android
-
 Read more: NahamCon 2024 – Kitty Kitty Bang Bang
Read more: NahamCon 2024 – Kitty Kitty Bang BangDescription: I found a cool android app to play with a cowboy cat! There’s has to be more going on with the app I can’t see on my screen… Download: https://lautarovculic.com/my_files/kittykittybangbang.apk Install the APK with ADB adb install -r kittykittybangbang.apk Let’s decompile it with apktool apktool d kittykittybangbang.apk Also, we can inspect the source code with jadx (GUI version) We can see in the MainActivity…
-
 Read more: NahamCon 2024 – Guitar
Read more: NahamCon 2024 – GuitarDescription: Have you ever wanted to play the guitar on your phone? Here’s a free app, with all guitar strings included for free! Download: https://lautarovculic.com/my_files/guitar.apk Install the APK with ADB adb install -r guitar.apk As the description say, probably the flag are hardcoded in the strings.xml resources.To make the writeup not so short, let’s make an explanation about the strings.xml resources. Android resources are files used to store…
-
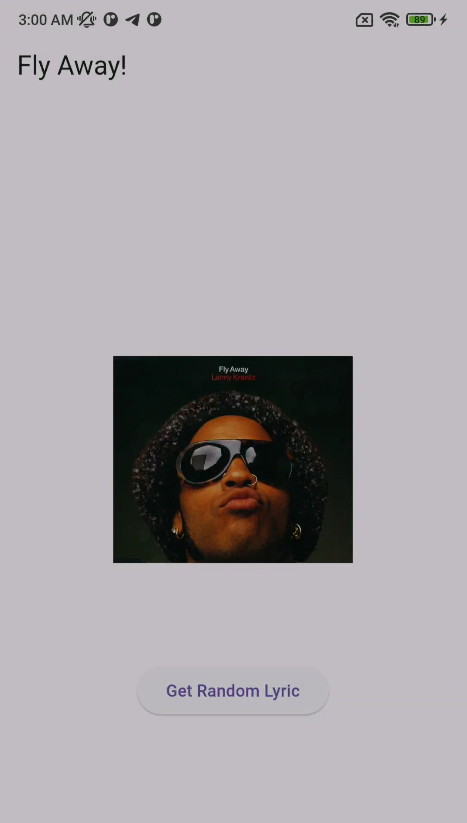 Read more: NahamCon 2024 – Fly Away
Read more: NahamCon 2024 – Fly AwayDescription: Lenny Kravitz lovers, this new app cleverly named “Fly Away!” can give you random lines from one of his most popular songs. Can you figure out how the songs are being sent to the app? Download: https://lautarovculic.com/my_files/flyaway.apk Install the APK with ADB adb install -r flyaway.apk This app was made in reFlutter. You need install it for proceed with…
-
 Read more: NahamCon 2024 – Buggy Jumper
Read more: NahamCon 2024 – Buggy JumperDescription: Buggy Jumper is a new mobile game that can be enjoyable for both gamers and hackers! There’s a lot going on, can you get some of game’s source code to see whats happening behind the scenes? Download: https://lautarovculic.com/my_files/buggyjumper.apk Install the APK with ADB adb install -r buggyjumper.apk Let’s decompile it with apktool apktool d buggyjumper.apk The app has been…
-
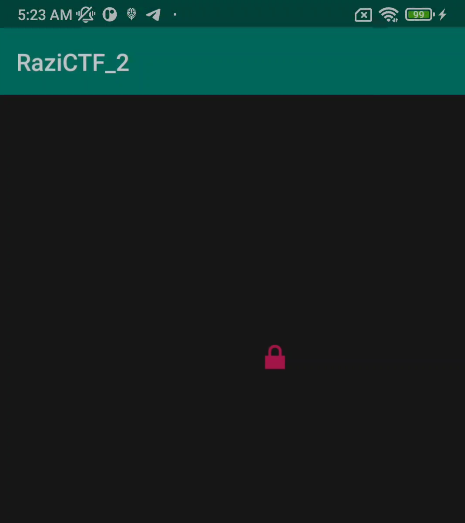 Read more: RaziCTF 2020 – Chasing a lock
Read more: RaziCTF 2020 – Chasing a lockDescription: As locks are so popular many will chase them but why? maybe a flag 🙂 Download: https://lautarovculic.com/my_files/chasingALook.apk Install the APK with ADB adb install -r chasingALook.apk We can see that we need touch the icon 20.000 times.Let’s decompile it with apktool apktool d chasingALook.apk And let’s inspect the source code with jadx (GUI version).The package name is com.example.razictf_2 and there are just one activity, that is MainActivity. But there are some class like a1, a2,…
-
 Read more: CyberTruck Challenge 2019 – Android CTF
Read more: CyberTruck Challenge 2019 – Android CTFDescription: A new mobile remote keyless system “CyberTruck” has been implemented by one of the most well-known car security companies “NowSecure Mobile Vehicles”. The car security company has ensured that the system is entirely uncrackable and therefore attackers will not be able to recover secrets within the mobile application. If you are an experienced Android reverser, then…
-
 Read more: NahamCon CTF 2022 – Click Me!
Read more: NahamCon CTF 2022 – Click Me!Description: I created a cookie clicker application to pass the time. There’s a special prize that I can’t seem to get. Download: https://lautarovculic.com/my_files/click_me.apk Install the apk with ADB adb install -r click_me.apk Decompile it with apktool apktool d click_me.apk Then, let’s open the apk with jadx (GUI version) for check source code.The package name is com.example.clickme. We have the MainActivity, and another class called ActivityMainBinding. But we’ll work with the first…
-
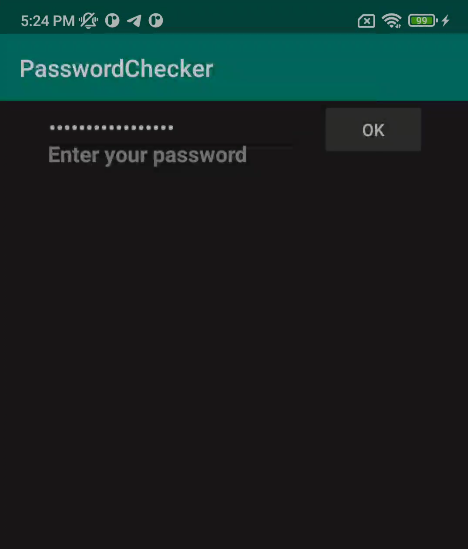 Read more: BSides Canberra 2019 – You Shall Not Pass
Read more: BSides Canberra 2019 – You Shall Not PassDownload: https://lautarovculic.com/my_files/PasswordCheckerAPKs.zip Install the correct APK, depends of your cpu device. You can check with getprop ro.product.cpu.abi In my case, is arm64-v8a.Then, install with ADB adb install -r PasswordChecker-arm64-v8a.apk We can see a simply password checker.That *return true or false*.Let’s inspect the source code with jadx (GUI version).And, decompile it with apktool apktool d PasswordChecker-arm64-v8a.apk We have the package name io.cybears.rev.passwordchecker and just one activity (MainActivity). And just the code that exists for our…
-
 Read more: PwnSec CTF 2024 – Snake
Read more: PwnSec CTF 2024 – SnakeDescription: Make sure to run the mobile application on Android API 28 or less (Android 9 or less).Download content: https://lautarovculic.com/my_files/snake.zip Install the apk with ADB.NOTEIll use an AVD (Android Virtual Device) non-rooted from the Android Studio SDK. adb install -r snake.apk The UI app doesn’t have nothing interesting. But is good notice that the app ask for us about storage permissions.In fact, the AndroidManifest.xml file have Let’s decompile the app…
-
 Read more: PwnSec CTF 2024 – FireStorm
Read more: PwnSec CTF 2024 – FireStormDescription: Descriptions are boring, just solve the challenge meh!Download content: https://lautarovculic.com/my_files/firestorm.zip Install the apk with ADB adb install -r FireStorm.apk Then, let’s decompile it with apktool apktool d FireStorm.apk Open jadx (GUI version) for look the Java code and inspect it.We can see in the MainActivity the following code public String Password() { StringBuilder sb = new StringBuilder(); String string = getString(R.string.Friday_Night); String string2 = getString(R.string.Author); String string3…