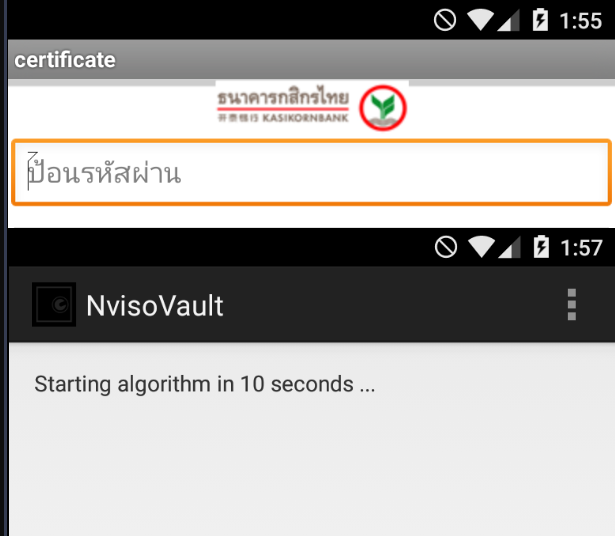 Read more: Cyber Security Challenge 2015 – Reverse That App & Nviso Vault
Read more: Cyber Security Challenge 2015 – Reverse That App & Nviso VaultReverse That App Description: We have intercepted a malicious Android binary, and we need your help analyzing the application! Reports from the wild say that this piece of malware is sending text messages to a premium number, resulting in a huge phone bill for the victims! This needs to stop… Can you identify the mobile…
-
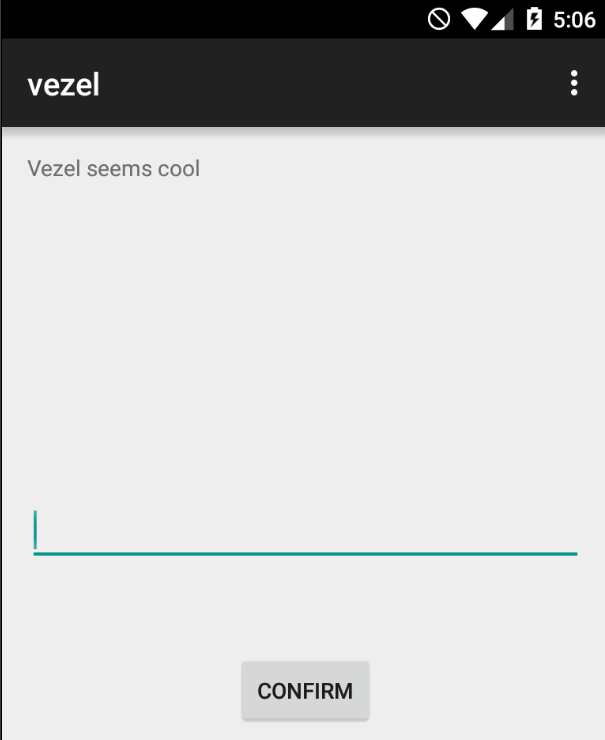 Read more: 0CTF 2015 Quals CTF – Vezel
Read more: 0CTF 2015 Quals CTF – VezelDescriptionEvermars says he is good at repackaging Android applications. For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APKhttps://lautarovculic.com/my_files/vezel.apk Install it with adb adb install -r vezel.apk We can see a text edit and an button.Let’s decompile the apk with apktool apktool d vezel.apk The package name is com.ctf.vezel Let’s inspect the source code with jadx.We just…
-
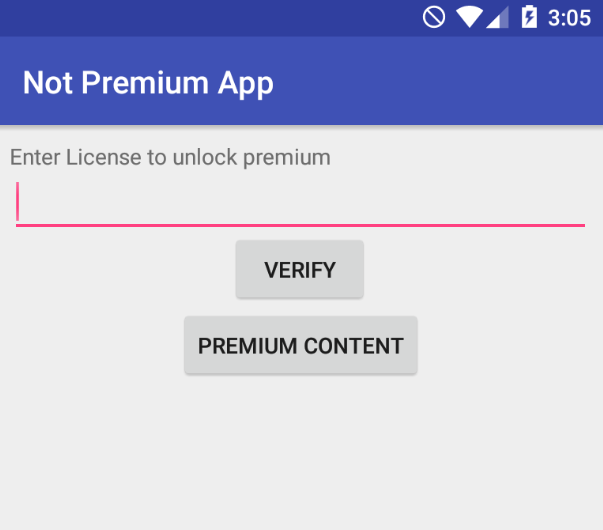 Read more: AHE17: Android Hacking Events 2017 (Why Should I Pay?)
Read more: AHE17: Android Hacking Events 2017 (Why Should I Pay?)For this challenge, probably we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APKhttps://team-sik.org/wp-content/uploads/2017/06/WhyShouldIPay.apk_.zip Install the apk with adb adb install -r WhyShouldIPay.apk And decompile the apk with apktool Load the apk to jadx-gui for see the source codeWe can see in the first activity that we have the VERIFY button, that give us an error.And the PREMIUM CONTENT button, that show us…
-
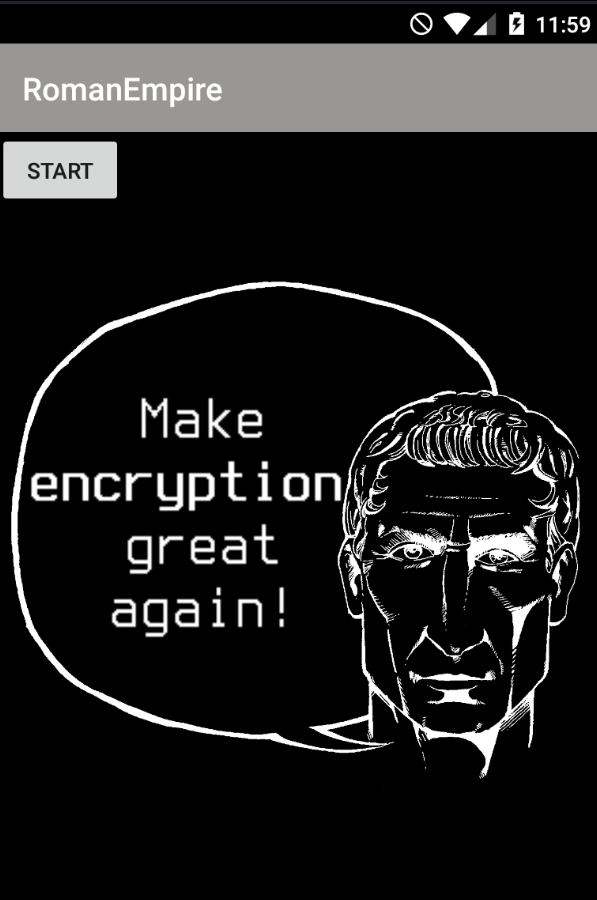 Read more: AHE17: Android Hacking Events 2017 (You Can Hide – But You Cannot Run)
Read more: AHE17: Android Hacking Events 2017 (You Can Hide – But You Cannot Run)For this challenge, probably we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APKhttps://team-sik.org/wp-content/uploads/2017/06/YouCanHideButYouCannotRun.apk_.zip Use apktool for decompile the .apk file apktool d YouCanHideButYouCannotRun.apk And install the .apk with adb adb install -r YouCanHideButYouCannotRun.apk Launching the app we can see that we have a text that talk about encryption and a button. That say Start to Running if we press it. Let’s load the .apk to jadx for…
-
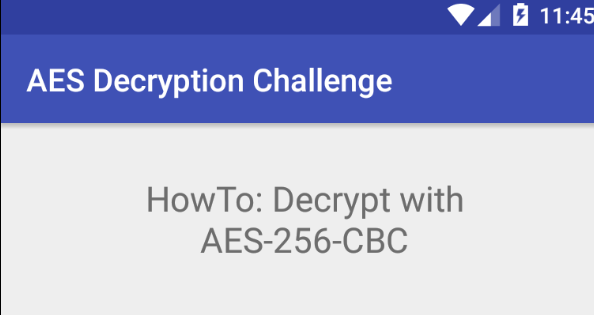 Read more: AHE17: Android Hacking Events 2017 (AES-Decrypt)
Read more: AHE17: Android Hacking Events 2017 (AES-Decrypt)For this challenge, we need install some things into our Android 5.1 device with Genymotion.For example, an ARM Translator.https://github.com/m9rco/Genymotion_ARM_Translation For download the APK https://team-sik.org/wp-content/uploads/2017/06/AES-Decrypt.apk_.zip Now, installing the APK, we can see a button and two text box for decrypt something. Then, let’s take around the code with jadx. Just we need this piece of Java…
-
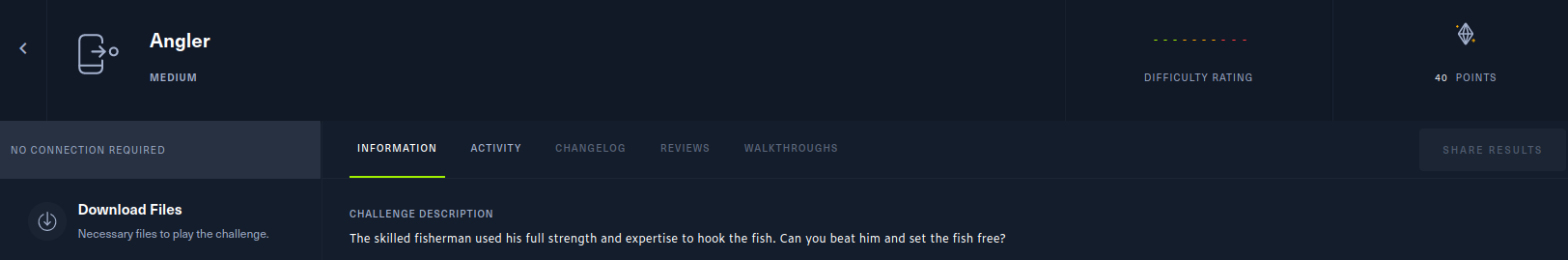 Read more: Angler – Hack The Box – @lautarovculic
Read more: Angler – Hack The Box – @lautarovculicDifficult: Medium Category: Mobile OS: Android Description: The skilled fisherman used his full strength and expertise to hook the fish. Can you beat him and set the fish free? First we’ll download the .apk file. The pass is hackthebox And then decompile with apktool ☝️🤓 apktool d Angler.apk The SDK version is 32, then we…